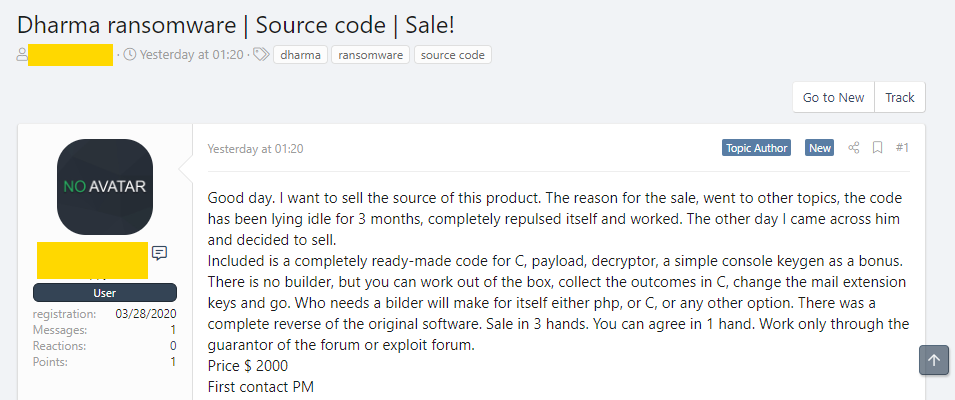
ZDNet reports that the source code for one of the most profitable ransomware of our time, the Dharma ransomware, was put for sale on two hacker forums last weekend. Sources are sold for $2,000.
Let me remind you that this year the FBI called Dharma the second most profitable ransomware in recent years during its report at the conference and RSA. Therefore, from November 2016 to November 2019, ransomware operators received $24 million in ransom from their victims.
The most dangerous ransomware last year, I recall, was called Emotet.
“The current sale of the Dharma code is likely to soon result in a leak to the public. That is, the malware will become available to a wider audience. This, in turn, will lead to a wide distribution of source code among many hack groups, and this will ultimately be followed by a surge of attacks”, – ZDNet quotes an unnamed information security expert.
However, the head of the cyber intelligence department at McAfee told ZDNet that the Dharma code has been circulating among hackers for a long time, and now it just arrived on public forums.
At the same time, the expert expressed the hope that sooner or later the source code will fall into the hands of information security specialists, and this will help to identify the shortcomings of the malware and create decoders.
“Dharma existed since 2016, and the ransomware underlying this malware was originally called CrySiS. It worked on the Ransomware-as-a-Service (RaaS) scheme, that is, other criminals could create their versions of malware to distribute, usually through spam campaigns, exploit kits, or RDP brute force”, – noted ZDNet reporters.
At the end of 2016, a user with the nickname crss7777 posted on the Bleeping Computer forums a link to Pastebin containing master keys from the CrySiS encryptor, which, as experts later established, were genuine. After that, CrySiS ceased to exist, “reborn” as Dharma.
Although Dharma keys suffered the same fate in 2017, this time the ransomware operators did not rebrand and continued to work, eventually turning their RaaS into one of the most popular ransomware on the market.
“So, in recent years, Dharma regularly receives updates. For example, in 2018 and 2019, the criminal underground adapted to new trends and moved from the mass distribution of ransomware through mail spam to targeted attacks on corporate networks. So did the Dharma operators”, – says the ZDNet publication.
It is noted that in the spring of 2019, a new strain of Phobos ransomware appeared on the network, used mainly for targeted attacks. Researchers at Coveware and Malwarebytes have noted that it is almost identical to Dharma. However, at the same time, Dharma did not stop existing and continued to work in parallel with Phobos. For example, Avast experts noticed three new versions of Dharma last week.




