Researchers have identified a critical vulnerability in Shim, a widely-used Linux bootloader. This vulnerability could potentially allow attackers to execute malicious code and gain control of target systems before the kernel is even loaded. This flaw raises significant concerns because it can bypass security mechanisms. These mechanisms are typically enforced by the kernel and the operating system.
What is a Shim Bootloader?
Shim serves as a small, open-source bootloader, crucial for facilitating the Secure Boot process on computers leveraging the Unified Extensible Firmware Interface (UEFI). It is signed with a Microsoft key, which is widely accepted by UEFI motherboards to verify the boot process’s integrity.
The vulnerability, discovered by Microsoft’s Bill Demirkapi, is found in Shim’s handling of HTTP boot operations. It allows for out-of-bounds write operations through manipulated HTTP responses.
Shim RCE Vulnerability Uncovered
The exploitation of CVE-2023-40547 (CVSS score: 9.8) involves creating specially crafted HTTP requests that lead to an out-of-bounds write. This flaw can be exploited in various ways, including remote code execution, network-adjacent, and local attacks. For instance, a remote attacker could intercept HTTP boot traffic through a Man-in-the-Middle attack. Meanwhile, a local attacker could modify EFI variables or use a live Linux USB. These actions could alter the boot process and allow the execution of privileged code.
The ability to execute code before the operating system loads presents a significant threat. It allows attackers to deploy stealthy bootkits that can undermine the security of the compromised system. This level of access grants attackers the ability to bypass traditional security controls and maintain persistent, undetected presence on the affected system.
Red Hat Fixes Shim RCE Flaw
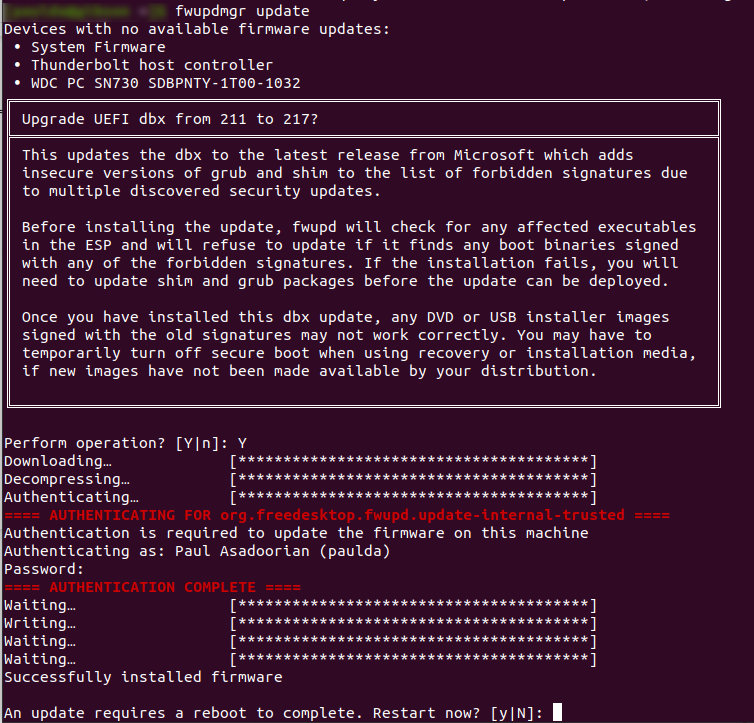
In response to this vulnerability, RedHat issued a fix on December 5, 2023. Users of Shim, including major Linux distributions like Red Hat, Debian, Ubuntu, and SUSE, are urged to update to the latest version of Shim (v15.8), which addresses CVE-2023-40547 and other vulnerabilities. Additionally, users must update the UEFI Secure Boot DBX (revocation list). This update is necessary to prevent the execution of vulnerable Shim versions. It also ensures that the patched version is signed with a valid Microsoft key.
Linux becomes a more and more viable target for different malware families. Sure, it has been predominant in APT attacks for quite some time, as it is a backbone of server infrastructure. Though, an increased number of Linux malware in the form of ransomware, spyware and rootkits appear over the last few years, which is a rather worrying trend. The vulnerability like the one I’ve described above is nothing to mess around with – it may and will be exploited, sooner or later.





