Aqua researchers believe that millions of repositories on GitHub are vulnerable to an attack that allows taking over other people’s repositories and is called RepoJacking. The issue is reportedly affecting the repositories of Google, Lyft, and other major companies.
Let me remind you that we also wrote that Malware in GitHub Repositories Is Spread From Fake Security Company Name, and also that Attackers Can Use GitHub Codespaces to Host and Deliver Malware.
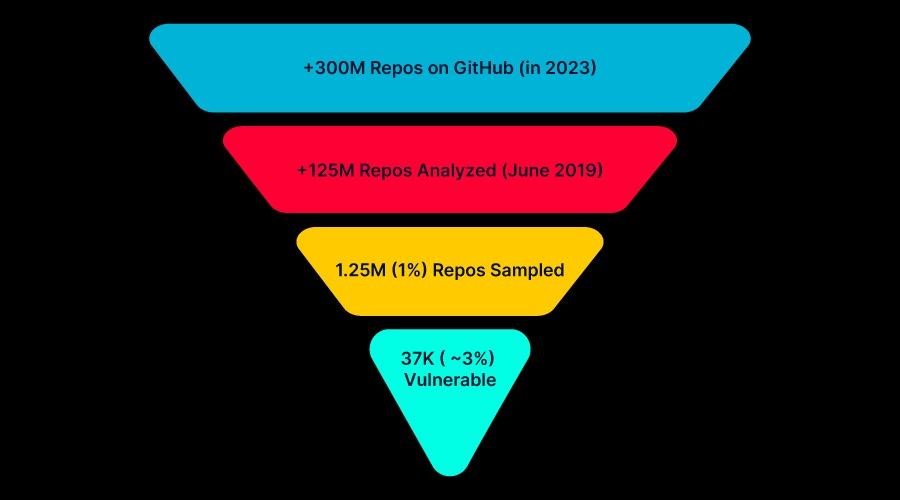
These conclusions were made after analyzing a sample of 1.25 million GitHub repositories, during which experts found that about 2.95% of them are vulnerable to RepoJacking.
Extrapolating this percentage to the entire database of 300 million GitHub repositories, the researchers calculated that the problem affects approximately 9 million projects.
The essence of the RepoJacking attack is simple. The fact is that usernames and repositories change regularly on GitHub (for example, due to the fact that the organization changed the brand name). When this happens, a special redirect is created to avoid breaking dependencies for projects that use code from repositories that have changed their name. However, if someone registers the old name, this redirect becomes invalid.
Thus, RepoJacking is an attack in which an attacker registers a username and creates a repository that was previously used by some organization, but has changed its name. As a result, any project and code that relies on a dependency on the attacked project will interact with a repository that the attacker controls and that may contain malware.
The researchers explain that GitHub is aware of this issue and there are a number of defense mechanisms in place to protect against RepoJacking. However, according to experts, these security solutions are not very reliable and can be easily bypassed.
For example, GitHub only protects very popular projects, however, they may have a dependency on a less popular and vulnerable repository that is not protected by GitHub. As a result, compromise will affect the entire supply chain.
In addition, GitHub protects repositories that had more than 100 clones in the week before the name change (indicative of malicious activity). But such protection does not apply to projects that have become popular after the renaming or after the transfer of ownership.
To demonstrate the danger of this problem, Aqua analysts searched for vulnerable repositories from well-known organizations and found striking examples in repositories operated by Google and Lyft.
In Google’s case, a readme file was found containing instructions for the rather popular Mathsteps project. The file pointed to a repository owned by Socratic, which Google acquired in 2018 and no longer exists. In fact, an attacker can clone this repository, and users, following the instructions in the readme, can download malicious code from the hacker’s repository.
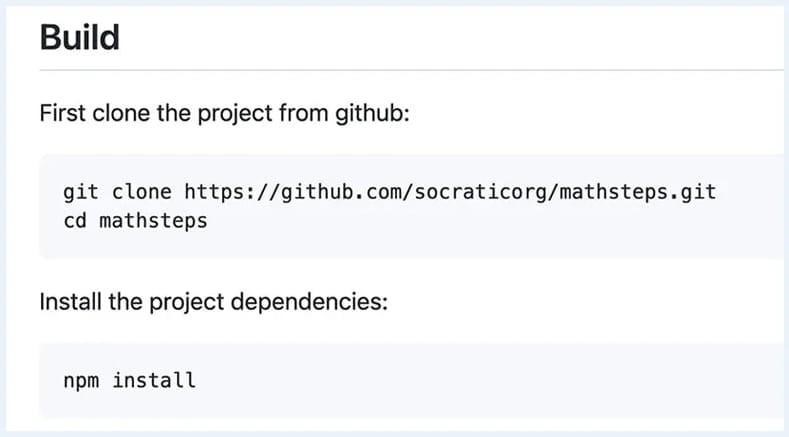
Also, since the instructions include npm install for a dependency, an attacker will be able to execute arbitrary code on unsuspecting users’ devices.
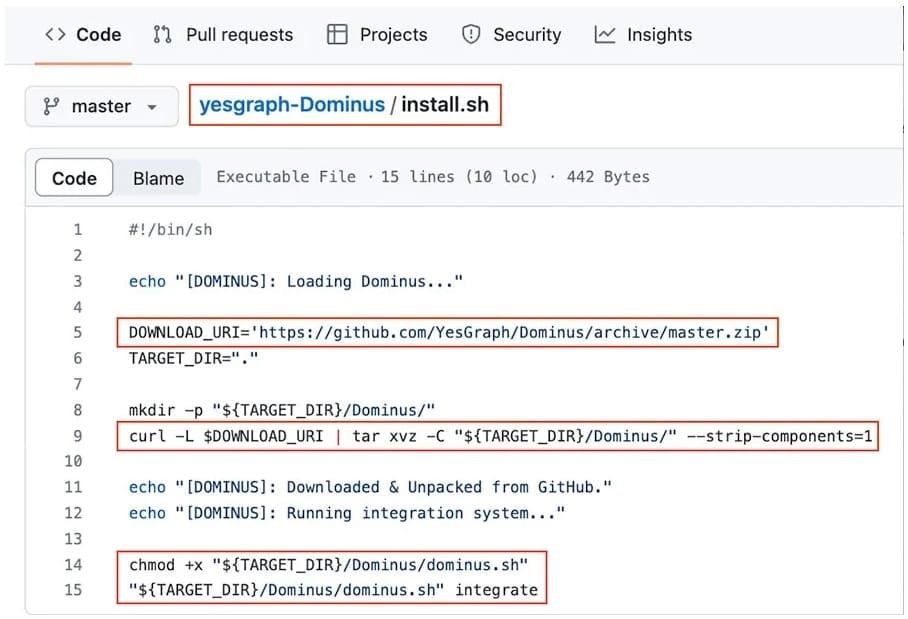
As for Lyft, in this case, the attack may be automated, as the researchers found an installation script in the company’s repository that extracts a ZIP archive from another repository vulnerable to RepoJacking.
So, an attacker who registers a new username and a repository with the correct name (in this case, YesGraph and Dominus) can inject their code to anyone who executes the Lyft install.sh script.
The experts conclude that RepoJacking is unfortunately quite difficult to prevent, and such an attack can have serious consequences for organizations and users. In conclusion, Aqua researchers advise project owners to minimize the resources they pull from external repositories.
The media also reported that GitHub says it takes years to fix vulnerabilities in some ecosystems.