Trend Micro reports that the GitHub Codespaces cloud development environment, available to the public use since November 2022, can be used to store and deliver malware, as well as malicious scripts.
Let me remind you that we also talked about Hackers Bypass CAPTCHA on GitHub to Automate Account Creation, and also that Hackers compromised Slack private GitHub repositories.
And also, the media reported that Many Repositories on GitHub Are Cloned and Distribute Malware.
In their report, the researchers demonstrate how easy it is to set up GitHub Codespaces to act as a web server to distribute malicious content while avoiding detection as the traffic originates from Microsoft servers.
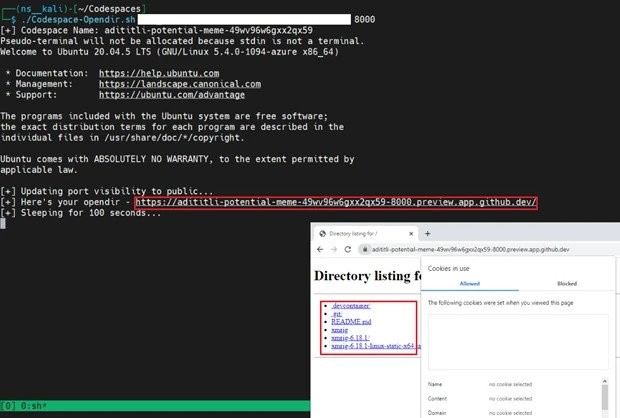
The fact is that GitHub Codespaces allows developers to share forwarded ports from a virtual machine both privately and publicly for the purpose of real-time collaboration.
When forwarding ports on a virtual machine, Codespaces will generate a URL to access the application running on that port, which can be configured as private or public. Access to the private port URL will require authentication in the form of a token or cookies. However, the public port will be available to anyone without authentication if they know the URL.
Trend Micro analysts write that attackers can easily use this functionality to place malicious content on the platform. For example, an attacker can run a simple Python web server, upload malicious scripts or malware into their Codespace, open a web server port on a virtual machine and make it public.
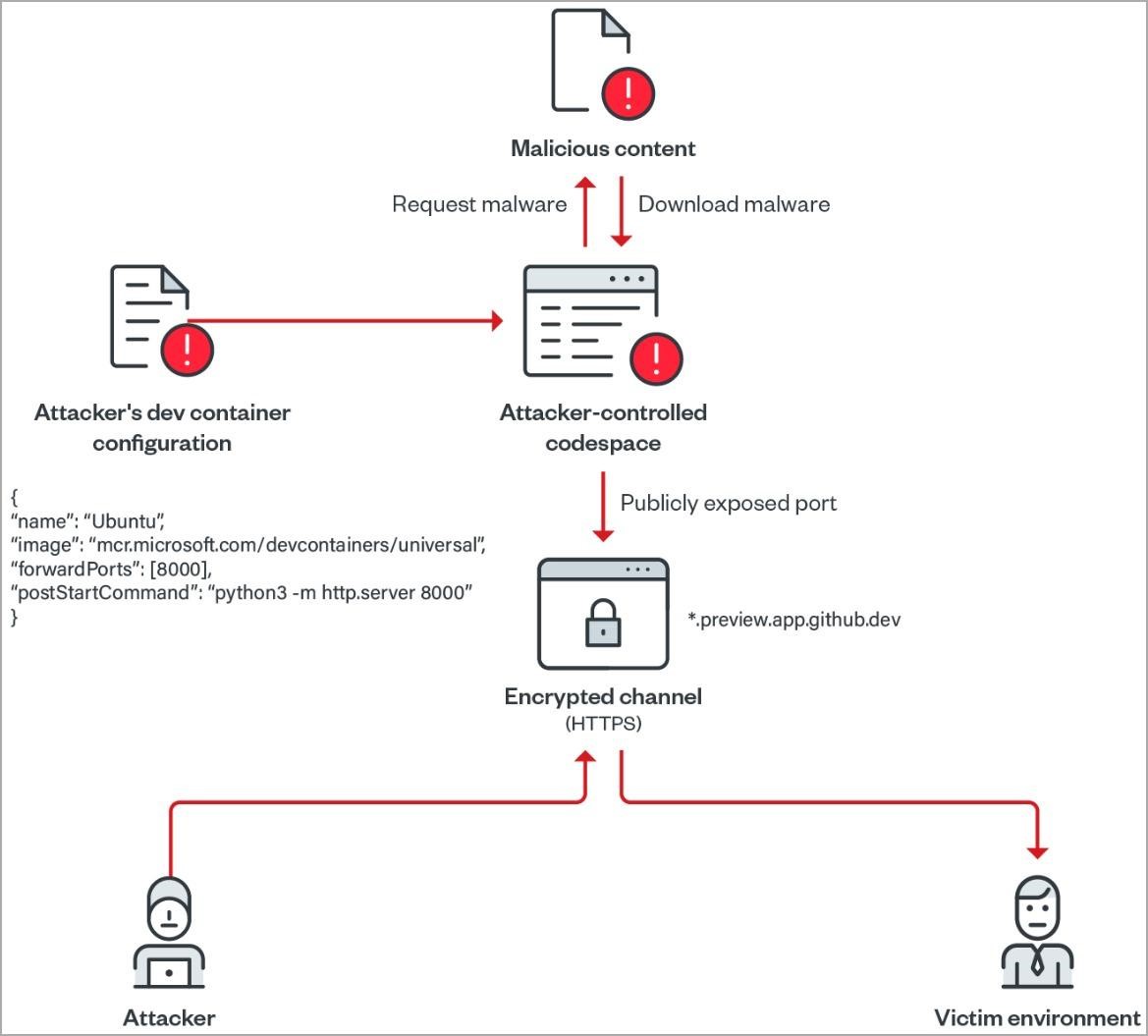
The generated URL can then be used to access hosted files that could be used in phishing campaigns or become malicious executables downloaded by other malware. This is how attackers commonly abuse other well-known services, including Google Cloud, Amazon AWS, and Microsoft Azure.
Also, Trend Micro analysts write that an attacker can create a simple script to create a Codespace with a public port and use it to host malicious content, and set it to automatically self-delete after the URL has been accessed.
So far, no cases of abuse of GitHub Codespaces have been found in this way, but analysts are confident that attackers are unlikely to miss this opportunity.




