In the intricate landscape of cybersecurity, comprehending the various forms of malware is crucial. This article offers an in-depth look at the most pervasive malware types, from Loaders to Keyloggers. We’ll explore their mechanisms, impacts, and how they compromise digital security, providing you with the knowledge to better safeguard against these ever-evolving cyber threats.
Let’s start by understanding what malware is. Malware is malicious software that can harm your computer and data. Some potentially unwanted or malicious applications, also, may not show any signs of danger and are rated by anti-malware vendors based on their own opinions. Hack tools can also considered malicious because someone can use them to hack computer networks. In addition, Antivirus software often blocks them as if they were active viruses.
Loader
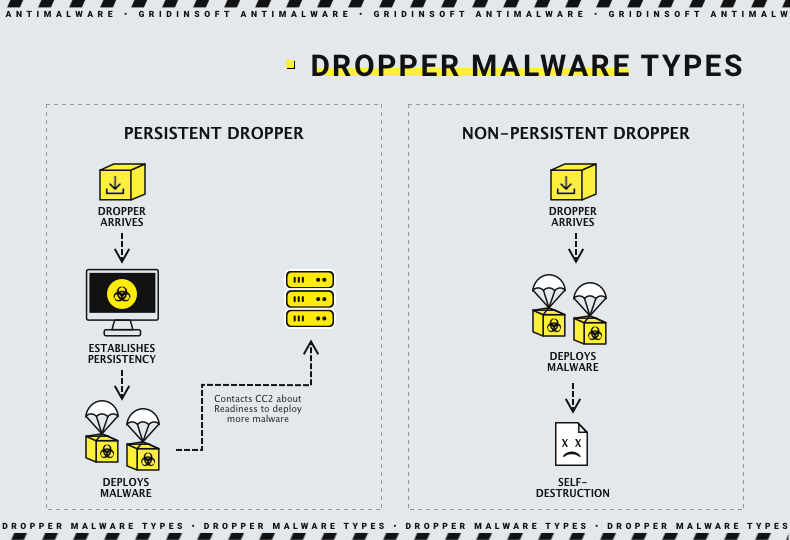
Loader malware, also known as downloader or dropper, is a type of malicious software designed to deliver other types of malware to the targeted system. These droppers often have the capability to form botnets, which are networks of computers that a single command center can control. Once activated, these botnets can deploy any kind of malware, ranging from adware and browser hijackers to spyware and ransomware.
However, for the droppers to work, they must first infiltrate the targeted system. Email spam is one of the most common methods of spreading this malware. However, this malware is usually targeted towards individual users rather than corporate networks, so methods like software cracks and adware are also used.
Loader (droppers) examples in 2024
- Amadey
- BatLoader
- BazarLoader
- TrickBot
- QakBot
Stealer
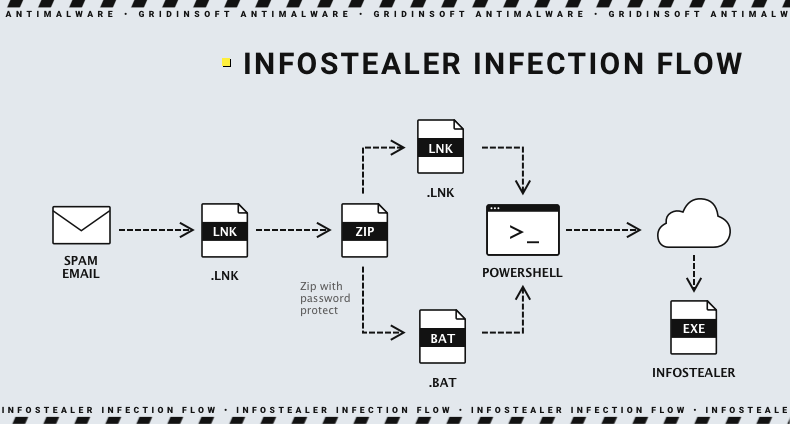
Stealer malware, often referred to as “information stealers,” is a type of malicious software designed to extract sensitive information from infected systems. This information can include a wide range of data such as login credentials, financial information, personal identification details, and more.
Key Characteristics of Stealer Malware
| Function | Description |
| Data Extraction | Stealers are programmed to find and exfiltrate specific types of data, such as passwords, browser history, cookies, system information, and files. |
| Stealthy Operation | They often operate quietly in the background, trying to avoid detection by both users and security software. |
| Automated Data Transmission | Once the desired information is gathered, it’s typically sent back to a command and control server controlled by the attacker. |
| Versatility | Stealers can be standalone malware or a module within larger, multi-functional malware. |
Common Types of Stealer Malware
| Type | Description |
| Password Stealers | Specifically designed to extract passwords stored on a computer or transmitted over a network. |
| Banking Trojans | A type of stealer malware that specifically targets financial information, like banking login credentials. |
| Keyloggers | Capture and record keystrokes, allowing attackers to gather data entered by the user, such as passwords and other sensitive information. |
| Browser Session Hijackers | Extract data from web browsers, including session cookies, which can allow attackers to impersonate the victim on various websites. |
| Clipboard Hijackers | Monitor the system’s clipboard for sensitive information like cryptocurrency wallet addresses. |
| Form Grabbers | Intercept data entered into forms on web pages, often used to steal credit card details and login information. |
Remote Access Trojan (RAT)
A Remote Access Trojan (RAT) is a type of malware that allows a hacker to control a victim’s computer remotely. This control is often comprehensive and can steal information, spy on the user’s activities, or distribute other malware. RATs are particularly dangerous because they provide the attacker with unauthorized access to the victim’s system, often without the user’s knowledge.
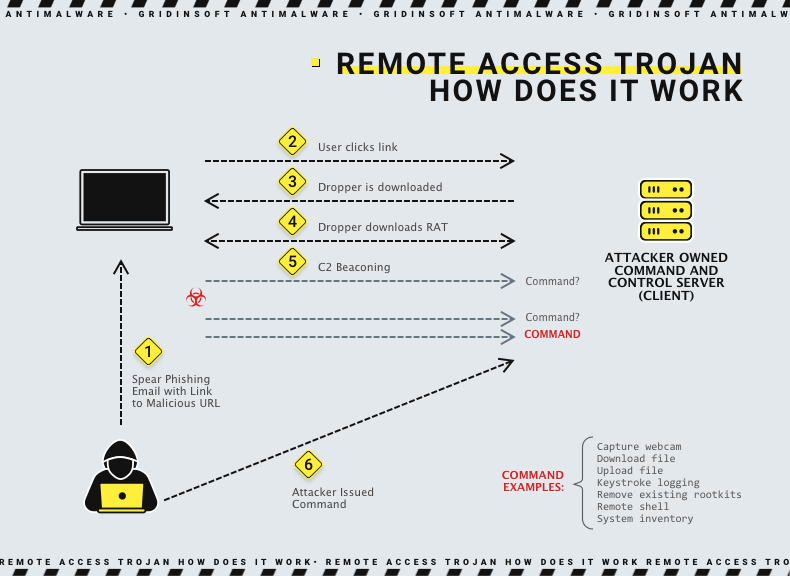
Characteristics of RATs
| Function | Description |
| Remote Control | The primary feature of a RAT is its ability to provide the attacker with remote control over the infected system. |
| Stealthiness | RATs usually operate in a stealth mode to avoid detection by users and antivirus programs. |
| Data Exfiltration | They can be used to steal sensitive data, including passwords, financial information, and personal files. |
| Browser Session Hijackers | Extract data from web browsers, including session cookies, which can allow attackers to impersonate the victim on various websites. |
| System Manipulation | They can alter system settings, modify files, and install additional software, including other malware. |
RAT Malware Types
| Type | Description |
| Generic RATs | These are RATs that provide broad remote control capabilities, suitable for various malicious activities. |
| Commercial RATs | Marketed as legitimate remote administration tools, these can be used maliciously if they fall into the wrong hands. Examples include DarkComet and NetBus. |
| Custom RATs | Created by attackers for specific campaigns, often used in targeted attacks and advanced persistent threats (APTs). |
| Banking RATs | Specialized in financial fraud, these RATs are designed to steal banking credentials and credit card information. |
| Mobile RATs | Targeting mobile devices, also, these RATs can access messages, call logs, and other sensitive data stored on smartphones. |
Ransomware
Ransomware is a malicious program that injects into your computer and encrypts your files. Once your files are encrypted, the attacker demands a ransom payment to restore access to your data. Some ransomware may also threaten to delete your files or expose sensitive information if the ransom is not paid. Although the first threat is often false, the second threat can be real as ransomware is frequently spread alongside spyware or stealers.
Characteristics of Ransomware
| Function | Description |
| Encryption | The most common tactic, where ransomware encrypts the victim’s files, making them inaccessible without a decryption key. |
| Demand for Ransom | Victims are typically demanded to pay a ransom, often in cryptocurrencies, to receive a decryption key. |
| Time Limits | Many ransomware variants include a countdown timer, threatening to delete the decryption key or increase the ransom amount if not paid within the time frame. |
| Distribution Methods | Commonly spread through phishing emails, malicious downloads, and exploiting vulnerabilities in software. |
| Anonymity of Transactions | Ransoms are usually demanded in cryptocurrencies to maintain the anonymity of the attackers. |
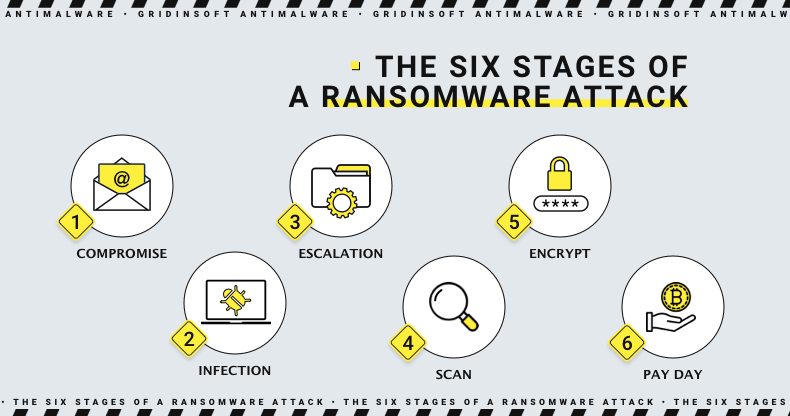
Types of Ransomware
| Type | Description |
| Crypto Ransomware | Encrypts valuable files on a computer or network. Example: WannaCry, which spread globally in 2017, encrypting files and demanding Bitcoin as ransom. |
| Locker Ransomware | Locks the victim out of their operating system, making it impossible to access their desktop, apps, and files. Example: the early ‘police-themed’ ransomware which falsely claimed that the user had committed a crime and needed to pay a fine. |
| Scareware | Fake security software that claims to have found issues on the user’s computer and demands payment to fix them. While not true ransomware, it uses similar intimidation tactics. |
| Doxware or Leakware | Threatens to publish sensitive data stolen from the victim’s computer unless a ransom is paid. |
| RaaS (Ransomware-as-a-Service) | The ransomware is created by a developer and distributed by affiliates who share a percentage of the proceeds with the developer. Example: REvil/Sodinokibi. |
| Double Extortion Ransomware | Not only encrypts data but also steals it. The attackers threaten to release the data publicly if the ransom isn’t paid. Example: Maze ransomware. |
| Mobile Ransomware | Specifically targets mobile devices, often locking the device or encrypting files stored on it. |
Trojan
Trojan virus is a type of malicious software that disguises itself as a legitimate program or file, tricking users into downloading and installing it. Once activated, a Trojan can perform a variety of harmful actions on the victim’s computer. Also, trojans can take various forms like applications, documents, and scripts, exploiting the system and performing actions like disabling security software, modifying system settings, and stealing personal information. In conclusion, they are typically spread through deceptive methods like phishing emails, fake software updates, or illegitimate tools.
Common Trojan Virus Types
| Type | Description |
| Trojan-Downloader | It disables security software like Microsoft Defender, connects to a command server, and can inject other viruses into the system, making it vulnerable to further attacks. |
| Trojan-Spy and Trojan-Stealer | These Trojans are designed to spy on the entire system or steal specific files or passwords. They can modify deep system settings to upload telemetry data, providing attackers with detailed information about the user’s activities and system configurations. |
| Trojan-Ransom (Ransomware) | This type disguises itself as a legitimate application and encrypts the user’s files, demanding a ransom for their decryption. It can disable security settings and block access to removal guides. |
| Trojan-CoinMiner | This type uses the victim’s hardware for cryptocurrency mining, which can lead to hardware overloads and failures. |
| Trojan with Adware Functions | Some Trojans can bombard the user with ads, opening advertising pages autonomously. These are often classified as potentially unwanted programs (PUPs). |
Installer malware
Installer malware is a type of unwanted software that disguises itself as legitimate installation programs for applications or updates. Also, these deceptive installers trick users into downloading and executing them, appearing to be trustworthy software installers. Once the user allows it to run, this malware will download and run numerous unwanted programs. Therefore, installers are sometimes used to monetize free or cracked software.
Types of Installer Malware include
| Type | Description |
| Bundled Malware Installers | These installers come with legitimate software but also include hidden malicious programs. They may install adware, spyware, or other unwanted software without the user’s knowledge. |
| Fake Software Update Installers | Masquerading as updates for popular software, these installers actually contain malware. They exploit the user’s trust in the software and the routine nature of updates to infiltrate systems. |
| Drive-by Download Installers | These are automatically downloaded to a user’s system without their consent when they visit a compromised or malicious website. The installation often occurs silently, without the user’s knowledge. |
Keylogger
A keylogger is a type of surveillance technology used to record keystrokes made by a user. The purpose of keyloggers can vary from benign to malicious, depending on their use. They are often used in corporate and legal environments to track employees’ and users’ activities for various reasons, such as security or compliance. However, in the context of malware, keyloggers are used to steal sensitive information like passwords, financial data, and personal messages.
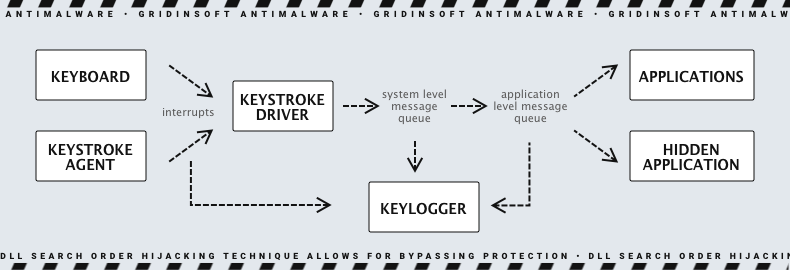
Types of Keyloggers
| Type | Description |
| Hardware Keyloggers | Physical devices attached to a keyboard or embedded in hardware to capture keystrokes. They are hard to detect without physical inspection. |
| Software Keyloggers | Malicious software that records keystrokes. They can be part of a larger malware package or standalone applications. Software keyloggers are more common and can be installed via phishing, malicious downloads, or by exploiting system vulnerabilities. |
| Kernel-based Keyloggers | Operate at the kernel level of the operating system, giving them high-level access to monitor keystrokes. They are difficult to detect and can bypass security software. |
| Browser Keyloggers | Specialized software designed to capture keystrokes only in web browsers. They are often used to steal login credentials and financial information entered on websites. |
| API-based Keyloggers | Use application programming interface (API) calls to monitor and record keystrokes. They are relatively common due to their ease of implementation. |
| Form Grabbing-based Keyloggers | Designed to record form data submitted in web browsers, capturing information before it’s encrypted by secure websites. |
How can I protect my computer from malware?
Protecting your computer from malware involves a combination of software solutions, safe computing practices, and regular maintenance. Although there are basic tips for protecting yourself from malware, such as: regular updates, strong passwords, secure networks, limit software installation. But Anti-malware tools are highly effective against various types of viruses.
You can be careful for a long time, but eventually you may end up downloading malware to your computer without realizing it. We recommend GridinSoft Anti-Malware, which can save you the stress and financial cost of fighting malware.