A new DLL (Dynamic Link Library) Search Order Hijacking variant emerged. This method capitalizes on executables in the trusted WinSxS folder of Windows 10 and 11, allowing threat actors to execute malicious code without needing high privileges.
How Does DLL Search Order Hijacking Work?
Researchers detect a novel DLL search order hijacking variant. It leverages the way Windows loads DLLs and executables. This technique exploits applications that don’t specify the full path of required DLLs, using a predefined search order. Attackers, in turn, manipulate this feature by placing malicious DLLs in prioritized directories. This technique is not new, and it is known that some TAs have used it during cyberattacks. There were quite a few of them:
- APT41
- Aquatic Panda
- BackdoorDiplomacy
- Evilnum
- menuPass
- RTM
- Threat Group-3390
- Tonto Team
- Whitefly
By forcing trusted apps to execute malicious DLLs, threat actors can achieve unauthorized access, execute arbitrary code. At the same time, their activities remain concealed by legit processes.
Proof of Concept
Security experts conducted a Proof of Concept (PoC) to demonstrate this. The team used Process Monitor to identify potential vulnerabilities. They set filters for outcomes like “PATH NOT FOUND” and “NAME NOT FOUND,” specifically targeting the “NOT_A_SYSTEM_FOLDER_MS” directory, a custom folder on the desktop used for research purposes.
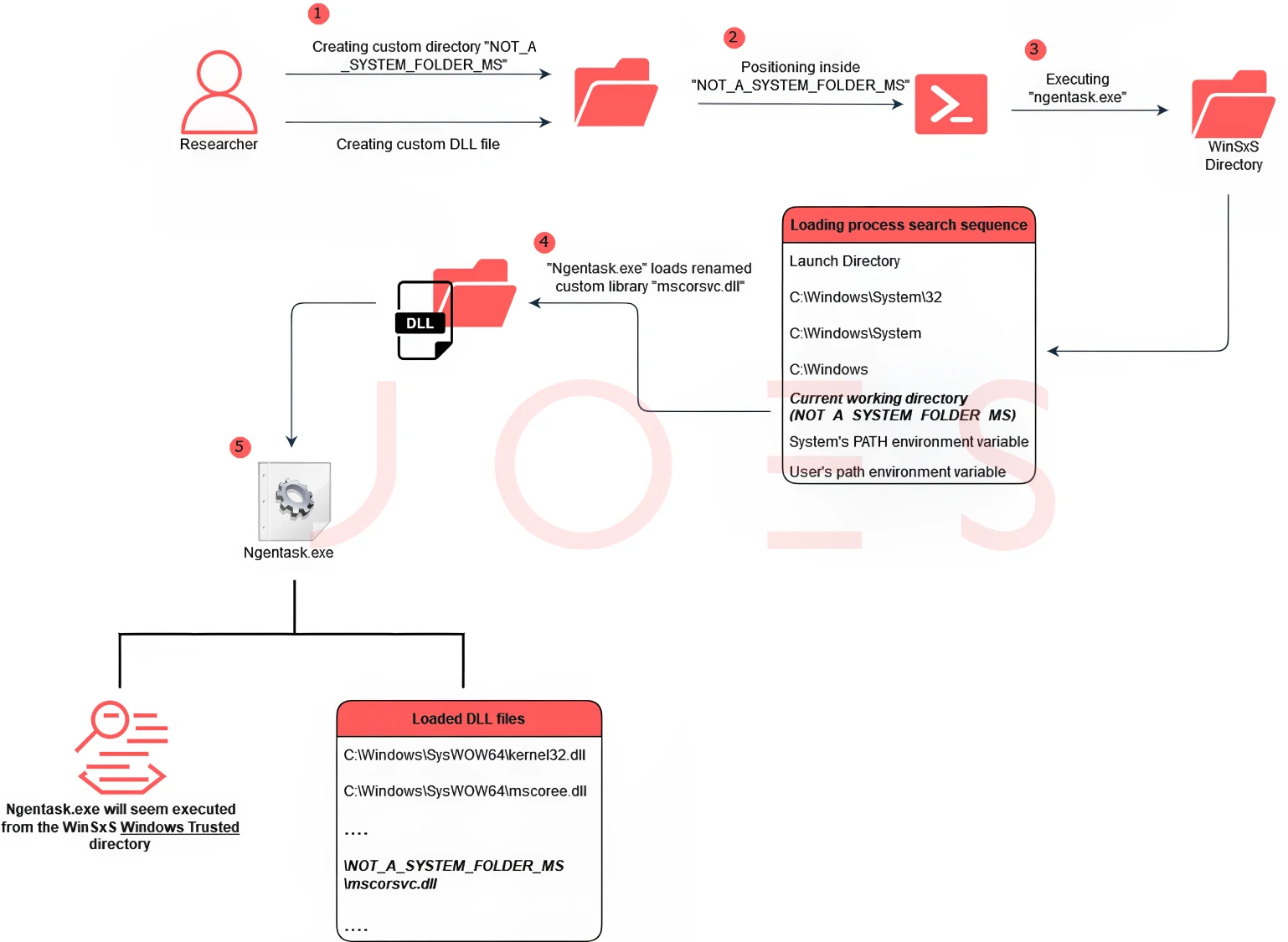
Next, they placed a custom DLL to be injected using the hijacking technique alongside an executable designed to execute and monitor binaries in the WinSxS folder. By running their custom tool, researchers identified binaries like “ngentask.exe” and “aspnet_wp.exe” in the WinSxS folder that attempted to search for their respective DLLs in the “NOT_A_SYSTEM_FOLDER_MS” directory.
The PoC involved launching a command line from a shell using “NOT_A_SYSTEM_FOLDER_MS” as the current directory. This action led the targeted binary to execute the researchers’ custom DLL instead of the legitimate one. The team renamed their custom DLL to match the expected name of the legitimate DLL file. They confirmed the successful injection of their custom DLL into the “ngentask.exe” process using Process Explorer.
Windows SxS, DLL Loading – What Are They?
The Windows WinSxS folder (short for Windows Side by Side) is a critical component of Windows. It is located at C:\Windows\WinSxS, and its primary function is to store multiple versions of important system files and Dynamic Link Libraries (DLLs). This capability is essential for maintaining system compatibility and integrity, mainly when updating Windows.
However, this trust is what the new DLL hijacking technique exploits by targeting files within the WinSxS folder to execute malicious code, thus bypassing traditional security measures. In normal operations, applications use a predefined search order to locate and load the necessary DLLs. However, this process becomes vulnerable when applications do not specify the full path to these DLLs. Attackers exploit this by placing malicious DLLs in directories that are searched before the legitimate ones, leading the application to load and execute malicious code inadvertently.
Detection Opportunities and Recommendations
To address this exploitation method, experts suggest focusing on parent process analysis. This includes looking for unusual processes invoking binaries from the WinSxS folder and monitoring the activities of these binaries, especially their network communications and file operations. This approach can help identify any abnormal behavior indicative of an ongoing attack.
In addition, it’s crucial to use comprehensive security measures like anti-malware solutions and firewalls. Antivirus software can detect and neutralize many types of malware, including those that might be introduced via DLL hijacking. On the other hand, firewalls help monitor and control incoming and outgoing network traffic.