Microsoft reportedly disabled MSIX installer protocol in Windows, due to its exploitation in real-world cyberattacks. Hackers found a way to misuse the protocol to install malicious software, bypassing anti-malware software detection.
MSIX Installer Protocol Exploited
The emergence of a malware kit market, exploiting the MSIX file format and ms-app installer protocol is nothing new. However, in this case, the kit, sold as a service, enables attackers to leverage the vulnerabilities within the protocol to distribute malware, including ransomware.
As a reminder, MSIX is a file packaging format designed specifically for Windows 10. It was based on the concept of XML manifest files. In these files, developers can describe how the deployment process works, what files are needed, and where they can be obtained. The root of the problem is that files packaged with MSIX can be delivered to the system over the Internet via ms-appinstaller. That, in turn, makes it possible to create links format ms-appinstaller:?source=//website.com/file.appx, invoking malware installation in such a way.
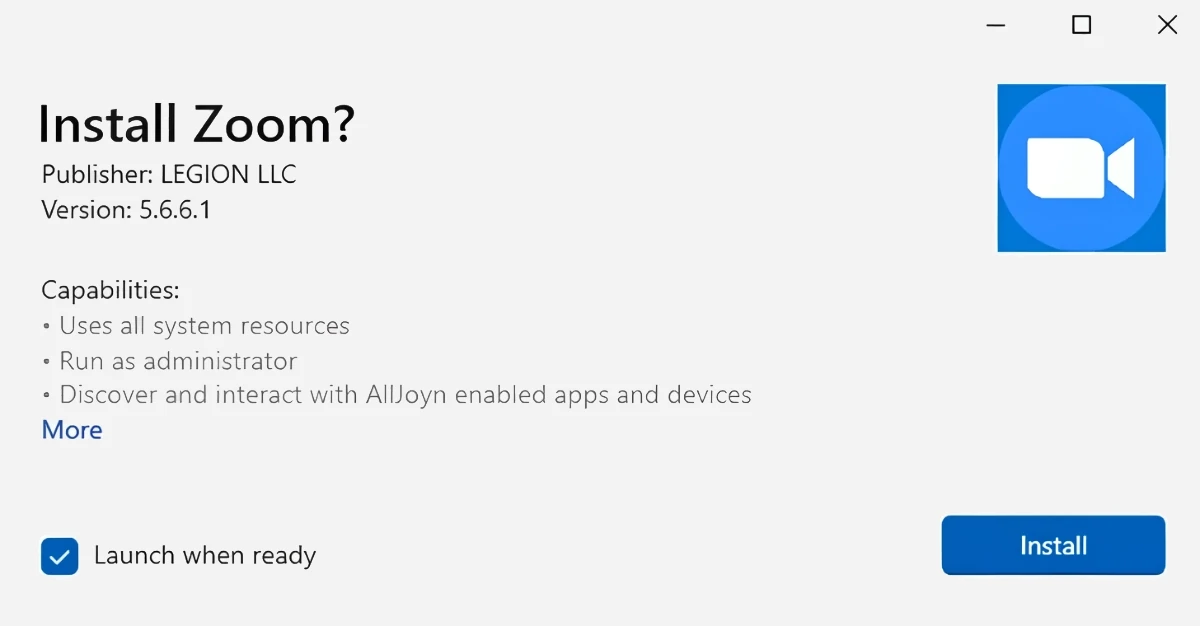
As for modus operandi, crooks have effectively utilized signed malicious MSIX application packages camouflaged as legitimate software to infiltrate systems. These packages are spread through various channels. In this case, it’s Microsoft Teams and deceptive advertisements on popular search engines. This strategy allows the attackers to bypass traditional security measures, such as Microsoft Defender SmartScreen and browser download warnings, making the attacks more difficult to detect and prevent.
Multiple hacking groups have been found to exploit the App Installer service since mid-November 2023. These groups use various techniques to distribute malicious software, including fake installers and landing pages. Some notable groups include Storm-0569, Storm-1113, Sangria Tempest, and Storm-1674.
Microsoft Blocks MSIX Installer
That is not the first time Microsoft faces the exploitation of this installation method. In February 2022, Microsoft disabled the vulnerable protocol, due to its exploitation by Emotet, TrickBot, and BazaLoader malware. Back in the days, the used vulnerability was a bit different, but lead to almost the same effect – the drive-by malware installation.
This time, Microsoft recommends installing the patched App Installer version 1.21.3421.0 or later to block possible abuse. The patch disables the ms-appinstaller handle by default, thus making it impossible to misuse it. Redmond also advises administrators who cannot immediately install the latest version of App Installer to disable the protocol via Group Policy. They can do that by setting EnableMSAppInstallerProtocol to Disabled.
Is This Vulnerability Dangerous?
It is rather dangerous, and it becomes clear once you see the list of threat actors that exploit this issue. Most of the time, it allows for backdoor and RAT installation, which act as open gates for more malicious programs. Even though in current attacks MSIX vulnerability is used mostly against corporations, nothing stops cybercriminals from applying it against home users.
To stay protected against such attacks, it is vital to install the latest patches and keep an eye on cybersecurity news. As you can see, any critical vulnerability almost always hits the newsletter headlines.
As a layer of reactive protection, I can recommend having an advanced security solution. While being hard to detect in a signature analysis due to the spoofed certificate, malware is rather easy to uncover on the run with a heuristic detection system. GridinSoft Anti-Malware is a solution that can provide you this kind of protection.