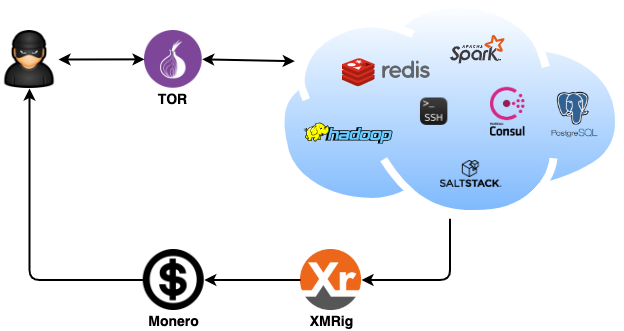
Zscaler analysts reported about the new DreamBus botnet that attacks corporate applications on Linux servers. It is a variation of the SystemdMiner malware that appeared back in 2019.
DreamBus has received a number of improvements over SystemdMiner. For example, the botnet mainly targets enterprise applications running on Linux systems, including PostgreSQL, Redis, Hadoop YARN, Apache Spark, HashiCorp Consul, SaltStack, and SSH.
Some of them are subject to brute-force attacks, during which malware tries to use default credentials, while others are attacked by exploits for old vulnerabilities.
The main task of DreamBus is to allow its operators to gain a foothold on the server so that they can download and install an open source miner for mining the Monero cryptocurrency (XMR). In addition, some of the infected servers are used as bots to expand the botnet, as further brute force attacks and search for other possible targets.
Also, Zscaler experts note that DreamBus is well protected from detection.
For example, all systems infected with malware communicate with the botnet’s control server using the new DNS-over-HTTPS (DoH) protocol, and the hacker’s C&C server is hosted in Tor.
Researchers warn that while the botnet may seem harmless, as distributes only a cryptocurrency miner, but in the future, DreamBus operators can easily switch to using more dangerous payloads, including ransomware.
Let me remind you that I also wrote about the fact that new worm for Android spreads rapidly via WhatsApp.