Spyware can be called the most sophisticated malware these days. It never acts openly, uses tricky techniques, and appears more often with other viruses. Together with its brother-in-law – stealer malware – spyware helps the cyber criminals to find and exfiltrate the data from attacked corporations. Moreover, ransomware that aims at individuals (exactly, STOP/Djvu family) can also contain spyware – it is used to steal the credentials and collect the system information after the encryption. However, most of these cases are pretty ordinary. Let’s have a look at the most famous spyware attacks in 2022.
Technical reference. What is spyware?
Before talking about the most interesting attacks with spyware, let’s remember some details about this malware. Spyware is a type of malicious software that aims at collecting information about the infected system and its users. It is sometimes associated with stealer – a related malware type that is often met together with spyware but has other functions. The similarity of spreading ways and disguises makes them ideal partners.
Spyware is oftentimes presented as a rogue program. It may look like a GPS tracker for your family, a notepad, or an alternative client for certain social networks. You may even like its functionality; however, its maintainers will analyze your personal information. And you will barely be able to blame these developers for accessing and storing your data – you had likely agreed with it in the EULA of these programs.
Nonetheless, during the attacks we are going to review in that article, spyware is injected as a “classic” malware – just a small executable file that launches together with the system and works silently. It is much more useful when you try to infect a corporate network with an EDR system running in it. Small file size, obfuscation, the ability to metamorphosis, and even unique malware for each target – are the characteristics of a modern “professional” spyware.
Famous Spyware Attacks in 2022: TOP Examples
The most significant spyware deployments usually happen during cyberattacks on corporations and jointly with other malware. In particular, the most often “companion” for spyware is ransomware. Stealer malware, the other follower of spyware, is sometimes deployed as a part of spyware. That’s why the reviewed cases will always have several other malware applied.
1. Bernalillo County government shutdown
At the beginning of the year, a peculiar cyberattack happened in Bernalillo County, New Mexico, US. The data breach reportedly happened on January 5, 2022. Crooks managed to break into the city control system, take over automatic door mechanisms, and cameras in jails and close down government buildings. During the incident, all employees inside the blocked building were trapped – no one besides the crooks could open the doors.
The official announcements on this case were pretty unclear. While the Bernalillo government stated that that was a ransomware attack, no evidence of file ciphering was found. Meanwhile, several lots on the Darknet auctions offered data about the “New Mexico population”. Meanwhile, no other published facts confirm the leak besides the cybersecurity analysts’ words about the spyware presence in the payload. Was the thing on the Darknet just someone’s joke, or was that for real, or a coincidence – no one can say for sure.
2. Puma employees’ information leak
Puma, a world-known sports clothing manufacturer, shoes and accessories, was attacked at the edge of 2022. The cybersecurity incident lasted for over a month – from December 2021 to January 22, 2022, until Kronos (Puma’s management solution vendor) managed to reach the data. Besides the file encryption, they also stole the data of almost 6,700 employees. Customer data was not affected, as Kronos assures.
Solving that issue and paying the compensation took another month. To deal with the reputational loss Kronos offered the company two years of identity monitoring service for free. They also protected their employees from identity theft and compensated for all spending on identity recovery.
3. Hensoldt attack
Hensoldt, a multinational technology company that produces electronic equipment for protection and surveillance was attacked a week after the attack on Bernalillo County – on January 12. Exactly, British subsidiaries of that company fell victim to a ransomware attack. No one has published any evidence that could make it possible to determine the attacker. However, the Lorenz group already claimed responsibility for this attack and reported that the ransom (between $500,000 and $700,000) was paid for both file decryption and leaked data.
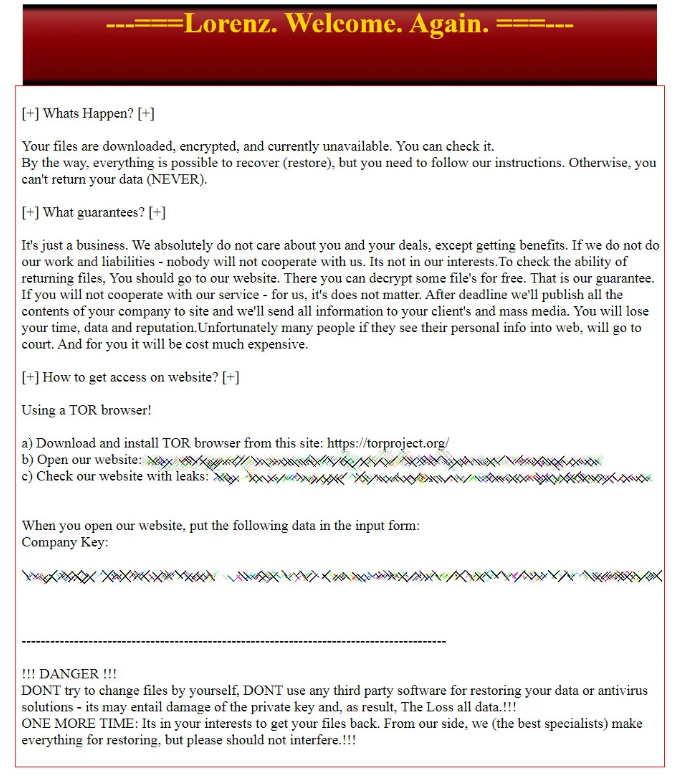
The specificity of this spyware attack case is that Hensoldt serves many military companies worldwide. Such companies always contain precious data – not only about the clients but also about new research. Information about radars, optoelectronic systems, and avionics – the main specialization of Hensoldt – may be very valuable for intelligence agencies from different countries. Hence, this case is loud rather because of the politics than because of the damage that was done.
4. nVidia 1TB leak of user data
An infamous cybercriminal gang Lapsu$, which is reportedly led by a 16-year-old schoolboy, attacked a chip giant at the end of February 2022. On the 4th of March, the gang threatened to publish the data if the ransom was not paid. The company assures that they don’t see any relation of this incident to the Russia-Ukraine war. Maybe, the most peculiar thing about that hacking is that Nvidia decided to get revenge and hacked the Lapsu$ back. Nonetheless, the latter was not affected by that break-in since they had a backup.
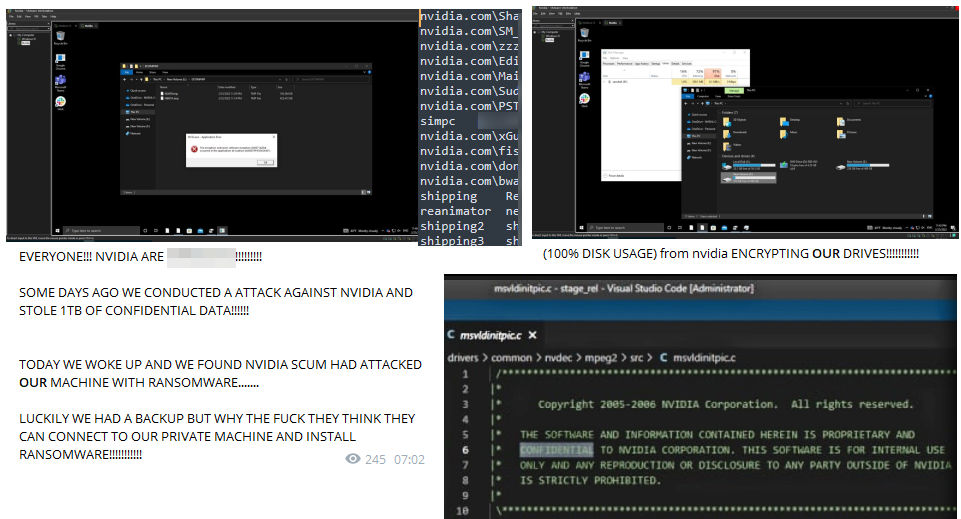
The information leaked from Nvidia is different and extremely valuable. Proprietary info – source codes of Nvidia software and firmware, employee credentials, and some information about the products in development. The gang published all that stuff on their Darknet marketplace. Crooks said they still analyze the data – so they have not deleted it after the ransom payment. Possibly, they will post it for sale in the future – for a much bigger sum.
5. Bridgestone data breach
Several days after the attack on nVidia, the biggest auto tires manufacturer on the entire globe was hacked by the other famous threat actors – the LockBit group. Cybersecurity specialists detected the ongoing attack and disconnected the damaged network facilities in Latin and North America. But that was too little too late. Crooks succeeded in shutting down the whole network, causing the production to stop for a week. Then they posted a typical double extortion message, with a deadline of 23:59 March 14.
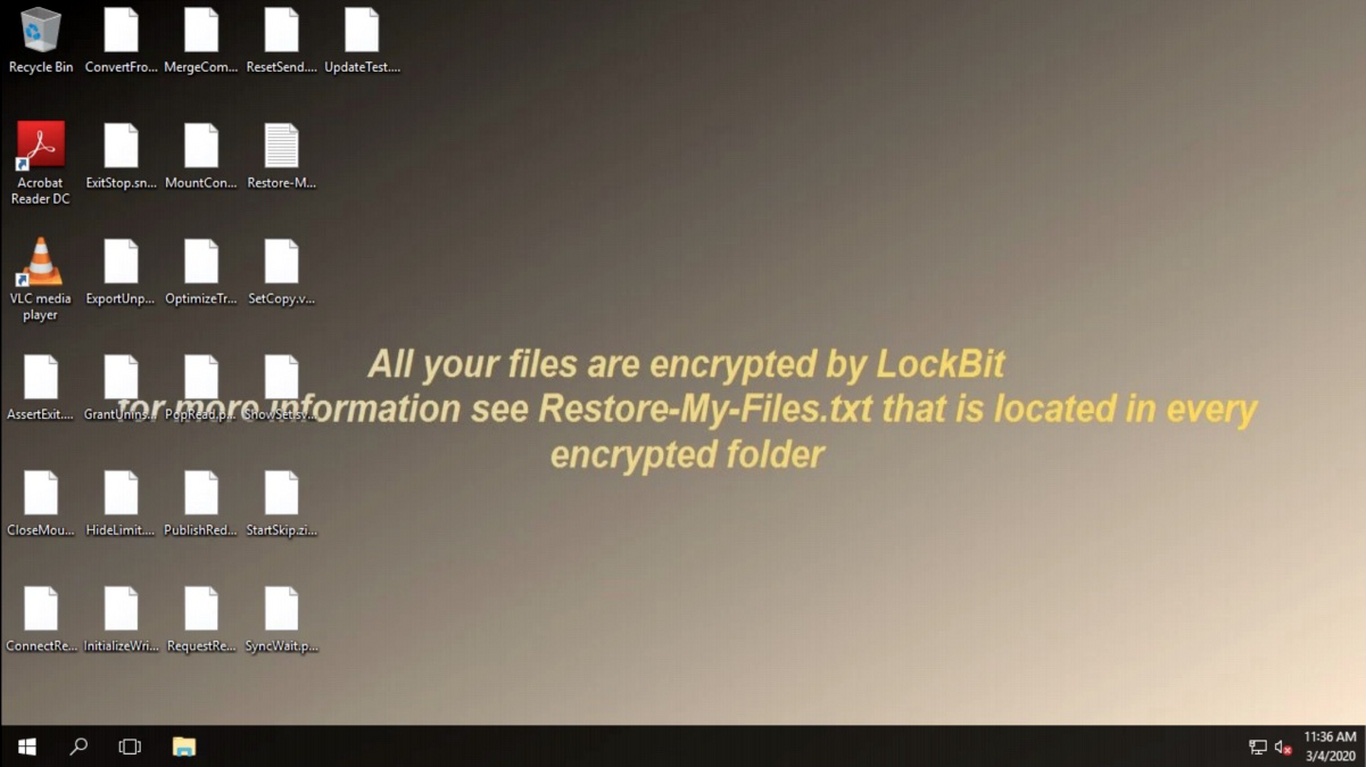
This incident could have been prevented – if Bridgestone had paid attention to the FBI notice about the indicator of compromise. The IOC related to LockBit ransomware was detected by the Federal Bureau of Investigation almost a month before the attack. Was that the recklessness of Bridgestone management or the absence of ways to counteract it? Or did we see the repeating of the Coventry story?
Conclusion. How to protect the data from spyware attacks?
Spyware has different forms, depending on its target. Individual users will likely get in the form of trojan virus – a seems-to-be-legit program that leaks the info about the user to its developers. It sharply contrasts with what corporations receive – a small, hard-to-detect program that masks skillfully in the system. Advice is correspondingly different.
Individual users must pay additional attention to the programs they install and use. Exactly, additional attention is needed to the applications that ask for access to things they may not need. How can a calculator use your gallery? Or why the navigation app may need your contacts? Ask these questions to yourself each time you install such dubious things.
- Data ciphering. Crooks will not be happy to see that the stolen data is encrypted – so apply the disk encryption to make it useless for someone who does not have a key. Fortunately, Windows has a default disk encryption mechanism – a pretty reliable one.
- Block the extraction. When spyware has successfully collected all the data, it prepares the environment for uploading the data to the C & C server. Blocking the external connections, excluding the ones used by your employees, will prevent data exfiltration.
- Change the credentials regularly. The expired product costs the least. When in the data pack sold on the Darknet, there are no workable login/password chains. This pack is worth nothing. Sure, sometime after the leak, these credentials will be legit, but often changes will substantially decrease the best-before period.
Anti-spyware measures in corporations may have general and specific characteristics. Using advanced security solutions and teaching cyber-hygiene to your employees will decrease the chances of getting this nasty thing. Meanwhile, several steps will have an effect, specifically from spyware. To avoid this, we have provided you with a guide to help protect your device from unwanted threats.