Information Security Experts Told About The Linux Malware Symbiote That Is Almost Undetectable
BlackBerry and Intezer specialists spoke about the new Symbiote Linux malware that infects all running processes on compromised systems, steals credentials and provides backdoor access to its operators. Let me…
Joint Operation: SSNDOB Personal Data Darknet Market Seized
What SSNDOB Was Before Its Servers Were Seized The US Department of Justice, Internal Revenue Service, and Federal Bureau of Investigation have joined forces with law enforcement authorities in Latvia…
Beware: New SpaceX Bitcoin Giveaway Scam
Crooks Make Elon Musk a Bait for Wannabe Cryptotraders Scammers again use SpaceX as a bait in fraudulent schemes. The statements of Elon Musk, CEO of the company, have been…
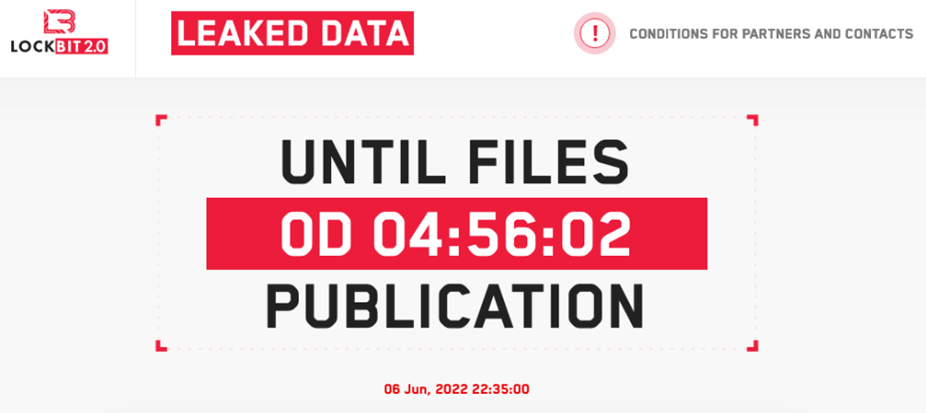
LockBit 2.0 Promises to Leak Mandiant Data
LockBit 2.0 announcement: real thing or vengeful trolling? On June 6, on its portal on the dark web, LockBit 2.0, a ransomware operator, has announced the exposure of data allegedly…
Microsoft Is in No Hurry to Fix the Follina Vulnerability, Which Has Become a Real Disaster
Hackers are actively exploiting the critical 0-day Follina vulnerability, which Microsoft is in no hurry to fix. Researchers warn that European governments and municipalities in the US have been targeted…
11 Types of Spoofing Attacks
Spoofing is a kind of cybercrime in which attackers impersonate a trusted source, such as a trusted contact, to gain access to confidential information or steal data, whether personal or…
Attackers Exploit MSDT Follina Bug to Drop RAT
Security specialists caution users about the exploitation of the recently disclosed Follina Bug found in all supported versions of Windows. Threat actors have actively utilized this vulnerability to install payloads…
New Cuba Ransomware Variant Involves Double-Extortion Scheme
What's new in April Variant of Cuba Ransomware The Cuba ransomware family has got itself a new specimen. The new version of Cuba revealed itself in late April 2022 and…
Evil Corp Switched to Using LockBit Malware to Avoid Sanctions
The Evil Corp group switched to using the LockBit ransomware to avoid sanctions imposed earlier by the Office of Foreign Assets Control of the US Department of the Treasury (OFAC).…
Warning Signs Of DDoS Attack: Symptoms
DDoS attacks can sometimes have devastating effects on various internet users. This particular type of cyber threat can put on hold different internal operations, create negative relationships with customers, and…
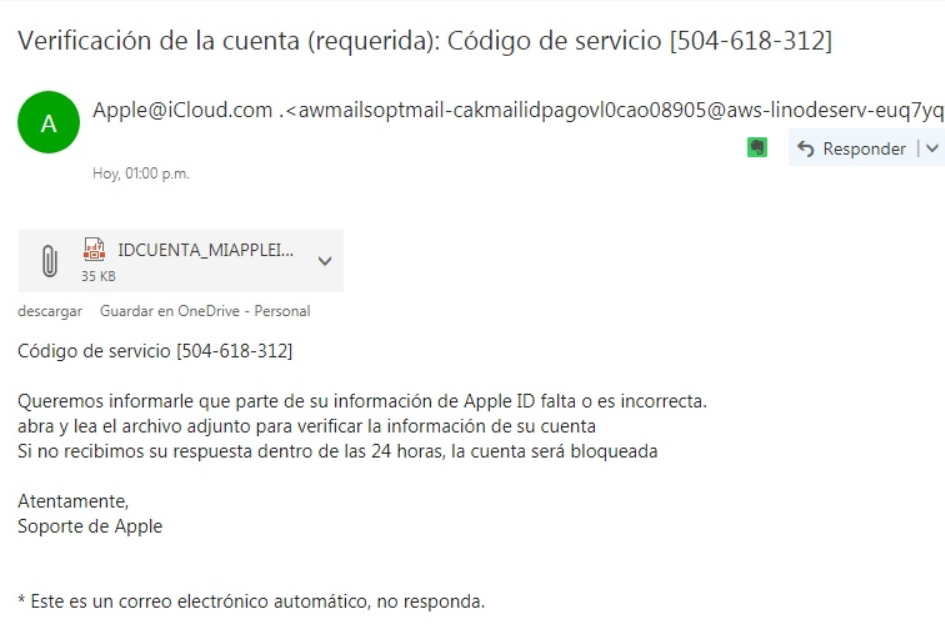
Extension spoofing strikes Spanish-speaking countries
An old-good form of malware disguisment sparked recently in several Spanish-speaking countries across the globe. Users note numerous cases of email attachments with spoofed file extensions, that appear to be…
Types of SQL Injection: Attack Examples
As we wrote in one of the articles, SQL is a structured query programming language (SQL, Structured Query Language) that allows programmers to communicate with large databases in almost plain…