The products by WSO2, an open-source API, applications, and web services provider, have been attacked in the wild through the CVE-2022-29464 vulnerability detected back in April 2022.
This vulnerability allows attackers to execute malicious code remotely via unhindered file uploading.
The scheme of the attack begins with web shell installation through *.jsp or *.war files upload taking advantage of the CVE-2022-29464 vulnerability. As the web shell is installed, the attacker executes an arbitrary Java process with its help.
RELATED: Microsoft warns of growing number of attacks using web shells.
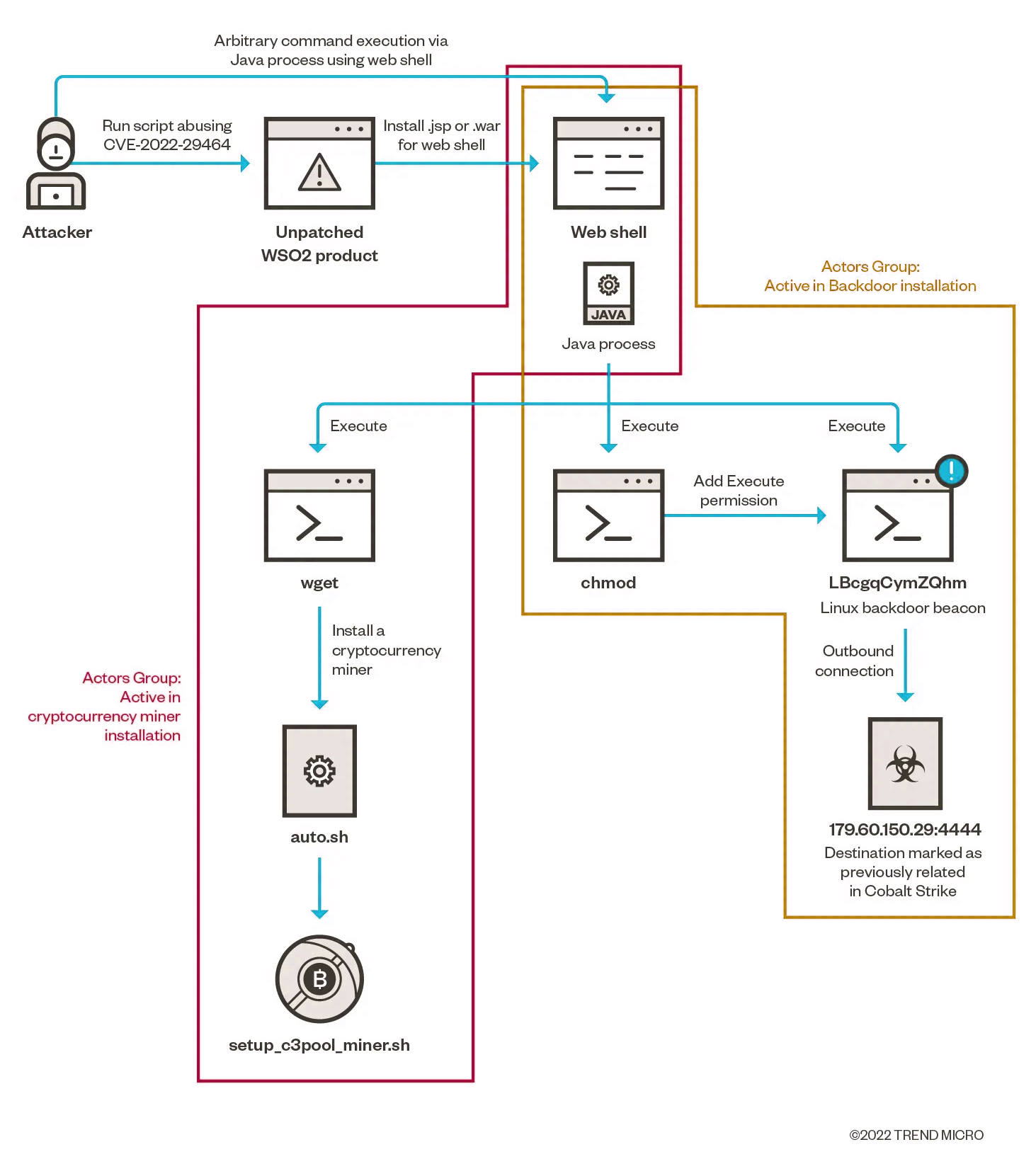
The results of the attack are the installation of a coin miner and Cobalt Strike beacon (backdoor.) The cryptocurrency miner is installed via the Java-process-launched wget command that installs the auto.sh file (the miner itself.) In the meantime, another part of the attack happens, also via the web shell. Java process calls a chmod command that modifies permissions to make it possible to run the process entitled “LBcgqCymZQhm” all through the same Java process. The process establishes an outbound connection to an IP address 179[.]60[.]150[.]29[.]4444, earlier tracked as a location involved in numerous Cobalt Strike attacks. Therefore, the LBcgqCymZQhm process is a Cobalt Strike backdoor beacon.
The most interesting thing is that the Cobalt Strike beacon, initially designed for Windows, turned out to be working on Linux during these attacks. That means the hackers have purposefully worked upon the backdoor’s compatibility with Linux.
The vulnerable software includes WSO2 API Manager 2.2.0 and above, Identity Server 5.2.0 and above, Identity Server Analytics 5.4.0 -5.6.0, Identity Server as a Key Manager 5.3.0 and above, Open Banking AM 1.4.0 and above, and Enterprise Integrator 6.2.0 and above. The patch is already there, so all users of the mentioned programs are advised to patch the flaws in question ASAP.
The multiple WSO2 clients belong to many industries, vital ones included. For example, healthcare, financial sector, energy, education, communications, and government. Needless to say, should the hackers exploit the CVE-2022-29464 vulnerability against unpatched systems, the consequences of the attack could be drastic.





