Cyble experts have warned that cybercriminals are attacking IS researchers, distributing malware under the guise of exploits for Windows, which eventually installs Cobalt Strike beacons on the experts’ machines.
Let me remind you that we also wrote that Emotet now installs Cobalt Strike beacons.
Cyble analysts report that malware disguised as PoC exploits for a pair of Windows vulnerabilities (CVE-2022-24500 and CVE-2022-26809) recently appeared on GitHub, which Microsoft patched as part of the April “update Tuesday”.
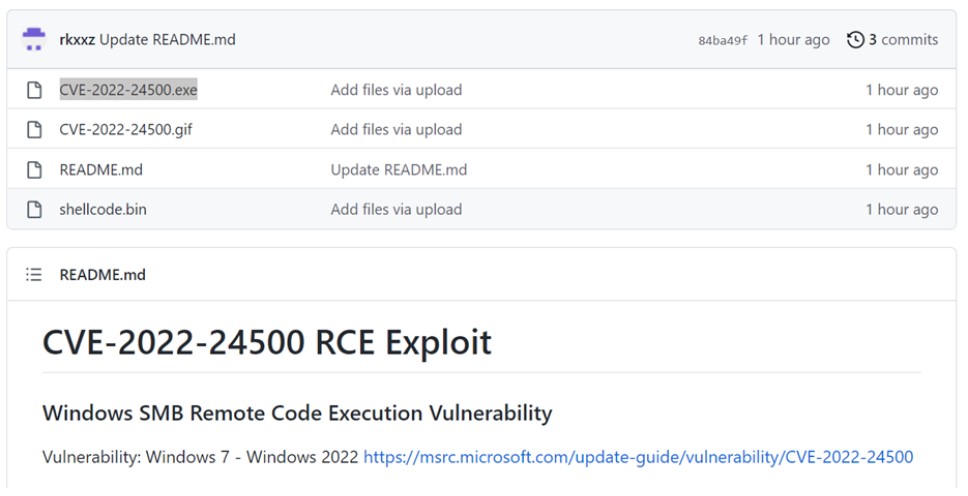
Fake exploits were published in the repositories of the user rkxxz, which have now been deleted along with the account itself. As always happens after the publication of PoC exploits, the news quickly spread on Twitter and even attracted the attention of attackers on hacker forums.
You might also be curious to know what Cybersecurity Experts Analyzed the Methods of a Group of Russian Hackers Wizard Spider.
And it soon became clear that the exploits were actually fake, and Cobalt Strike beacons were installed on people’s devices. Cyble analysts have taken a closer look at the fake PoCs and found that they are written in .NET and pretend to exploit the IP address, in fact infecting users with a backdoor.
The deobfuscated exploit sample showed that the fake PoC runs a PowerShell script that executes another gzip-compressed PowerShell script (VirusTotal) to inject the beacon into memory.
The researchers note that this is not the first case of targeted attacks on cybersecurity experts. The fact is that by attacking members of the cybersecurity community, in theory, attackers not only gain access to data on vulnerability research (which the victim can work on), but can also gain access to the network of a cybersecurity company. And this can be a real gold mine for hackers.
Cobalt Strike is a legitimate commercial tool built for pentesters and red teams and focused on operations and post-operations. Unfortunately, it has long been loved by hackers ranging from government APT groups to ransomware operators.
Although the tool is not available to ordinary users, attackers still find ways to use it (for example, rely on old, pirated, hacked and unregistered versions).