
Matrix Ransomware
A lot of actors in the ransomware field are active for only two or three years. Such statistics are caused by some rapid changes in the distribution methods of ransomware - the appearance of ransomware-as-a-service, for example. It can be quite hard to adapt to the new environment, so crooks decide to make something completely new rather than fix an old thing. But some of the ransomware variants keep going even though all changes happened to the paradigm.
The Matrix ransomware group, which started its activity a relatively long time ago, shows huge adaptability to the environment. Companies are not so careless about cybersecurity, compared to the single users, so when you are aiming at corporations - you should discover new injection methods to keep going. Initially, Matrix was spread through the RIG exploit kits, Windows shortcuts vulnerabilities and email spamming. Those methods were pretty effective against companies up to 2018, when the majority of the exploited vulnerabilities were fixed. Hence, these cybercriminals should change their tactics - or shut down their activity.
In 2018, the Matrix group completely changed the distribution methods. In contrast to previously used ways, they applied RDP vulnerabilities exploitation - just like Dharma ransomware does. Such a change is a precondition for a long life to Matrix since RDP breaches are based on human factors rather than on program vulnerabilities. In 2019, Matrix was reportedly attacking companies in 10 countries - U.S., Belgium, UK, Mexico, Germany, Brazil, Taiwan, Canada, Chile, and South Africa. And with the time flow, the corporations from various other countries reported the Matrix attacks.
Several words about the distribution
As it was mentioned, the main way of Matrix ransomware distribution is brute-forcing the RDP vulnerabilities. This way to attack the companies became even more effective after the start of the pandemic - when the majority of workers were forced to work from home. In such circumstances, remote access to the workplace is a perfect solution that allows the employees to have full access to what they have on their workstations. However, the Remote Desktop Protocol - the default technology for remote access, offered by Microsoft, contains several critical vulnerabilities. Microsoft does not hurry to fix them, regardless of the fact that these breaches were discovered long ago. Hence, the companies must close these vulnerabilities on their own.
When the RDP is established by an experienced user, all possible security breaches will likely be closed. These breaches hide inside of the connection ports - some of the last ones can easily be accessed from the outside. People who know about such a breach just create the connection through other ports, and close the vulnerable ones to prevent possible attacks. But when you have no experience in establishing really secured connections, it is pretty easy to miss this thing.
Ransomware distributors scan the opened ports in the RDP network of a certain corporation, trying to find the unsecured vulnerable port. In case when they find one - they connect through it and attempt to log into the corporate network using brute force. Sooner or later they will hack the login and password for one of the accounts - and the action begins.
How does Matrix ransomware encrypt?
In contrast to a lot of other families, the Matrix virus uses mixed encryption: the files are ciphered with AES-256, and then re-ciphered with RSA-2048. By the way, that action does not bring any effect, since single AES-256 encryption is enough - no one will be able to decrypt it in acceptable terms. Hence, additional encryption with RSA cipher is rather a spooking maneuver, than really effective action.
Technical details
| Note | INFO.hta file. Contains the notice about what happened and offer to decrypt 3-5 files for free. |
| File pattern | %filename% . %original_extension% . %ransomware_extension% |
| Algorithm | AES-256+RSA-2048 |
| Features | Very old player on the ransomware market - keeps going since 2016 |
| Damage | Deletes Volume Shadow Copies, disables Microsoft Defender and removes other anti-malware software. |
| Distribution | RDP vulnerabilities exploiting |
Here is the typical ransom note, that is left by Matrix ransomware after the encryption is done:
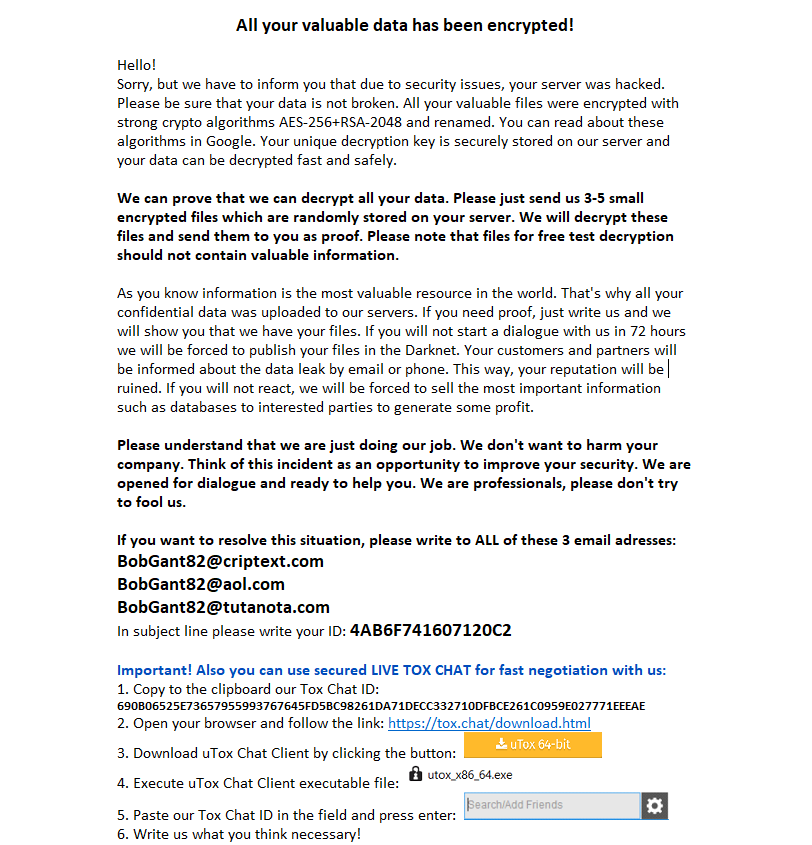
Before performing the file encryption, this malware also prevents the usage of all basic recovery methods. It deletes Volume Shadow Copies and backups created with the basic Windows methods. Volume Shadow Copy is a mechanism that allows keeping the system drive copy, in order to use it for system recovery, but it may also be useful to recover the files after the ransomware attack.
During the 2020, Matrix group used the following extensions for their attacks (by the chronological order):
.MTXLOCK, .CORE, .ANN, .FOX, .KOK8, .KOK08, .NEWRAR, .FASTBOB, .FASTB, .EMAN, .THDA, .RAD, .EMAN50, .GMPF, .ATOM, .NOBAD, .TRU8, .FASTA, .JNSS, .FBK, .ITLOCK, .SPCT, .PRCP, .CHRB, .AL8G, .DEUS, .FG69, .JB88, .J91D, .S996, .[[email protected]], .[[email protected]][[email protected]], .[[email protected]], .[[email protected]], .[[email protected]], .[[email protected]], .[[email protected]], .[[email protected]], .[[email protected]], .[[email protected]], and .[[email protected]]
The average ransom amount of Matrix ransomware is about $58,000. This sum is relatively small compared to other ransomware that are currently active. But it is pretty easy to understand why they charge such a low payment for the decryption - their usual targets are small companies. If you charge too much - they will likely refuse to pay or will have further financial problems. And it is pretty easy to understand that the FBI will have an increased interest in a ransomware group that pushes small business units into bankruptcy.
