A Windows malware designed to steal cryptocurrency and clipboard contents installs a malicious VenomSoftX Chrome extension on users’ machines. The extension works like a RAT (Remote Access Trojan), stealing victims’ data and cryptocurrencies.
Let me remind you that we also said that Malicious Ledger Live extension for Chrome steals Ledger wallet data, and also that 295 Chrome extensions injected ads in search results.
The existence of ViperSoftX malware has been known to security experts since 2020, for example, Cerberus and Fortinet have already talked about it. Now, the malware has been studied in detail by Avast experts. They report that the malware has changed noticeably since then.
The company report says that since the beginning of 2022, Avast has detected and stopped 93,000 ViperSoftX attack attempts against its customers, mainly affecting users from the United States, Italy, Brazil and India. At the same time, it is known that the main distribution channel for malware is torrent files of game cracks and activators for various software.
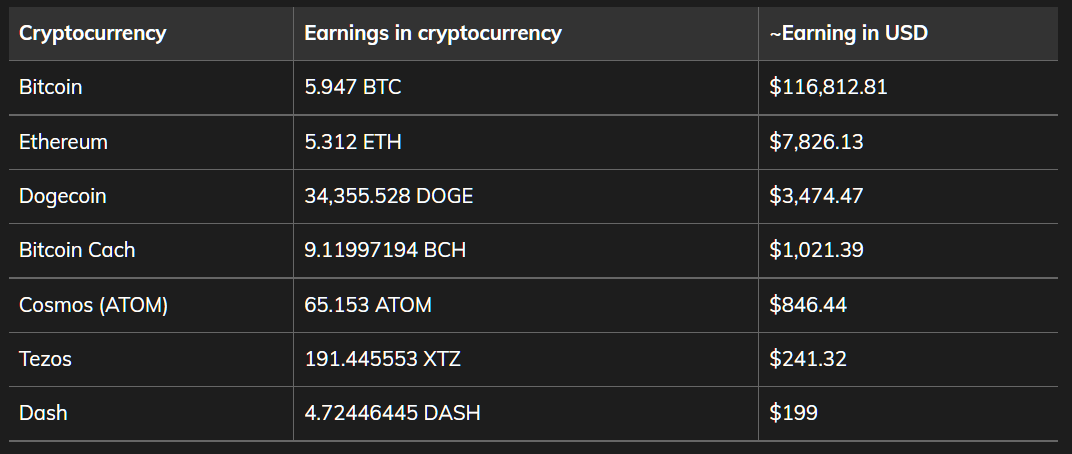
After examining the wallet addresses that are hard-coded in the ViperSoftX and VenomSoftX samples, the experts found that as of November 8, 2022, the attackers “earned” about $130,000. Moreover, the stolen cryptocurrency was obtained solely by redirecting cryptocurrency transactions on hacked devices, that is, this amount does not include profit from other activities of hackers.
The new variants of ViperSoftX do not differ much from those studied earlier, that is, they can steal data from cryptocurrency wallets, execute arbitrary commands, download payloads from the control server, and so on. The main difference between the new versions of ViperSoftX is the installation of an additional malicious VenomSoftX extension in the victim’s browsers (Chrome, Brave, Edge, Opera).
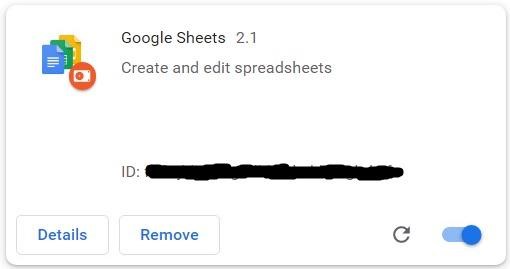
To hide from the victim, the extension masquerades as Google Sheets 2.1, allegedly created by Google, or as a certain Update Manager.
Although VenomSoftX largely duplicates the functionality of ViperSoftX (both malware target the cryptocurrency assets of victims), the extension itself carries out the theft differently, which increases the chances of attackers to succeed.
In particular, the targets of VenomSoftX are Blockchain.com, Binance, Coinbase, Gate.io and Kucoin, and the extension monitors the user’s clipboard and replaces any addresses of cryptocurrency wallets (as Carabank Group did, for example) that get there, with the addresses of attackers.
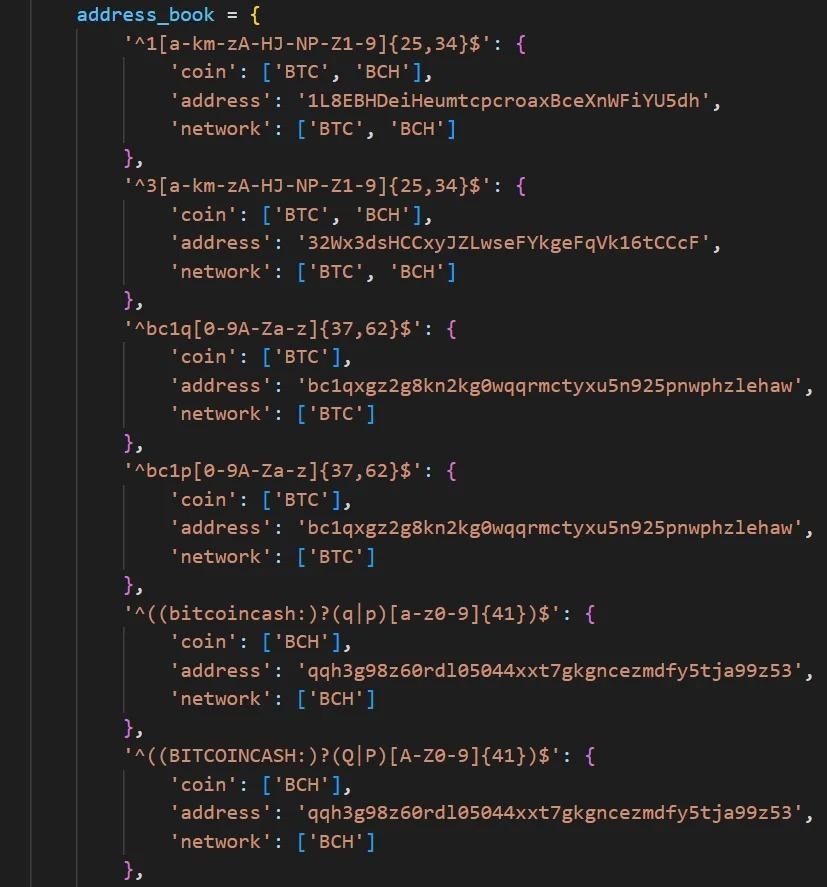
In addition, the extension can change the HTML code on sites to detect the address of the user’s cryptocurrency wallet, while manipulating elements in the background and redirecting payments to attackers.
To determine the victim’s assets, the VenomSoftX extension intercepts all API requests to the aforementioned cryptocurrency services, and then sets the maximum available transaction amount, stealing all available funds.
Moreover, in the case of Blockchain.info, the extension will try to steal the password entered on the site.
The researchers say it’s easy to detect such fake Google Sheets: the real Google Sheets are usually installed in Chrome as an app (chrome://apps/) and not as an extension, which is fairly easy to check on said page. If the extension is present in the browser, you should remove it as soon as possible, clear the data, and probably change the passwords.

