Gamaredon Hack Group Uses New Malware to Attack Ukrainian Organizations
Cisco Talos analysts write that the Russian-speaking hack group Gamaredon (aka Primitive…
Does a Factory Reset Get Rid of Viruses?
You can use the reset feature to destroy the virus from your…
The New Shikitega Malware Is Very Difficult to Detect and Eliminate
AT&T researchers have discovered a new Linux stealth malware called Shikitega that…
SharkBot Malware Infiltrates Google Play Store Again
Information security specialists from Fox IT discovered two applications in the Google…
Dangers Of Spam Email: Tips How To Avoid, Spam Email Revenge
Many businesses don't consider all of the dangers of spam and just…
Malware Hides in Images from the James Webb Telescope
Securonix researchers have noticed an interesting malware campaign that distributes a malware…
Experts Demonstrate Data Extraction Using LEDs and a Gyroscope
This week, researchers have demonstrated two interesting ways to extract data from…
Researchers Found 35 Malware on Google Play, Overall Installed 2,000,000 Times
Bitdefender experts found 35 malware in the Google Play Store that distributed…
IS Specialists Discovered a New Version of Malware from Russian Hackers LOLI Stealer
Cyble Research Labs specialists found a sample of malware in the wild,…
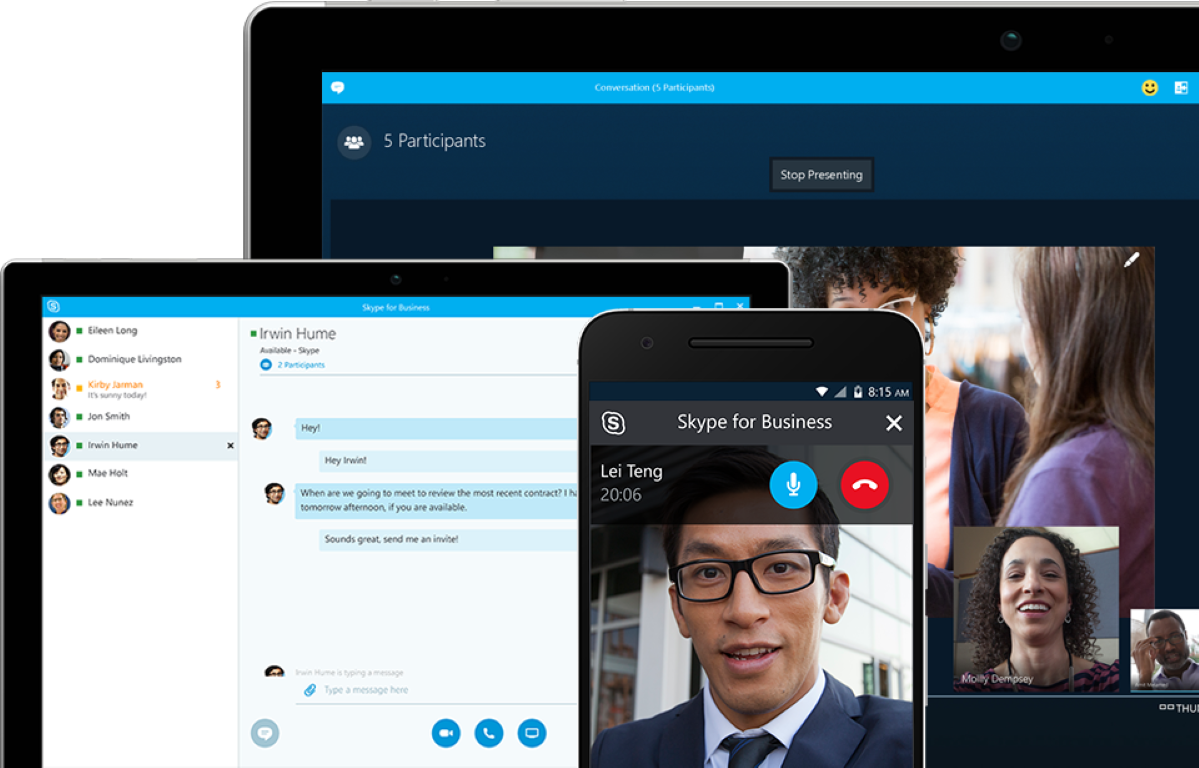
Most Often, Malware to Bypass Protection Impersonates Skype, Adobe Acrobat and VLC
VirusTotal analysts presented a report on the methods that malware operators use…
Microsoft Links Raspberry Robin Worm to Evil Corp
Microsoft analysts have noticed that the access broker, which the company tracks…
The Austrian Company DSIRF Was Linked to the Knotweed Hack Group and the Subzero Malware
Microsoft has been told that the Knotweed hack group is linked to…