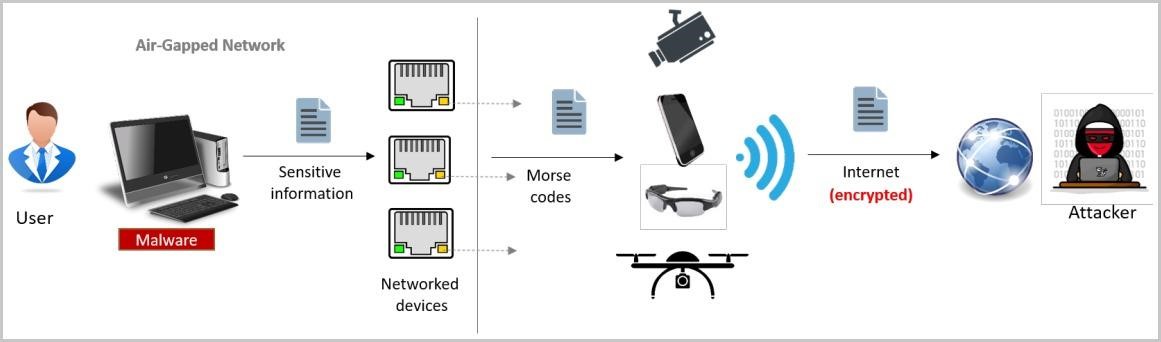
This week, researchers have demonstrated two interesting ways to extract data from machines that are physically isolated from any networks and potentially dangerous peripherals at once. The GAIROSCOPE method suggests using the gyroscope of the nearest smartphone for these purposes, and the ETHERLED method suggests using LEDs on network cards.
Like other attacks on isolated machines, GAIROSCOPE and ETHERLED rely on the potential ability of an attacker to compromise the target environment in advance and install malware on the machine using infected USB drives, a watering hole attack or compromise of the supply chain. Although this is not an easy task, researchers leave its solution “outside the brackets”, focusing entirely on the process of extracting information.

Let me remind you that we also talked about the fact that specialists from the Ben-Gurion University presented a new type of cyber-biological attack that can bring biological warfare to a new level.
Dr. Mordechai Guri, an Israeli information security specialist and the head of the R&D department at the Cybersecurity Research Center at Ben-Gurion University, developed and demonstrated the ETHERLED data mining method. ETHERLED converts blinking diodes into Morse code, which can then be decoded by an attacker.
Of course, to intercept such signals, you will need a camera located in direct sight of the LED indicators on the network card of the target computer. It may surprise someone that a machine isolated from any networks uses a network card, but the expert notes that ETHERLED can also use other peripheral devices that have LED indicators. For example, routers, NAS, printers, scanners, and so on are suitable for an attack.
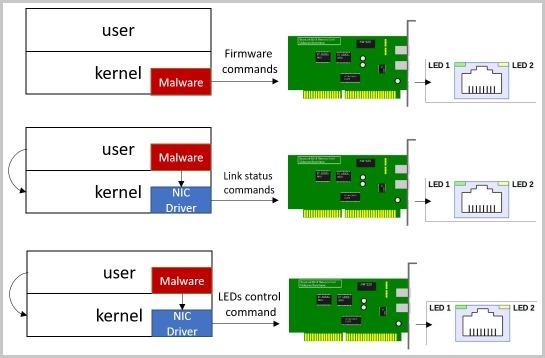
The attack begins with the installation of special malware on the target computer, which contains a modified version of the firmware for the network card. Changes allow attacker to control the frequency, duration and colors of the LEDs flashing. In addition, the Guri malware is able to change the connection state or modulate the LEDs necessary for signaling.
The fact is that a malicious driver can use documented and undocumented hardware functions to control the speed of a network connection, as well as to enable or disable the Ethernet interface, which causes the status indicators to blink and change color.
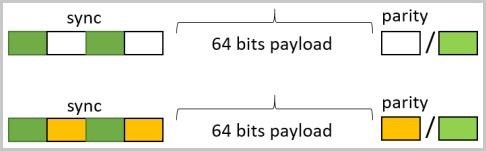
Each data frame begins with the sequence “1010”, indicating the start of a packet, followed by a 64-bit payload.
To extract data through individual LEDs, the expert generated Morse code dots and dashes (from 100 to 300 ms) separated by indicator off pauses (from 100 to 700 ms). It is noted that if desired, the speed can be changed and increased up to ten times.
To capture such signals remotely, a potential attacker can use anything from simple smartphone cameras (up to 30 meters), drones (up to 50 meters), hacked webcams (10 meters) and hacked surveillance cameras (30 meters), and ending with telescopes or cameras with powerful telephoto lenses (more than 100 meters).
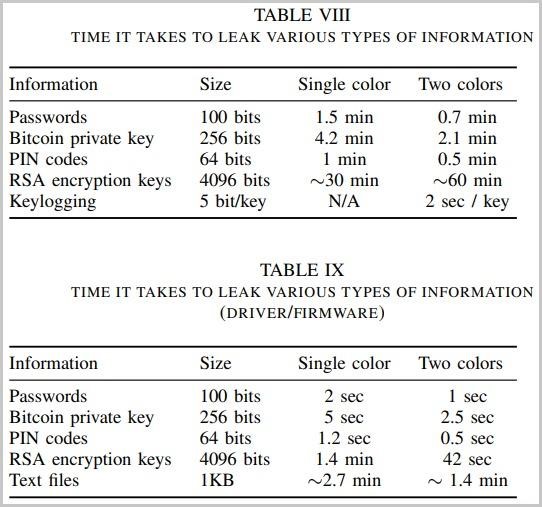
The time required to transfer data via ETHERLED varies from 1 second to 1.5 minutes for passwords; from 2.5 seconds to 4.2 minutes for private bitcoin keys; 42 seconds to an hour for 4096-bit RSA keys.
All the same, specialists from Ben-Gurion University, under the leadership of Dr. Mordechai Guri, demonstrated the second concept for stealing data from isolated machines. The GAIROSCOPE attack is based on the generation of resonant frequencies that can be intercepted by the gyro sensor of a smartphone located close to the target machine (up to 6 meters).
The researchers say that this time, the attack may require infecting the smartphones of employees working in the victim organization with a special application for the attack to work.
At the next stage of the attack, the attacker must collect confidential data (for example, encryption keys, credentials, and so on) on an isolated machine using pre-installed malware, and convert this information into sound waves indistinguishable by the human ear, which will be transmitted through the speakers or speaker of the infected cars.
Such a transmission must be intercepted by an infected smartphone located in close proximity to the isolated machine, or by an insider. A special malicious application on a smartphone “listens” to the gyro sensor built into the device, after which the data is demodulated, decoded and transmitted to the attacker via the Internet. Interestingly, the malicious application on the receiving smartphone (in this case, One Plus 7, Samsung Galaxy S9 and Samsung Galaxy S10 were tested) only has access to the microphone and does not arouse unnecessary suspicion among users.
Experiments have shown that this method can be used to transmit data at a rate of 1-8 bps at distances of 0-600 cm from an isolated machine (up to 800 cm in narrow and enclosed spaces).
The GAIROSCOPE attack is also interesting because Android and iOS don’t have any visual cues to indicate that an app is using a gyroscope. What’s more, the gyro sensor is even accessible via HTML via standard JavaScript. This means that an attacker may not even install a special application on the victim’s device, but instead inject a JavaScript backdoor into some legitimate site that will interrogate the gyroscope, receive hidden signals and transmit information to its operators.




