Experts discovered ESPecter UEFI bootkit used for espionage
ESET experts discovered the previously unknown ESPecter UEFI bootkit, which was used…
Malware developers increase use of the unusual programming languages
BlackBerry Research & Intelligence analysts have found that criminals are increasingly turning…
Scammers distribute fake Windows 11 installers
Fraudsters explore curiosity about the release of Windows 11 to distribute fake…
Previously assessed as insignificant, DirtyMoe botnet infected over 100,000 Windows systems
The developers of the DirtyMoe botnet (which was assessed as insignificant) added…
TeamTNT mining botnet infected over 50,000 systems in three months
Trend Micro warns that since March 2021, the TeamTNT mining botnet from…
Hackers infected the Android emulator NoxPlayer with malware
UPDATE: BigNox contacted us and said that they "contacted cybersecurity firm ESET…
What is the worst computer virus? Figuring out
Worst computer virus - what is it? Seems that anyone who has…
Microsoft: Supernova and CosmicGale malware detected on systems running SolarWinds
Continue studies oт large-scale attack on the supply chain, for which attackers…
Malicious packages found in RubyGems repository again
Sonatype experts have discovered the pretty_color and ruby-bitcoin malicious packages in the…
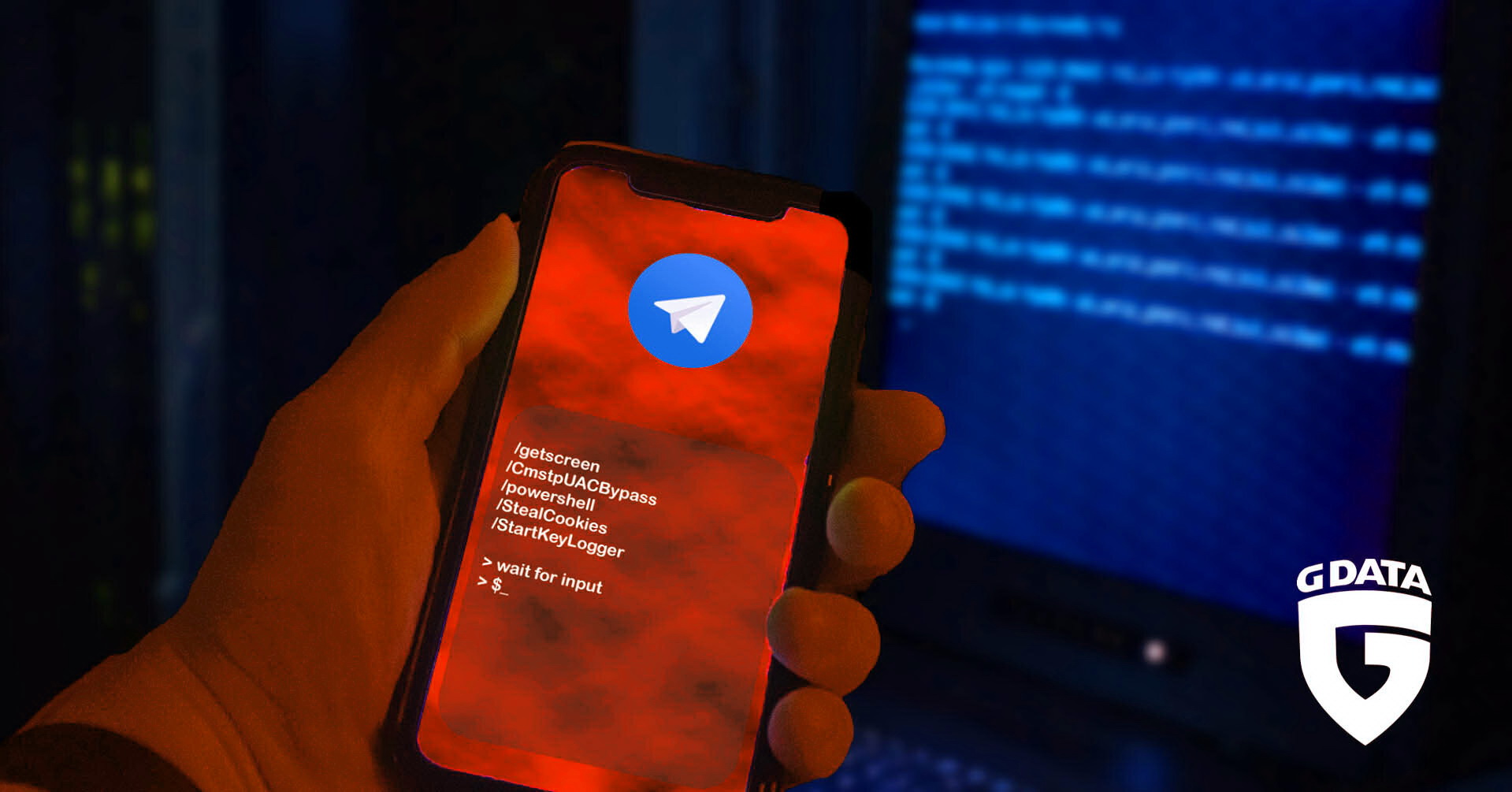
New T-RAT malware can be controlled via Telegram
G DATA's specialists have published a report on the new T-RAT malware,…
Alien malware steals passwords from 226 Android apps
ThreatFabric analysts have discovered a new Android malware Alien. The malware primarily…
KryptoCibule malware steals cryptocurrency from Windows users
ESET specialists discovered the KryptoCibule malware, which has been active since 2018…