Shuckworm hackers attack Ukrainian organizations with new variant of Pteredo backdoor
Specialists from the cybersecurity company Symantec reported attacks by the cybercriminal group…
Nation-State Threat Actors are an Actual Menace, According to CISA
On April 13, the US government (specifically, the Department of Energy, the…
RuRansom Malware Destroys Data in Russian Systems
VMware specialists spoke about the activity of the RuRansom wiper, which attacks…
RaidForums shutdown as the result of Operation Tourniquet
The chain of international law enforcement agencies - Europol, FBI, NCA and…
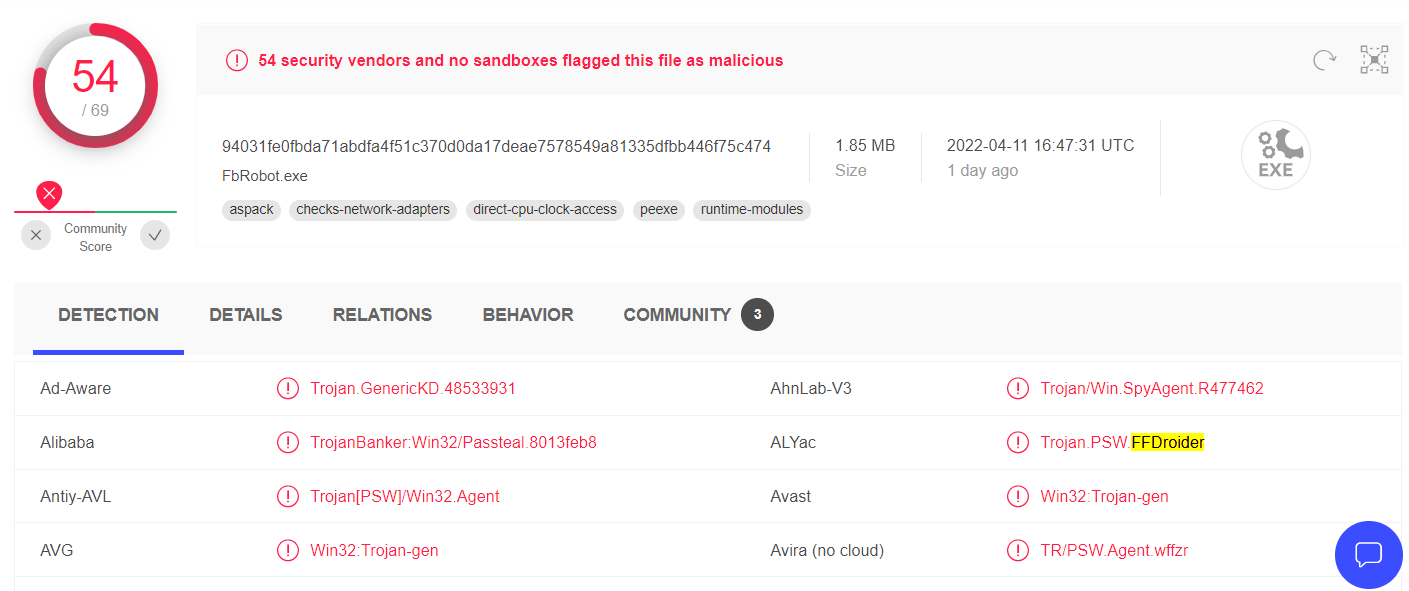
FFDroider Stealer: The New Hazard To Social Networks
FFDroider Stealer is the second malware of this type that popped out…
Meta Infostealer Malware Spread via Spam
Meta, a newly crafted information-stealing malware, is distributed via a vast spam…
Hackers attack hackers by spreading malware on underground forums
Information security specialists have discovered new evidence that hackers often attack hackers,…
TrickBot causes crashes on the machines when cybersecurity experts studying it
TrickBot malware has received new features that make it more difficult to…
New BHUNT malware hunts for cryptocurrency wallets
Bitdefender researchers talked about a new modular BHUNT malware that steals the…
The FBI believes that the HelloKitty cryptor is controlled by operators from Ukraine
A medical organization from Oregon, which recently reported a breach and data…
Emotet now installs Cobalt Strike beacons
The researchers warn that Emotet now directly installs Cobalt Strike beacons on…
Google Stops Glupteba Botnet and Sues Two Russians
Google representatives said that they stopped the work of the Glupteba botnet:…