Meta, a newly crafted information-stealing malware, is distributed via a vast spam spree. The mechanism of the stealer injection within this campaign is already well-known. However, Meta is now a mainstream tool among hackers. Therefore, further attacks featuring this software but with different scenarios are inevitable. This article explains how the current malspam scheme works. We also share the story behind the info stealer.
READ ALSO: Spyware vs. Infostealer – what’s the difference?
The information provided within the current article, including the images, is courtesy of Brad Duncan, an independent cybersecurity analyst, the man behind the malware-traffic-analysis.net blog.
Spam Campaign details
The Meta infostealer malware gets into the victim’s computer. It begins with an email with an attachment. Already a stay-away thing for the experienced ones, but someone might still buy into that. The bait is classic: you have received payment, and there is a little paperwork to be done before getting your money.
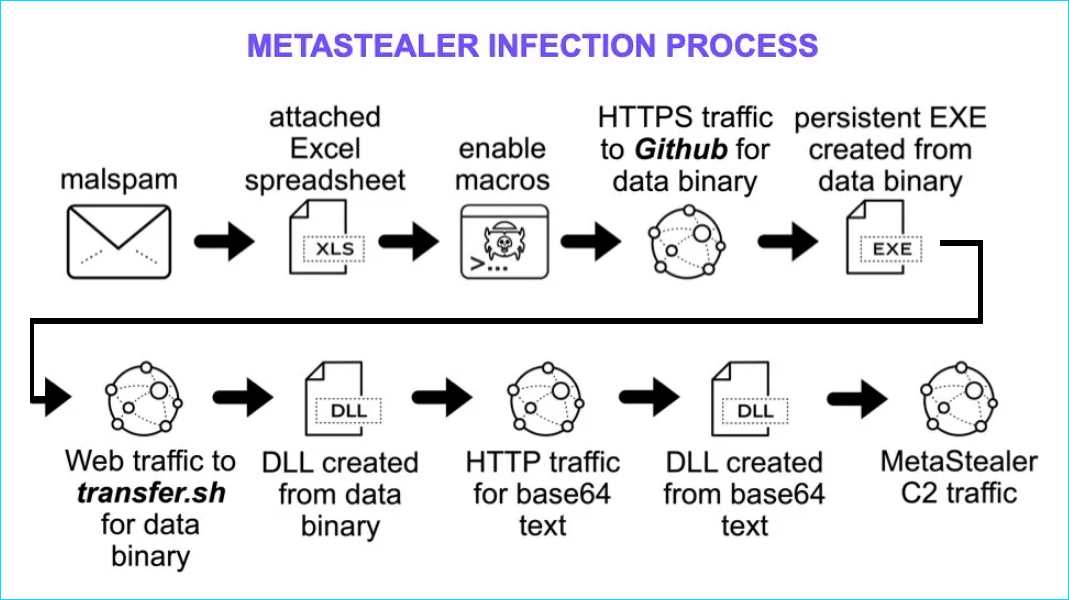
After the user downloads the attachment (an excel table within the current campaign,) the file will, just as expected, request allowance to execute macros. The sheets file features a DocuSign image to be more persuasive, although it is unnecessary since it is already downloaded. If the victim consents, enabled scripts (VBS) start downloading stuff from several sources.
The downloaded payload gets encoded with base64 (schemes presenting binary data as text) or undergoes byte reversal. Both methods increase the malware’s chances of passing undetected by antivirus programs. The fetched content constitutes *.dll and *.exe files.
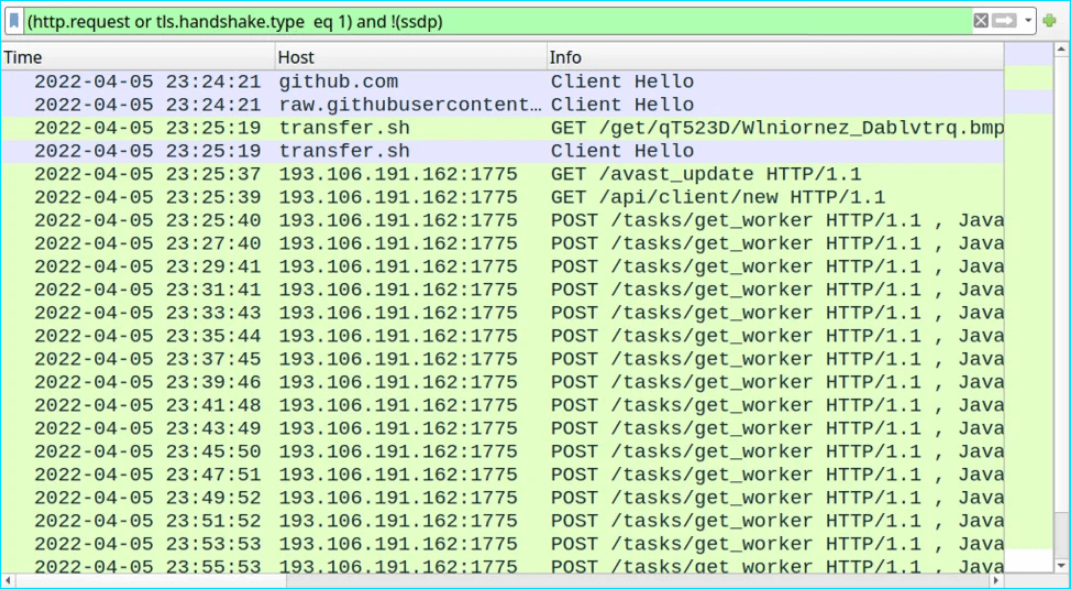
The hacker’s plan succeeds as a malicious executable gets assembled on the victim’s computer, and it starts sending data to the server with 193[.]106[.]191[.]162 address. The file name is ‘qwveqwveqw,’ and it even gets itself a system registry entry. Meta steals passwords for cryptocurrency wallets and web browsers, namely Chrome, Firefox, and Edge. By the way, Meta alters PowerShell and Windows Security settings, excluding *.exe files from antivirus examination.
Brief information on Meta malware
The hacker community quickly reacted to the suspension of Raccoon Stealer malware. Its operators stopped selling and supporting the tool as one of the developers became a victim of the war in Ukraine. Meta, advertised as the successor of RedLine, is one of several stealers that arrived to occupy the vacant niche. Its monthly price on the 2Easy botnet marketplace is $125 and a lifetime subscription costs $1000. For a more thorough analysis of the Meta malware, consider reading the original report by Brad Duncan on the Internet Storm Center security forum.
RELATED: Why is the 2easy trading platform gaining popularity?