KELA analysts say that the 2easy trading platform is gaining popularity on the darknet, gradually becoming an important player in the sale of stolen data.
The company’s report states that the stolen information was collected from approximately 600,000 devices infected with malware.
2easy mostly sells so-called Logs, which are archives of data stolen by malware from hacked browsers and systems. Typically, such dumps include credentials, cookies, and information about stored bank cards.
I think you will also be interested to know: what is the darknet?
2easy was launched back in 2018, but the site has shown rapid growth since last year, since until recently the site sold data from only 28,000 infected devices and was considered a minor player in this market.
According to KELA experts, the sharp growth is due to the development of the platform and the stable quality of its offerings, which is why 2easy has earned itself a reputation and popularity in the hacker community.
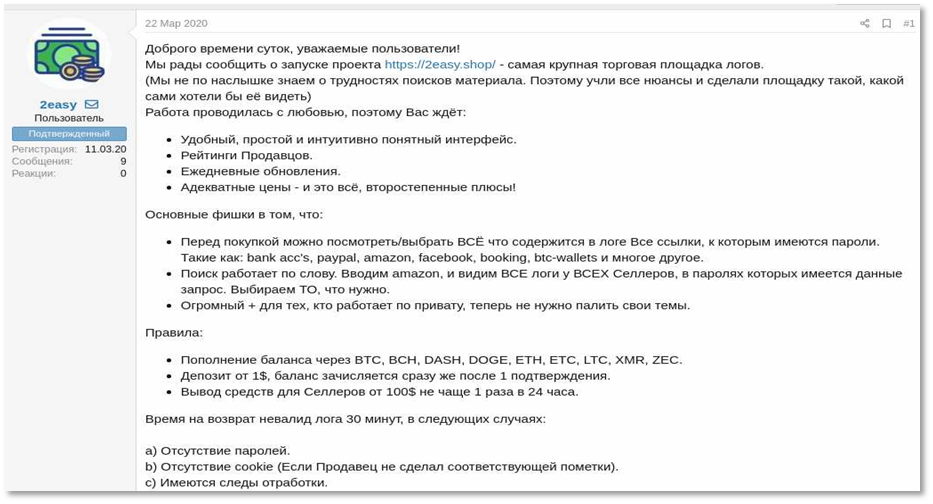
The site is fully automated, that is, anyone can create an account, add money to the wallet and make purchases without interacting with sellers directly. Data is available for purchase at an average of $ 5, which is about five times less than on the Genesis marketplace, and three times less than the average cost on the Russian black market.
Experts point out that the 2easy graphical interface is user-friendly and allows users to perform the following actions on the site:
- view all URLs where infected machines have logged in;
- search for URLs of interest;
- view a list of infected machines from which credentials for the specified site were stolen;
- check seller rating;
- check for tags assigned by sellers, which usually include the date the machine was infected, and sometimes additional notes;
- get credentials for selected purposes.
The only drawback of 2easy in KELA is the fact that the platform does not provide potential buyers with the ability to preview the product, that is, edited IP addresses or OS versions for devices from where the data was stolen.
Each “lot” purchased at 2easy comes in the form of an archive containing the stolen logs of the selected bot. The type of content in each case depends on the specific malware and its capabilities. However, in 50% of cases, merchants use the RedLine malware, and it is capable of stealing passwords, cookies, bank card data stored in browsers, FTP credentials, and much more.
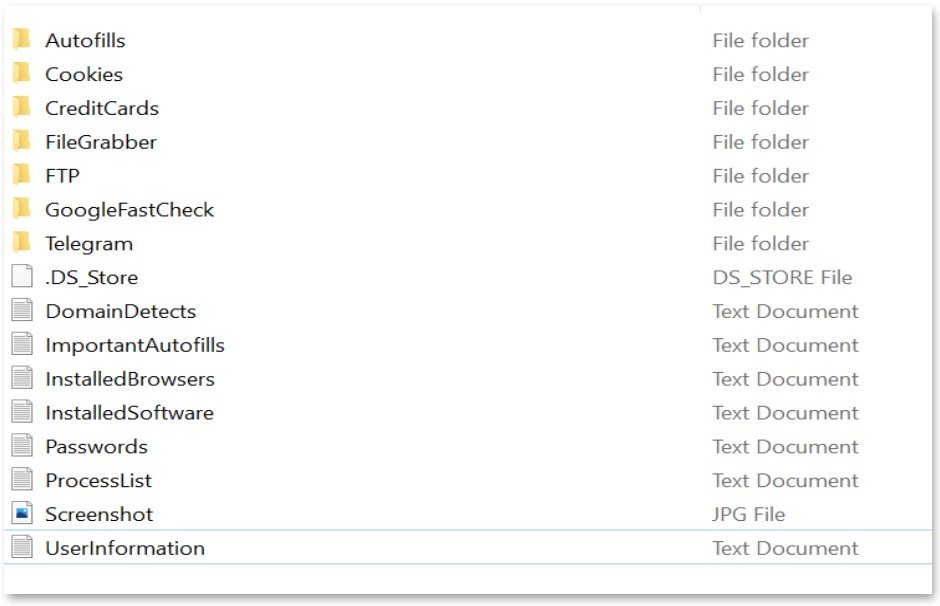
Five of the eighteen merchants working for 2easy use RedLine exclusively, while the rest use other malware, including Raccoon Stealer, Vidar and AZORult.
KELA analysts warn that such logs, as well as the information they contain, often become the key to penetrate corporate networks.
Let me remind you that I also talked about the fact that Researchers noticed that the darknet is discussing exploits as a service.