At the end of October, OpenSSL developers warned that the upcoming update to version 3.0.7 would close a critical vulnerability. Notably, this would only be the second critical bug in OpenSSL since 2016.
Now that OpenSSL 3.0.7 has been officially released, it turned out that fixes were released for two serious vulnerabilities at once, and the critical bug rating was revised, and it is no longer considered as such.
Version 3.0.7 fixed two vulnerabilities at once (CVE-2022-3602 and CVE-2022-3786) affecting OpenSSL versions 3.0.0 and higher (from 3.0.0 to 3.0.6).
Critical status should have been CVE-2022-3602, which is an arbitrary 4-byte stack buffer overflow that can cause crashes or lead to arbitrary code execution (RCE).
Ultimately, this vulnerability was rated high severity since according to the rules, a critical bug should affect widespread configurations, and only instances of OpenSSL 3.0 and later are vulnerable to CVE-2022-3602.
The second issue, CVE-2022-3786, can be exploited by a potential attacker through malicious email addresses and is capable of causing a denial of service through a buffer overflow.
Despite the assurances of the developers, some information security experts and vendors were quick to equate the discovery of a vulnerability in OpenSSL with the sensational Log4Shell problem, discovered in 2021 in the Log4J library.
Bleeping Computer notes that such a panic is premature: according to Censys, only about 7,000 systems running vulnerable versions of OpenSSL can be found on the network (among more than 1,793,000 unique hosts), and according to Shodan, there are about 16 such instances.
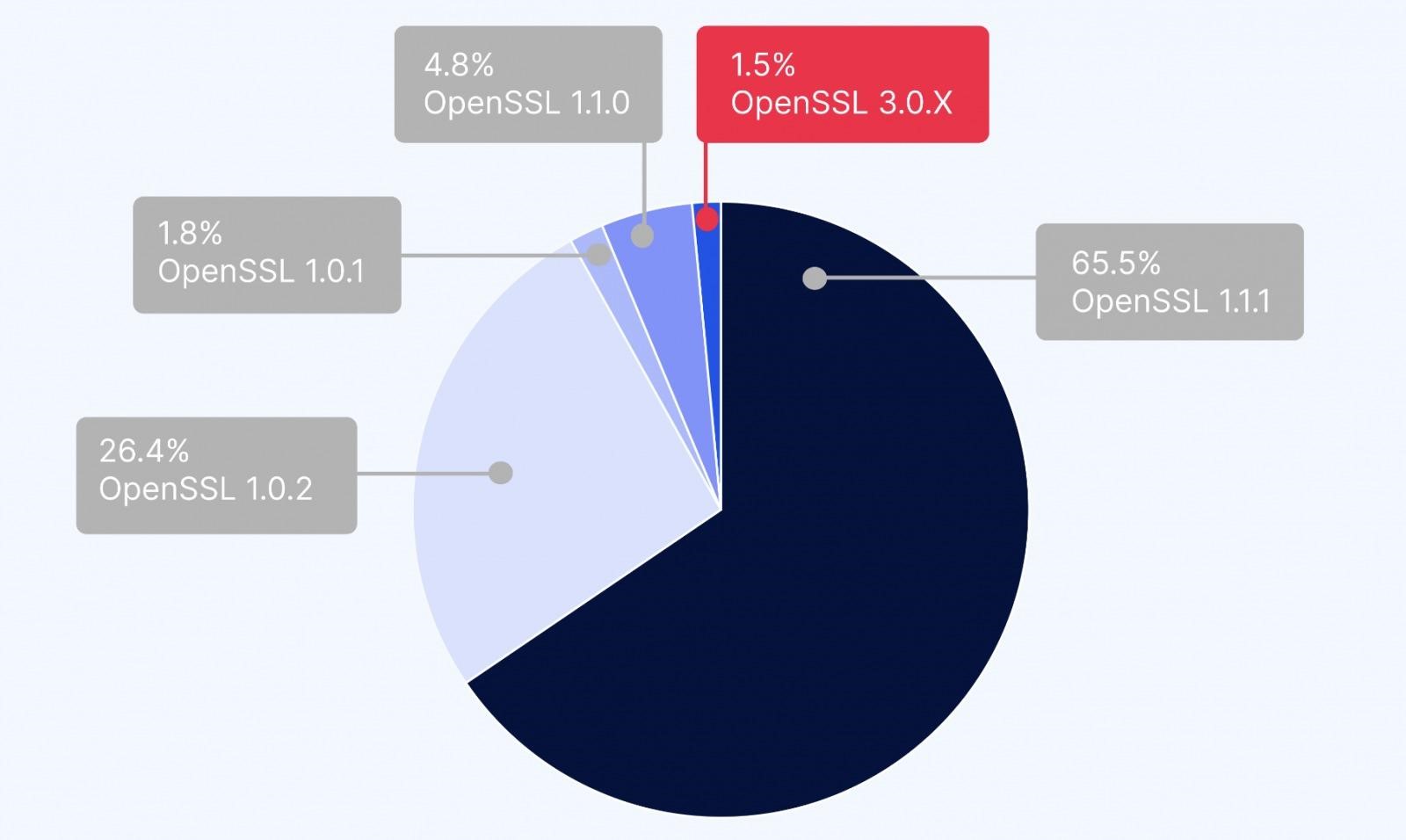
Cloud security company Wiz.io analysed deployments in major cloud environments (such as AWS, GCP, Azure, OCI, and Alibaba Cloud) and also reports that only 1.5% of all OpenSSL instances are affected by the latest vulnerability.
A separate page dedicated to CVE-2022-3602 and all related data was launched by well-known information security expert Marcus Hutchins. He explains that the problem occurs when validating an X.509 certificate and can be used to execute code using a malicious TLS certificate remotely. However, exploitation requires the malicious TLS certificate to be signed by a trusted CA.

The National Cybersecurity Center of the Netherlands has already begun compiling a list of products that are either affected or not affected by the latest bug.
It is worth saying that Akamai analysts have classified Redhat Enterprise Linux 9, Ubuntu 22.04+, CentOS Stream9, Kali 2022.3, Debian 12 and Fedora 36 distributions as vulnerable. The company’s experts have already published OSQuery and YARA rules that should help security specialists detect vulnerable products.





