The Emotet botnet resumed activity and began sending out malicious spam again after a five-month break, during which the malware practically “lay low.”
So far, Emotet is not delivering additional payloads to the infected devices of victims, so it is not yet possible to say exactly what this malicious campaign will lead to.
Let me remind you that we also wrote that Microsoft patches Windows AppX Installer vulnerability that spreads Emotet malware.
One of the first to notice the resumption of Emotet activity was experts from the Cryptolaemus group, which includes more than 20 information security specialists from around the world, who in 2018 united for a common goal – to fight Emotet. According to them, the malware, which had been idle since June 13, 2022, suddenly resumed its work in the early morning of November 2 and began sending spam around the world.
Proofpoint expert and Cryptolaemus contributor Tommy Madjar report that a new spam campaign is using previously stolen email threads to spread malicious Excel attachments. Among the samples already uploaded to VirusTotal, you can find attachments aimed at users from all over the world, written in different languages and with different file names. Malicious documents are disguised as various invoices, scans, electronic forms, etc.
Bleeping Computer journalists list the names of some of the malicious honeypot files:
- Scan_20220211_77219.xls
- fattura novembre 2022.xls
- BFE-011122 XNIZ-021122.xls
- FH-1612 report.xls
- 2022-11-02_1739.xls
- Fattura 2022 – IT 00225.xls
- RHU-011122 OOON-021122.xls
- Electronic form.xls
- Rechnungs-Details.xls
- Gmail_2022-02-11_1621.xls
- gescanntes-Document 2022.02.11_1028.xls
The researchers note that this Emotet campaign features a new template for Excel attachments, which contains revised instructions for users to bypass Microsoft Protected View.
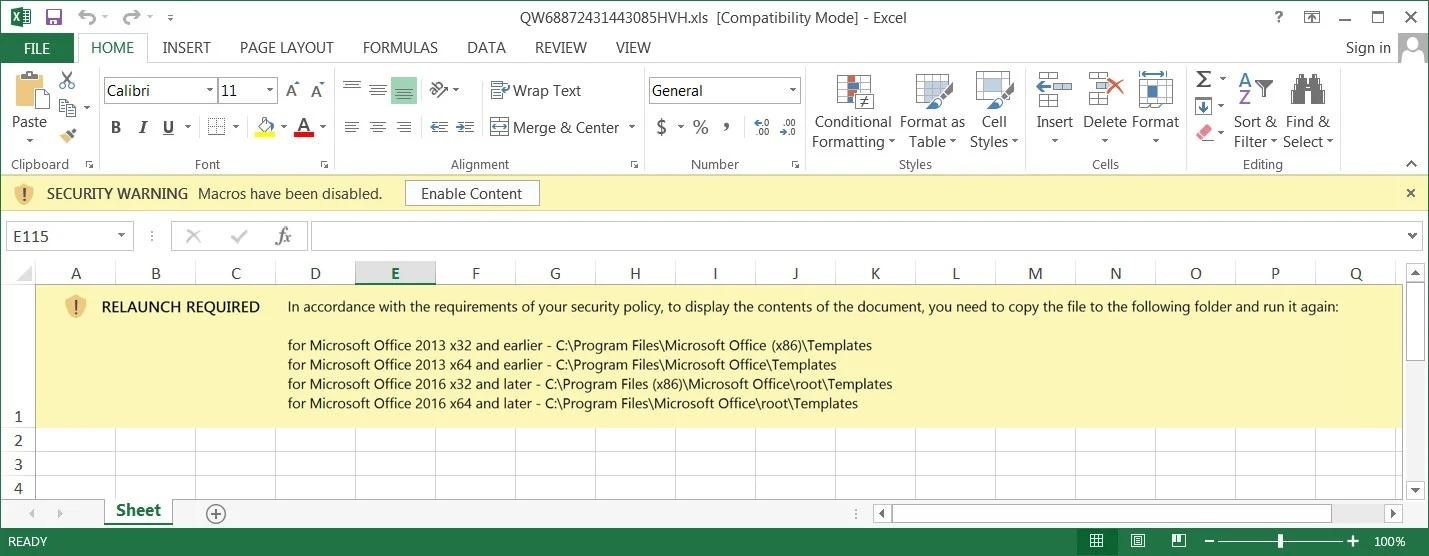
A malicious Excel file tells the user how to proceed
The fact is that Microsoft adds a special Mark-of-the-Web (MoTW) flag to files downloaded from the Internet (including email attachments). And when a user opens a Microsoft Office document containing the MoTW flag, it opens in Protected View mode, which prevents the execution of macros that install malware.
Therefore, Emotet operators now instruct users to copy the file to the trusted Templates folders, as this will bypass Protected View restrictions (even for a file marked MoTW).
If a malicious attachment is launched from the Templates folder, it immediately executes macros that download the Emotet malware to the victim’s system. The malware is loaded as a DLL into several folders with random names in %UserProfile%\AppData\Local, and then the macros run the DLL using regsvr32.exe.
The malware will then run in the background, connecting to the attackers’ control server to receive further instructions or install additional payloads. Let me remind you that earlier Emotet distributed the TrickBot Trojan, and was also caught installing Cobalt Strike beacons.
History of Emotet:
Emotet appeared in 2014, but only in the 2020s did it become one of the most active threats among malware.
The malware was distributed mainly through email spam, malicious Word, and Excel documents, etc. Such emails could be disguised as invoices, waybills, account security warnings, invitations to a party, or information about the spread of the coronavirus. In a word, hackers will carefully follow global trends and constantly improve their bait emails.
Although Emotet once started as a classic banking Trojan, the threat has since evolved into a powerful downloader with many modules. Its operators have begun to cooperate with other criminal groups actively.
Having penetrated the victim’s system, Emotet used the infected machine to send spam further and installed various additional malware on the device. Often these were bankers such as TrickBot, miners, infostealers, as well as cryptographers like Ryuk, Conti, ProLock.
Europol called Emotet “the most dangerous malware in the world” and also “one of the most prominent botnets of the last decade.”
An attempt to eliminate the botnet, undertaken by law enforcement officers in 2021, was unsuccessful. At the end of the year, the malware returned to service, teaming up with Trickbot to “get back on its feet.”
However, experts warned about the active growth of Emotet, and last summer, it was noticed that the malware acquired its own module for stealing bank cards.





