ESET specialists discovered the KryptoCibule malware, which has been active since 2018 and steals cryptocurrency from Windows users in the Czech Republic and Slovakia (these countries accounted for 85% of infections).
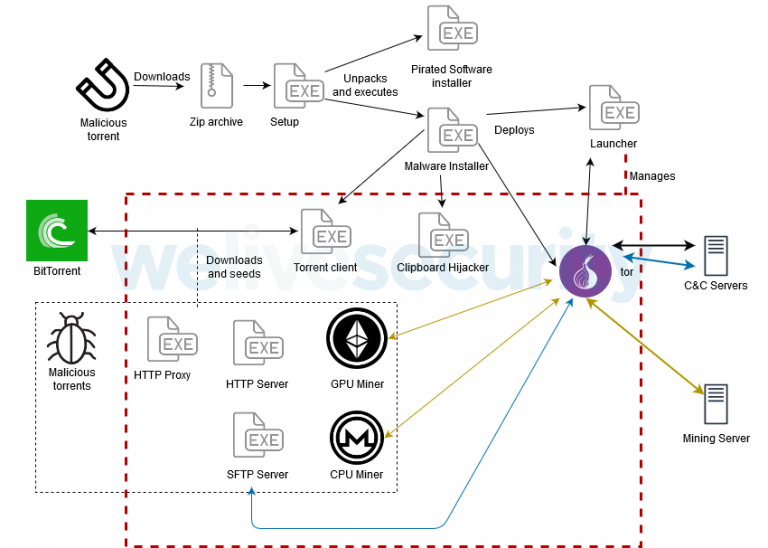
KryptoCibule has three main functions and is capable of: installing cryptocurrency miners on victims’ systems (CPU and GPU miners are used to mine Monero and Ethereum cryptocurrencies), steal files associated with cryptocurrency wallets, and change wallet addresses in the OS clipboard.
“It uses the victim’s resources to mine coins, tries to hijack transactions by replacing wallet addresses in the clipboard, and exfiltrates cryptocurrency-related files, all while deploying multiple techniques to avoid detection. KryptoCibule makes extensive use of the Tor network and the BitTorrent protocol in its communication infrastructure”, — report ESET specialists.
All elements of the “triple threat” for cryptocurrencies were added to the KryptoCibule code gradually, that is, the developers have been improving their malware for two years, and now the malware has turned into a complex multi-component threat, far exceeding the total mass of other malicious programs.
Now KryptoCibule is distributed mainly through torrents with pirated software.
“KryptoCibule is spread through malicious torrents for ZIP files whose contents masquerade as installers for cracked or pirated software and games”, – write ESET experts.
Most of the infected torrents were found on the uloz[.]to site, which is popular in the Czech Republic and Slovakia. The mentioned installer ensures the stability of the malware and its constant presence in the system (through scheduled tasks), and then installs KryptoCibule itself on the victim’s machine.
The researchers write that KryptoCibule uses Tor to communicate with the control servers on the darknet, while a torrent client is used to download torrent files that are responsible for downloading additional modules (proxy servers, mining modules, as well as HTTP and SFT servers).
Interestingly, KryptoCibule checks for antivirus software on victims’ computers, but only looks for ESET, Avast and AVG products. All three companies are based in the Czech Republic and Slovakia. Since the malware targets users from these countries, it seems that hackers believe that only these antiviruses can be installed on the computers of potential victims.
Let me remind you that there were cooler cases: I talked about the fact that hackers cracked European supercomputers and forced them to mine cryptocurrency.

