A proxy botnet, “Socks5Systemz”, uses malware loaders to infiltrate computers across the globe. Attackers have infected about 10,000 devices and organized a full-fledged proxy service based on it.
Socks5Systemz Dropper Malware Overview
A recent analysis from Bitsight has revealed the existence of a new malware sample called the Socks5Systemz proxy botnet. Although it has been active since 2016, it has remained unnoticed until now. The primary aim of this malware is to convert the infected devices into traffic-forwarding proxies, enabling malicious, illegal, or anonymous activities.
Threat actors can access this covert service by paying between $1 and $140 in cryptocurrency. Depending on the sum, malware developers offer wider functionality to the user. The Socks5Systemz botnet is typically spread through malware such as PrivateLoader and Amadey, which is commonly propagated through phishing, exploit kits, and malware downloaded from P2P networks.
How does Socks5Systemz Work?
The Proxy Bot Analysis report describes a harmful computer program about 300 KB in size. It creates a specific ID based on the date of the Windows directory on the computer it infects. When it is first run, it saves the current time, downloads a PDF file from a particular website, and saves it to the computer. It then tries to find a way to communicate with a C2 server, which is controlled by the person who created the bot.
If it can’t connect through the method it tries first, it sends an HTTP request to a specific website asking for the IP address of a valid C2 server. Once it connects to a valid C2 server, it can execute various commands, including “idle,” “connect,” “disconnect,” “updips,” and “upduris.” The “connect” command is vital because it allows the bot to become part of a group of available proxies that can be used to forward traffic on behalf of clients.
Expanding the Proxy Network
Experts have mapped a control infrastructure that includes 53 proxy bots, backconnect, DNS, and address acquisition servers. These servers are mainly spread across European countries, such as France, the Netherlands, Sweden, and Bulgaria. Since October, analysts have discovered 10,000 unique communication attempts via port 1074/TCP with the identified backconnect servers, which indicates that there are approximately 10,000 victims.
Overall, the Socks5Systemz proxy botnet has a worldwide impact, with infections observed across the globe. The highest number of infections has been reported in India, the United States, Brazil, Colombia, South Africa, Argentina, and Nigeria. However, the absence of infected systems communicating with backconnect servers in Russia, combined with other clues uncovered during the research, suggests that the operators of this service may be based in Russia.
The Proxy Service
An investigation into the botnet infrastructure revealed a Telegram user named “boost” who shared a screenshot of an account checker tool using the IP addresses of backconnect servers as proxies. This discovery showed that “boost” sells compromised accounts and access to the proxies.
Using a Telegram bot called “BoostyProxy,” “boost” established a complete proxy service. The service offers two subscription options: “Standard” and “VIP.”
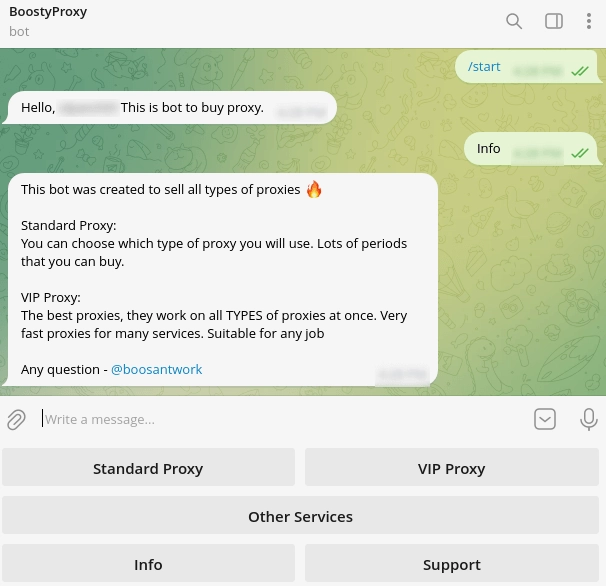
The Standard subscription permits using a single proxy type with no multithreading, while the VIP subscription offers more flexibility, supporting various proxy types (socks4, socks5, and HTTP) and multiple threads. Here are the pricing options for both subscription tiers: Standard starts from $1 for one day with Single Thread and ends at $28 for three months. VIP starts from $22 for one day with 100 Threads and ends at $4000 for three months with 5000 threads. All payments are made using cryptocurrency through the Cryptomus Crypto Payment Gateway.
Protection Against Botnets
The discovery of the Socks5Systemz proxy botnet highlights the ongoing danger that cybercriminals pose to the digital world. This botnet can harm individuals and an entire network of compromised systems, aiding in various types of cybercrime. To keep your systems and network safe from the Socks5Systemz proxy botnet and other similar threats, follow these steps:
- Use Endpoint Security. Install updated antivirus and anti-malware software to detect and prevent threats.
- Keep Software Up to Date. Regularly update your operating systems and software applications to patch any vulnerabilities that can be exploited.
- Boost Network Security. Use intrusion detection and prevention systems to monitor network traffic for suspicious activity. Implement firewalls to prevent unauthorized access to your network and critical assets. Use network segmentation to limit lateral movement within the network in case of a breach.
- Educate Employees. Teach your employees the risks of clicking suspicious links and downloading attachments from unknown sources. Please encourage them to use strong and unique passwords and enable two-factor authentication.
- Use Email Filtering. Implement email filtering and phishing detection solutions to block malicious emails. Train employees to recognize phishing attempts and avoid clicking on harmful links.
- Perform Regular Data Backups. Please back up your data regularly and store it in a secure, isolated environment. Test these procedures to ensure data can be restored quickly in case of an incident.
- Monitor Network Activity. Continuously monitor your network for any unusual activity or connections that may indicate a compromise.
- Stay Informed. Subscribe to threat intelligence services to stay informed about emerging threats.