Stopabit Virus
Stopabit is an unwanted application that has almost no useful functionality. Users…
Taskbarify Unwanted Application
Taskbarify is unwanted software (like a Movidown)that claims it is a tiny…
Socks5Systemz Proxy Service Infects 10,000 Systems Worldwide
A proxy botnet, "Socks5Systemz", uses malware loaders to infiltrate computers across the…
Botnet of 400,000 Devices Used as Proxy Nodes Uncovered
Cybercriminals used stealthy malware to create a botnet of 400,000 proxy servers.…
Proxyjacking: The Latest Cybercriminal Invention In Action
Today, in the constantly changing world of cyber threats, attackers always look…
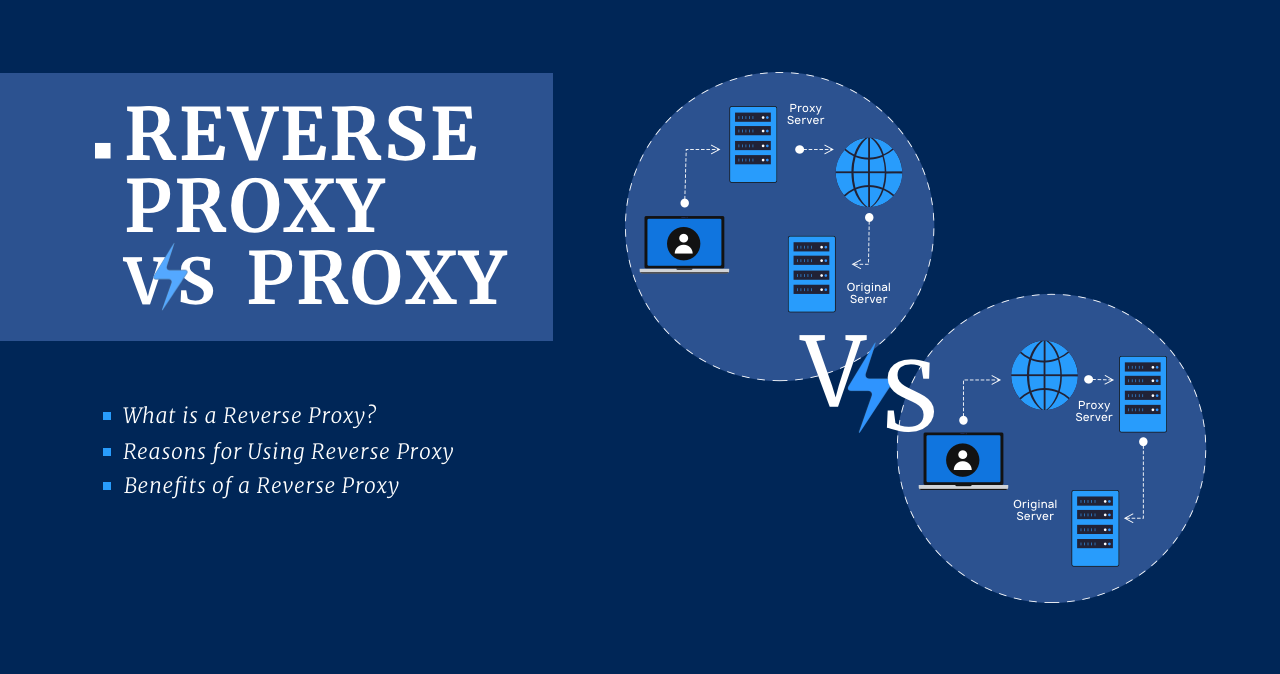
Reverse Proxy vs Proxy
What is a Reverse Proxy? A reverse proxy is the same server…
VPN, Proxy, or Tor: Differences, Meaning
You've probably heard the words VPN, Proxy, and Tor. You may even…