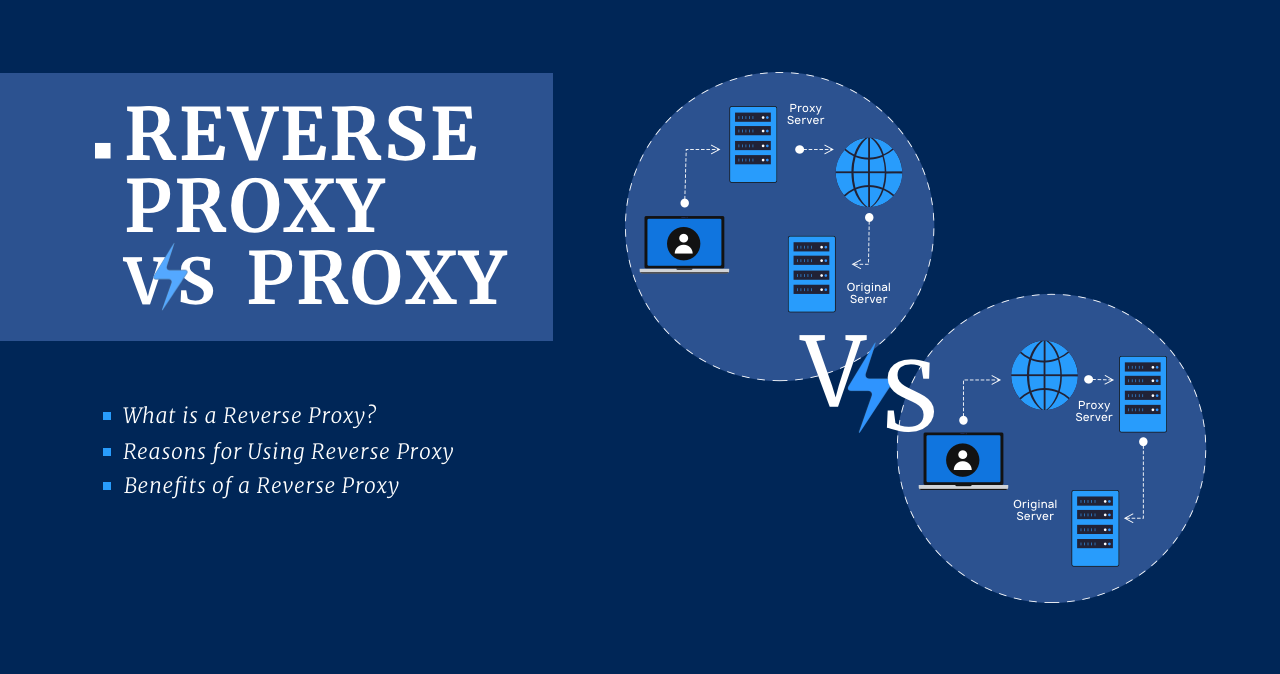
What is a Reverse Proxy?
A reverse proxy is the same server but is in front of a web server. Depending on its configuration, it allows or refuses the external connection to reach the endpoint. Reverse proxies are used to improve security, performance, and reliability. To understand how a reverse proxy works and what benefits it can provide, let’s first remember what a reverse proxy server is.
Proxy Server Meaning
A direct proxy server, or web proxy, is a server that sits in front of a client’s computer. When this computer sends requests to sites on the Internet, the proxy takes control over these requests. It then communicates with the Web servers on behalf of these clients as an intermediary. Suppose we have three computers participating in a typical direct proxy communication:
- A: The user’s home computer
- B: Direct proxy server.
- C: The source server of the website (the storage location of the website data).
Computer A will talk directly to computer C in a standard Internet connection. That is, the client sends requests directly to the origin server, and the origin server responds to the client. When a direct proxy server is set up, A will instead send requests to B, which will forward the request to C. C will then send a response to B, which will deliver the response back to A.
Reasons for Using Reverse Proxy
As you can already guess, reverse proxy is an intermediary on the incoming connection that may decide whether it should be allowed. Why would anyone want to add this extra middleman to their online activities? There are several main reasons why someone might need to use a direct proxy:
- To avoid the restrictions on browsing. For example, governments, schools, and other organizations sometimes use firewalls to restrict their users from accessing specific Websites. To bypass these restrictions, you can use a direct proxy since the connection will not be straightforward to the sites visited but to a proxy server.
- To block access to certain content. It happens the other way around. Proxy servers can be set up to block a group of users from accessing specific sites. For example, a school network may block particular websites such as Facebook or other social networking sites.
- To protect your identity on the Internet. In some cases, ordinary Internet users want more anonymity on the Internet. In other cases, Internet users live in countries without freedom of speech, and the government can impose severe sanctions on political dissidents. In such countries, criticism of the government on a web forum or social media can lead to heavy fines and sometimes even imprisonment for these users. Suppose one of these dissidents uses a proxy server to connect to the website where they post politically sensitive comments. In that case, their IP address will be harder to trace. This is because only the IP address of the proxy server will be visible.
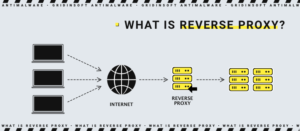
Proxy Server VS Reverse Proxy
The main difference between the proxy server and a reverse proxy server is that it is in front of one or more web servers and intercepts client requests. At the same time, the forward proxy is in front of the clients. With a reverse proxy, all client requests to the website server will be intercepted by the reverse proxy. The reverse proxy will send requests and receive responses from the source server.
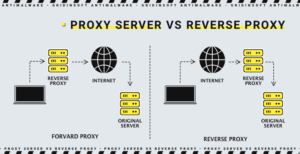
In simplistic terms, you could say that the forward proxy sits in front of the client and ensures that no source server ever communicates directly with that particular client. On the other hand, the reverse proxy server sits in front of the source server. It ensures that no client ever communicates directly with that source server. Once again, let’s introduce this by naming the computers involved:
- D: Any number of users’ home computers
- E: It is a reverse proxy server
- F: one or more source servers
Typically all requests from D go directly to F. F sends the responses directly to D. In the reverse proxy case, all requests from D go now to E. E will send its requests and receive responses from F. E will then forward the corresponding responses to D.
Benefits of a Reverse Proxy
Here are the main benefits of reverse proxy:
- Protection against attacks. With a reverse proxy, a website does not have to disclose the actual IP address of its origin server(s). This can protect the website from possible targeted attacks, such as DDoS attacks. Instead, attackers will only be able to target the reverse proxy server, which often has better protection and more resources to fend off a cyberattack.
- Global Server Load Balancing (GSLB) – In this form of load balancing, a website can be distributed across multiple servers worldwide, and the reverse proxy will send clients to the server closest to them geographically. This reduces the distance requests and responses travel, minimizing load times.
- Caching. A reverse proxy server can also cache content, which improves performance. For example, suppose a user in Paris visits a website with a reverse proxy server with web servers in Los Angeles. In that case, the user can connect to the local reverse proxy server in Paris, which would then have to communicate with the source server in Los Angeles. The proxy server can then cache (or temporarily store) the response data. Subsequent Paris users browsing the site will receive a locally cached version from the Paris reverse proxy server, resulting in much better performance.
- SSL Encryption. Encrypting and decrypting SSL (or TLS ) communications for each client can require significant computing resources for the source server. However, the reverse proxy can be configured to decrypt all incoming requests and encrypt all outgoing responses, freeing up valuable resources on the source server.
Conclusion
Looking at the above, we see that even though they all have the word “proxy” in their names, they are not the same thing. They have their scope based on their position in the request-response loop. However, it is essential to know that each one moderates your traffic and can either block your requests or allow them.