The Security Blog From Gridinsoft
Fullerton India Hacked, LockBit Leaks 600GB of Data
Fullerton India, a large lending institution from India, appears to be hacked back in early April 2023. It is confirmed…
Ransomware Attacks Increasingly Using AuKill Malware to Disable EDR
A new cybercrime tool called “AuKill” has emerged, which attackers use to disable endpoint detection and response (EDR) defenses used…
AI Generated Video Based on Mouse Brain Signals
A team of researchers from the EPFL has developed an AI tool that can interpret rodent brain signals in real…
BlackCat Group Leaks Western Digital Data to the Network
The operators of the ransomware BlackCat (aka ALPHV) have published screenshots of Western Digital’s internal emails and video conferences. The…
LOBSHOT malware steals cryptowallets, exploits Google Ads
LOBSHOT, a recently-detected malware family, appears to be a new strong player in the malware market. Carrying a combination of…
IPStorm botnet now attacks Android, macOS and Linux devices
For the first time, Anomali specialists noticed the IPStorm in…
Microsoft estimated that ransomware attacks take less than 45 minutes
Microsoft analysts have prepared a traditional Digital Defense report, in…
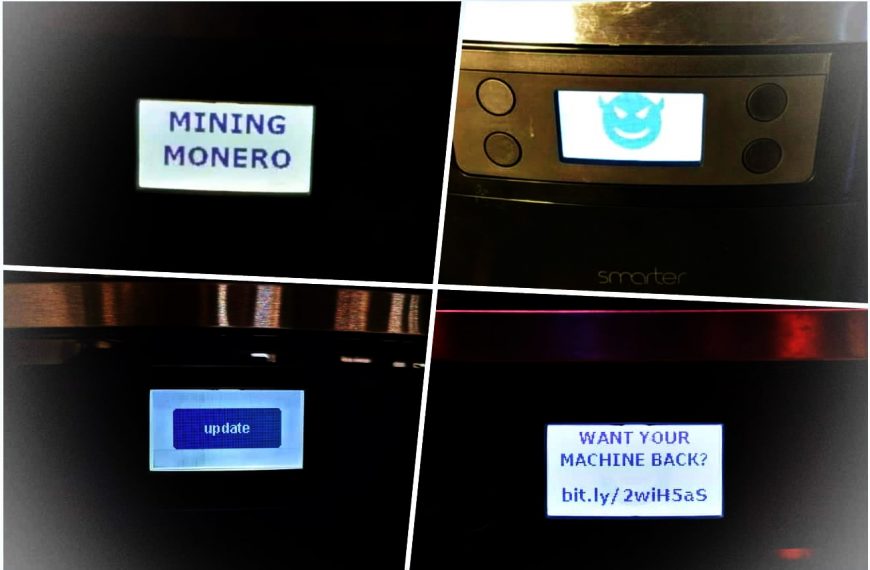
Avast expert taught Smarter Coffee machine to ransom money
Back in 2015, experts from Pen Test Partners talked about…
Attackers can bypass TikTok multi-factor authentication through the site
Journalists of the ZDNet publication, citing one of their readers,…
Windows XP source codes leaked
4chan has published a 42.9 GB torrent file, which contains…
Alien malware steals passwords from 226 Android apps
ThreatFabric analysts have discovered a new Android malware Alien. The…
CISA experts warned about the growth of LokiBot infostealer activity
Specialists from the Agency for Cybersecurity and Infrastructure Protection, organized…
Microsoft left open one of the internal servers of the search engine Bing
Ata Hakcil, cyber security specialist at WizCase, discovered that Microsoft…
Spammers hide behind hexadecimal IP addresses
Trustwave experts have discovered that pharmaceutical spam attackers have started…
Mozilla completely stops development of Firefox Send and Firefox Notes
This summer, I talked about how ZDNet journalists drew attention…
Chinese hackers attack US organizations and exploit bugs in F5, Citrix and Microsoft Exchange
The Department of Homeland Security (DHS CISA) Cybersecurity and Infrastructure…
Qbot Trojan Entered The Top Of The Most Widespread Malware
Check Point has released its monthly Global Threat Index for…