The Security Blog From Gridinsoft
MSMQ Vulnerability Allows Remote Code Execution
Recent update released by Microsoft, an April Patch Tuesday, revealed a severe vulnerability in Microsoft Message Queueing mechanism. That vulnerability…
Hackers Infect eFile Tax Filing Service with Malware
The eFile service, used by many Americans to file their tax returns and authorized by the US Internal Revenue Service…
Rilide Malware Steals Data from Chromium Browsers
Trustwave SpiderLabs specialists spoke about the new Rilide malware, which steals confidential data and cryptocurrency, targeting Chromium browsers. Basically, Rilide…
Rorschach Ransomware Analysis
Recent research from the CheckPoint Research team revealed a new ransomware sample that can potentially beat all samples currently present…
Rorschach’s New Ransomware Is Named the Fastest to Date
Check Point analysts have discovered a new ransomware, Rorschach ransomware that has already been used to attack an unnamed American…
Ukraine’s largest IT company SoftServe has been attacked by a ransomware
One of the largest IT companies in Ukraine, SoftServe (number…
KryptoCibule malware steals cryptocurrency from Windows users
ESET specialists discovered the KryptoCibule malware, which has been active…
Shlayer malware bypassed Apple security checks
Security expert Peter Dantini discovered that the Shlayer malware bypassed…
Scientists have developed an attack that allows not to enter a PIN code while paying with Visa cards
Scientists from the Swiss Higher Technical School of Zurich have…
Elon Musk confirmed that the Russian offered a Tesla employee a million dollars for hacking the company
Earlier this week, the US Department of Justice announced the…
Twitter and Graphika neutralized Dracula propaganda botnet
Experts from the Graphika research group talked about how they…
Hackers use in attacks malicious plugin for 3Ds Max
Bitdefender experts have discovered a hacker group that is attacking…
SpiKey technique allows opening the lock by recording a sound of a turning key
Scientists from the National University of Singapore have published a…
Ukrainian cyber police in cooperation with Binance detained operators of 20 cryptocurrency exchangers
Since January 2020, the Ukrainian cyber police began cooperating with…
Microsoft developers will stop supporting classic Edge and IE 11
Microsoft said it would stop supporting classic Edge and IE…
Vulnerabilities in Amazon Alexa opened access to user data for outsiders
In June this year, researchers from Check Point discovered a…
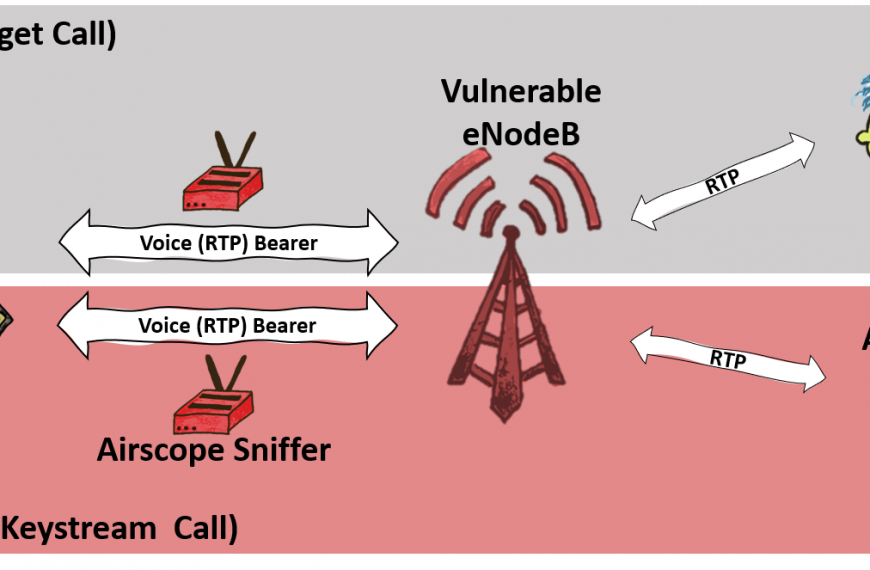
ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Experts from the Ruhr University and New York University in…