Experts from the Ruhr University and New York University in Abu Dhabi have published information about the ReVoLTE attack, which allows decrypting and overhearing other people’s conversations on LTE networks.
This attack already has its own website, and at the Usenix conference researchers demonstrated a video presentation of their report.
I’d like to note that earlier the same research company discovered the IMP4GT problem, which affects almost all modern devices with LTE support, namely smartphones, tablets, IoT devices.
The bug allows imitating another user on the operator’s network, which means that an attacker will be able to subscribe for paid subscriptions at the expense of other people or publish something (for example, secret documents) under someone else’s name.
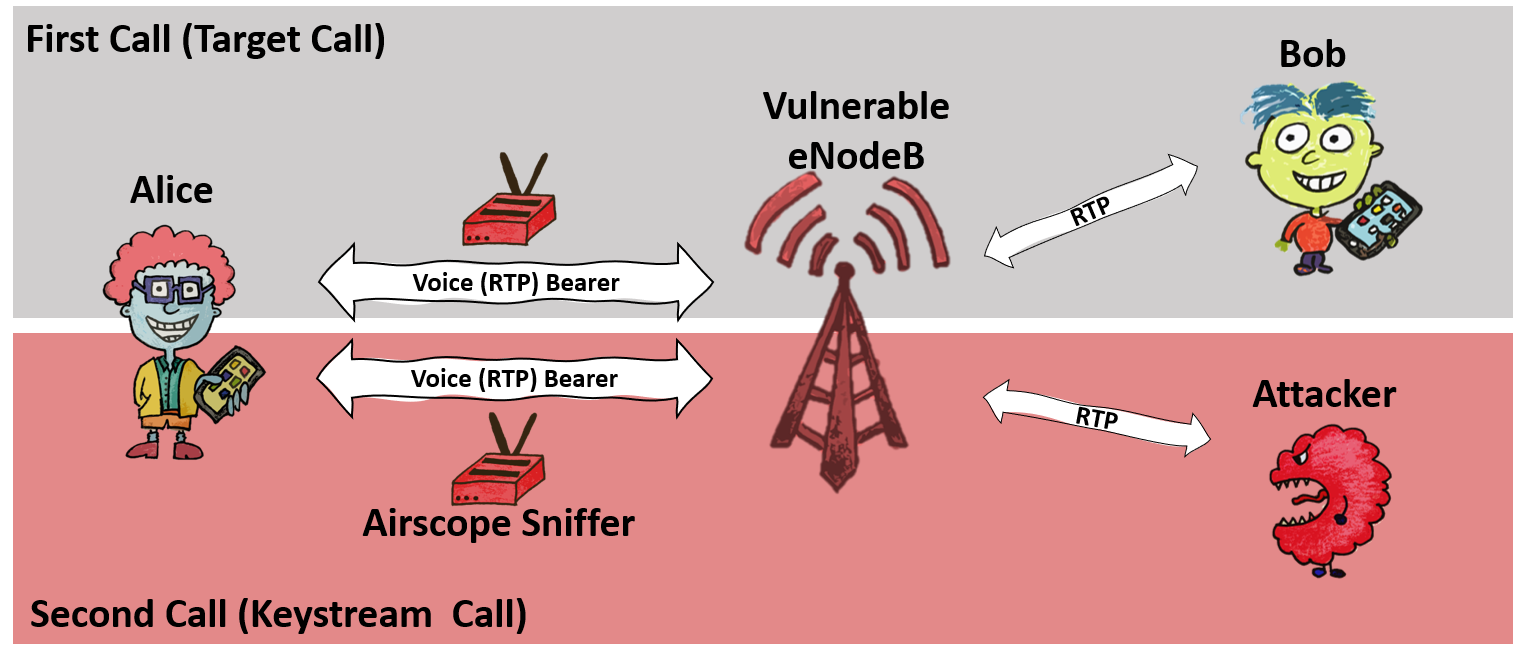
“The ReVoLTE attack is based on the fact that many mobile operators use the same encryption key to protect different 4G voice calls passing through the same base station”, – say information security specialists.
Scientists have conducted a series of “field tests” of their attack, analyzing the operation of random base stations throughout Germany, and it turned out that 80% of them use the same encryption key (or a key that is easy to predict), which puts users at risk.
The fact is that by default the VoLTE standard supports encrypted calls, and mobile operators must choose their own encryption key (stream cipher) for each call. Normally, the key should be unique for each call. Unfortunately, it turned out that often voice calls are encrypted with the same key or key that is easy to predict.
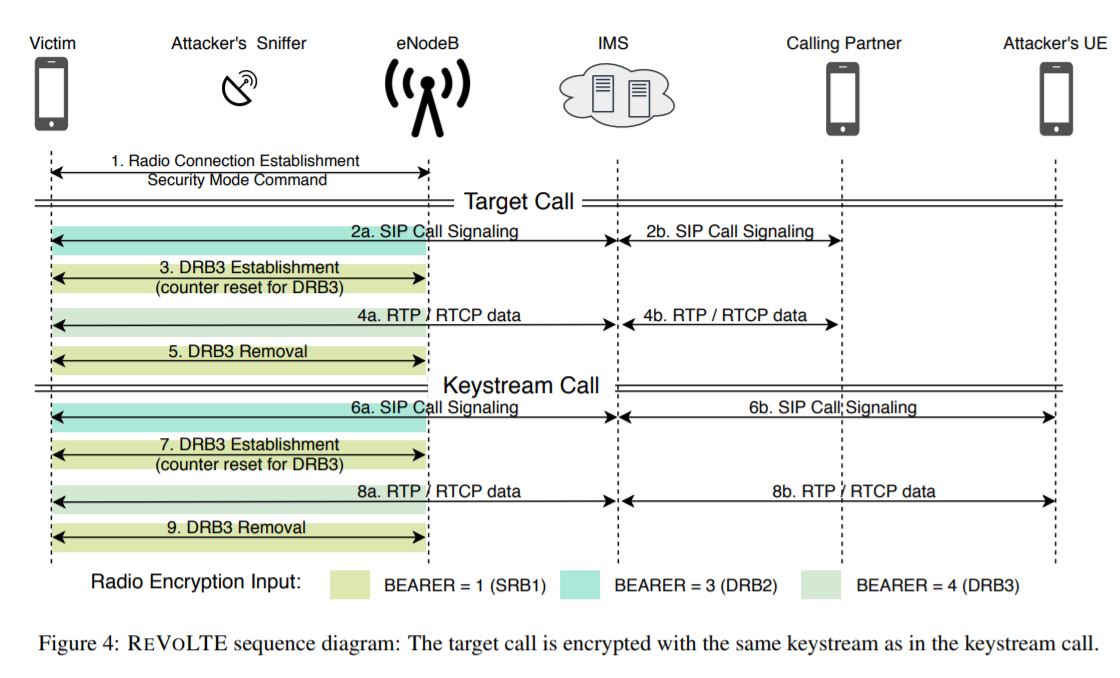
This problem usually manifests itself at the level of base stations, which reuse the same stream cipher or predictable algorithms to generate encryption keys. As a result, an attacker can record a conversation between any two 4G users connected to a vulnerable base station and then decrypt it.
All a hacker needs to carry out an attack is to call one of the victims and record the conversation so that this call is encrypted with the same (or predictable) encryption key. The only limitation is that the attacker must be connected to the same base station as his victim, and the attacker must act quickly: the attacker’s call must be completed within about 10 seconds after the targeted call ends.
This can be done with hardware that will cost about $7,000 in total. While the price may seem high, the researchers note that generally the 3G and 4G spoilers used by law enforcement and criminal groups cost not less.
“The longer the attacker talks to his victim, the more he will be able to decrypt from the previous conversation. For example, if the attacker and the victim spoke for five minutes, the attacker would later be able to decrypt five minutes of the previous conversation”, — explain the researchers.
Essentially, the hacker only needs to compare the two entries and determine the encryption key.
Back in December 2019, researchers reported about the problems to both German mobile operators and the GSMA. As a result, the GSMA released updates to the 4G protocol that protect against ReVoLTE attacks. Unfortunately, experts point out that even if German mobile operators and their users are now safe, other operators around the world may still be vulnerable.
Experts have created and published on GitHub a special application for Android that can use mobile operators to test their networks and base stations for vulnerabilities to ReVoLTE. The app requires a rooted device that supports VoLTE and runs on the Qualcomm chipset.