Cybersecurity experts have published a report on worrying ransomware statistics. A survey of 435 cybersecurity professionals identified gaps, misunderstandings, and obstacles regarding organizational security, preventing attacks, and eliminating extortion. Analysts conclude that most of these organizations will likely face a ransomware attack this year – simply because.
What is ransomware?
The name of this malware has been repeated too often over the last few years. Ransomware is malicious software that aims to block access to a computer system or encrypt files until the victim pays a ransom. A cyber attack can cause significant disruption, financial loss, and potential data breaches. Throughout the last 7 years, it became a major threat to companies, particularly to the data they hold.
When a network or computer is infected with ransomware, the malware typically encrypts the victim’s files, making it inaccessible. The attackers then demand a ransom payment, usually in cryptocurrencies like Bitcoin, to provide the decryption key or release the system. Typically for attacks on companies, hackers also steal any data they can get their hands on in the company network. They ask for a separate ransom to prevent publishing it as well. Some gangs practice blackmailing the company, threatening to publish the facts of the security incident.
Ransomware can spread through various means, including email attachments, malicious downloads, or by exploiting vulnerabilities in computer systems. Once the ransomware gains access to a system, it quickly encrypts files, making them unreadable without the decryption key.
The most dangerous ransomware:
Some notorious ransomware families that have caused significant damage and disruption in recent years include:
LockBit
The LockBit group is a notorious gang of threat actors who have been spreading their ransomware since 2019. They are constantly updating their malware to make it harder to stop. The group is also known for its media presence – they frequently give interviews and participate in forum discussions. Conti group disbanded in 2022. After that LockBit has become a prominent player in the market, responsible for over 40% of all attacks at times. Although this number varies, they are among the most successful cybercrime gangs.
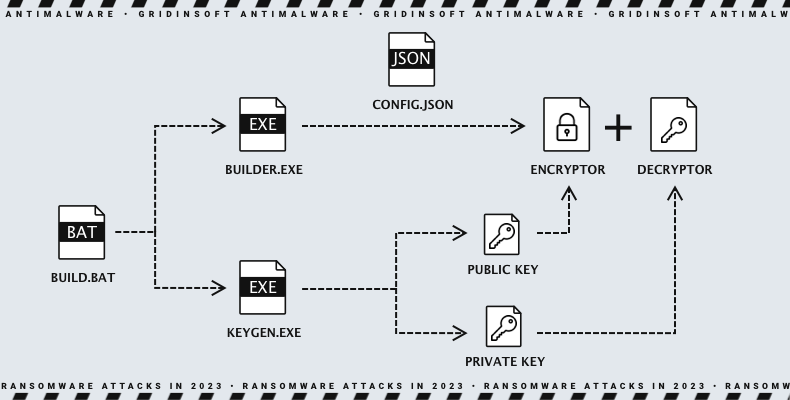
LockBit owes its success to its ransomware and additional software that facilitate cyberattacks. These programs ensure the secure, speedy, and dependable encryption and exfiltration of files. Initially, LockBit’s ransomware and data exfiltration software was already the fastest. However, with regular updates, hackers made it even faster over time. In comparison, no widely-used ransomware is nearly as efficient, except for the Rorschach ransomware, which boasts faster encryption. Besides speeding up encryption and exfiltration, updates enhance network infrastructure and bug bounty programs.
Vice Society
The Vice Society is a russian-based invasion, exfiltration, and extortion group. The group first became known in 2021. They mainly focus on the education sector( universities, colleges, and schools). In some ways, this RaaS group is ahead of Lock Bit.
The FBI, Multi-State Information Sharing and Analysis Center (MS-ISAC), and Cybersecurity and Infrastructure Agency (CISA) issued a joint advisory this week warning that the Vice Society has started targeting the US education sector with ransomware attacks more than other sectors.
Cl0p
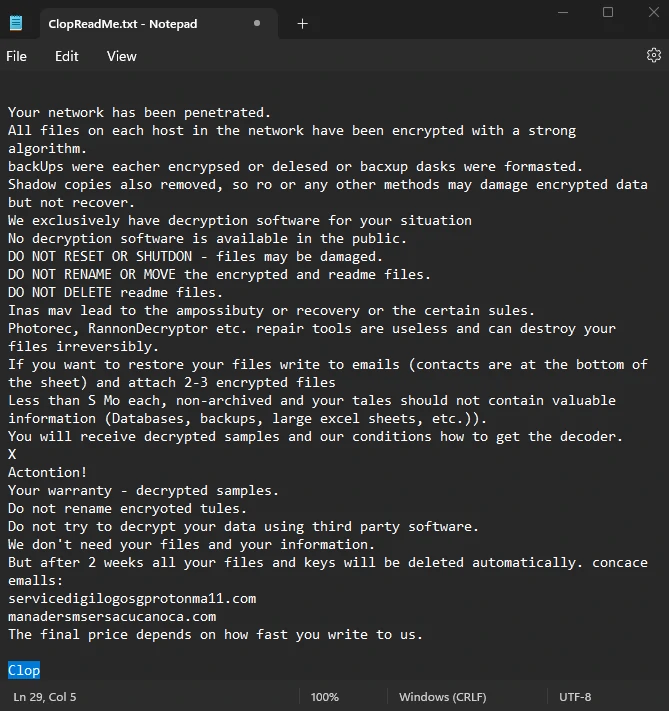
Cl0p is a ransomware gang that encrypts files on computers it infects using an RSA 1024-bit public key and RC4 encryption with 117 bytes of the key. One of the main ways Clop is spread is through spear phishing, which involves sending an email with a malicious attachment. The attached file has a certificate that makes it look legitimate to protection systems, making it harder to detect. In addition to the ransomware, the payload often includes an SDBOT worm that steals information.
According to a tweet from Microsoft Security Intelligence, Sangria Tempest (also known as ELBRUS and FIN7), a cybercrime group motivated by financial gain, has become active after long inactivity. In April 2023, were seen using the Clop ransomware in opportunistic attacks, marking their first extortion campaign since late 2021. Furthermore, it has been discovered that FIN7 has begun utilizing a new type of malware called Clop, which can be detected on Microsoft Files.
BlackCat
ALPHV, or BlackCat is an extortion group that has been in existence since November 2021. Specifically, it is a ransomware-as-a-service (RaaS) operation and one of the most sophisticated RaaS operations currently available. BlackCat ransomware is designed to be challenging to eliminate and may try to turn off antivirus software or other security measures. It can also alter system files and settings to ensure that it persists, making it harder to recover from the attack.
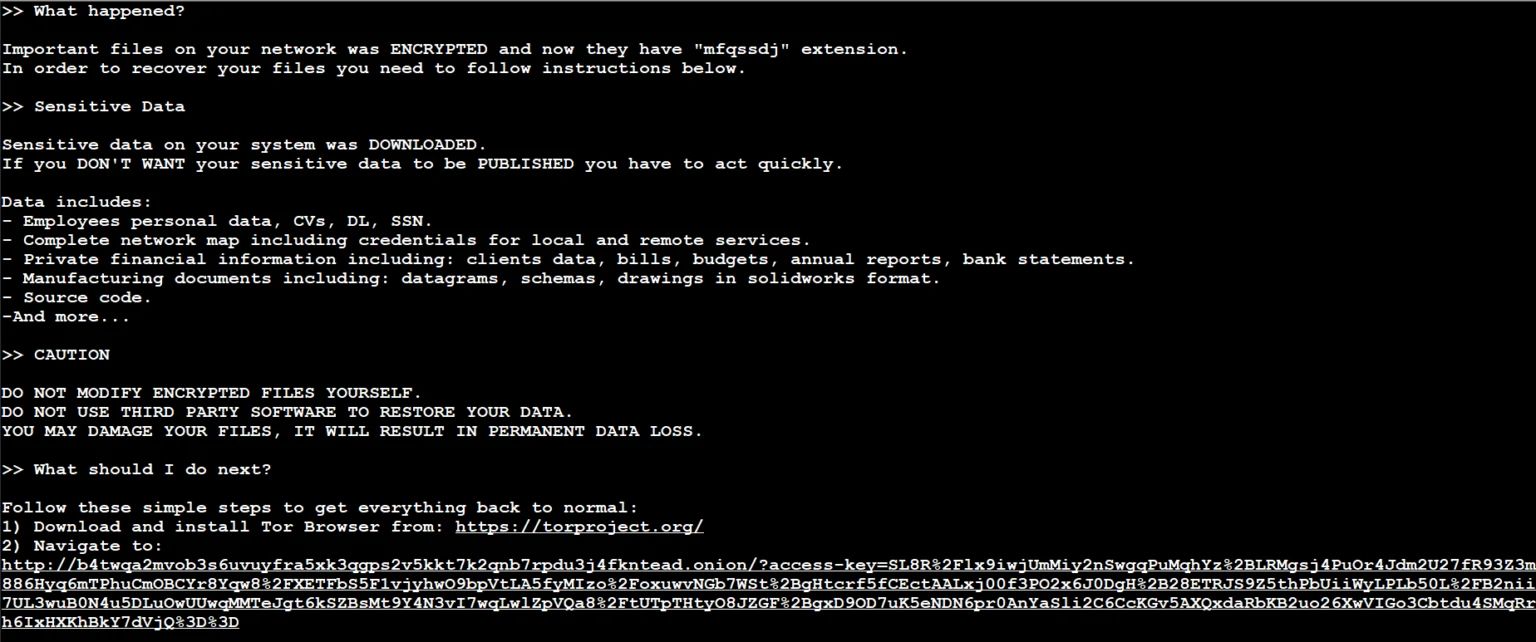
BlackCat uses malware-infected emails or website links to lure in unsuspecting victims. Once it infects a system, it spreads quickly throughout the entire network. This threat also employs the “triple extortion” technique, where attackers steal a copy of the victim’s data and encrypt it on their machine. Therefore, being vigilant and taking precautions to protect against such attacks is essential.
Royal
Royal Ransomware was discovered in 2022, and it quickly began hitting newsletter headlines. It has been evolving rapidly since then and has become one of the most dangerous ransomware campaigns of the year. The group responsible for it, Dev-0569, has been targeting many victims and has demanded large sums of money ranging from $250,000 to $2 million per compromise. In November 2022 alone, added 43 new victims to their list.
A type of ransomware called “Zeon” was first seen in September of last year but later renamed “Royal”. It may have been active since January 2022. Initially, it used an encryptor called BlackCat but later switched to its encryptor, which produced ransom notes similar to those used by Conti. After the name change, Royal started using its encryptor to generate ransom notes.
It’s important to note that the threat landscape constantly evolves, and new ransomware variants emerge regularly. Therefore, to stay up-to-date on the latest developments and most harmful ransomware types each year, it is advisable to follow trustworthy sources on cybersecurity and remain informed on current events in this industry.
Ransomware Report’s key findings in the current year:
- Many respondents (77%) have a mistaken belief that their endpoint security solution (EDR) can effectively shield their servers from malware attacks, which indicates overconfidence in their attack detection abilities.
- A lot of respondents have unrealistic expectations about the recovery time after a cyber attack. According to research, it usually takes weeks or even months to recover fully, but 35% of respondents think they can bounce back in just a few days.
- A survey showed that 76% of respondents were highly confident in their organization’s ability to prevent attacks. Still, only 35% were confident in their ability to recover data after it had been locked or encrypted by ransomware.
- A significant percentage of individuals reported that their financial information (69%), customer information (61%), and employee information (56%) are at risk.
Based on these findings, researchers emphasize moving from a purely preventive approach, such as EDR, to a more multi-level, comprehensive strategy, including the rapid containment of ongoing attacks. As a result, organizations can limit damage and reduce recovery time by implementing solutions that can quickly close active attacks by better protecting their valuable data, operations, and reputation.
EDR/XDR Is Ineffective?
EDR and XDR are cybersecurity solutions designed to investigate, detect, and respond to security incidents and threats in an organization’s network environment.
Shortly about EDR and XDR
EDR focuses on monitoring and protecting individual endpoints, such as laptops, desktops, servers, and mobile devices. It involves installing lightweight agents on endpoints that collect and analyze data about system events, processes, network traffic, and user behavior. EDR solutions provide real-time visibility into endpoint activities, detect and respond to suspicious or malicious behavior, and facilitate incident investigation and remediation.
XDR builds upon the capabilities of EDR by integrating and correlating data from multiple security sources across the organization’s entire network environment. It goes beyond endpoints and includes data from network devices, cloud services, email gateways, and other security decisions. Such as intrusion detection systems, firewalls, and secure web gateways.
So what?
The take regarding EDR/XDR ineffectiveness is somewhat true, but the more extended answer sounds different. “EDR/XDR with no auxiliary systems that extend visibility and boost response speed in the protected environment are not effective” – that is what it is about. Companies commonly think having one major software from the extensive list of security appliances available is enough. This, however, is not true – at least for the modern, rapid threat landscape.
Additional sources of information help the protective solutions better understand what is happening inside the network. Anomalous login time, accessing the network directory that was never touched before, connecting to the unknown external server – all these things should raise suspicion. And they do – if there is an user behavior analytics (UBA) solution running along with a protective one. Things like security orchestration, automation and response (SOAR) will also allow for a faster and all-encompassing response to a threat. It is like giving your guardsmen access to CCTV and centralized door lock control – and without it, they will have a weakened ability to protect your property.
How to avoid ransomware?
- Enhance cybersecurity, it’s important to limit the attack surface by blocking access to internal apps from the Internet and minimizing the number of vulnerable components.
- Prevent breaches, a cloud-native proxy architecture should be implemented to thoroughly scrutinize all traffic inline and at scale and enforce consistent security policies.
- Connecting users straight to applications instead of the network can prevent lateral movement while employing deception and workload segregation to contain threats.
- Inspecting all Internet-bound traffic, including encrypted channels, is crucial to prevent data theft. Network detection and response solutions will fit perfectly for that purpose.
- Stay informed about the latest threats and educate yourself and your team on safe online practices. Be cautious about sharing sensitive information online or with unknown individuals.
- Implement network segmentation: Separate your network into segments or zones to limit ransomware spread across your infrastructure. This way, if one segment gets infected, it won’t affect the whole network.
- Conduct regular security audits: Perform security and vulnerability assessments to identify and address potential system and network weaknesses.
Adopting these preventive measures, practicing good cybersecurity hygiene, and staying vigilant can significantly reduce the risk of falling victim to a ransomware attack.