Unfortunately, millions of users worldwide are at risk every single day. Statistics show that a successful phishing attack occurs every 30 seconds, suggesting cybercriminals don’t stand still and evolve as their methods do. However, not only traditional phishing scams can damage a business – targeted phishing and CEO scams are much more devastating. Undoubtedly, IT decision makers fear becoming another story in the never-ending book of hacks. But what makes these phishing attacks so successful? According to an Osterman Research report, there are 6 things to blame.
1. Lack of user’s security awareness
The most critical vulnerability in any defense is the human factor. Unfortunately, it is the human factor that all phishing attacks are aimed at. In particular, it is the lack of employee training on issues such as phishing and ransomware. So about 6% of employees have never received security training. This is quite dangerous regarding employee confidence and the ability to recognize phishing attacks and act accordingly. In addition, employees should be trained to handle any unexpected emails and scams they may encounter on various platforms.
2. Cybercriminals change their focus
The availability of stolen data on the Darknet has dramatically reduced its commercial value. Fraudsters can buy payment card data so cheaply that it becomes unprofitable for those who steal and sell this information. In addition, banks have now introduced more sophisticated mechanisms to confirm transactions, and the ability to track them minimizes the effectiveness of previous schemes. In response, cybercriminals have changed tactics, seeking to make money through organizations directly through ransomware attacks. These attacks are not much more challenging for the cybercriminal, but the rewards can be much more significant. Although experts warn organizations not to pay ransoms, many victims prefer to transfer a lump sum to get their systems back online rather than face the headache of responding to incidents. Attacks such as ransomware are especially effective when information owners, fearing losing their data, will not think twice before paying the criminal’s demands.
3. Insufficient Business Impact Analysis
Some companies don’t do enough to mitigate the risks associated with phishing and malware. There is also no way to identify the weakest users who need further training. In addition, robust data backup processes are often lacking, as well as internal controls, such as double confirmation of any request for necessary actions, such as a bank transfer (which can prevent fraud by the CEO). Neglecting these processes plays into the hands of some of the most common fraud methods.
4. Good funding for criminal organizations
The enormous success that cybercriminals have achieved in recent years means that they have enough money to invest in this business. Thus, they can invest in technical resources to hone their skills. Unfortunately, this has also allowed cybercriminals to exploit new avenues of attack. For example, recently, there has been significant growth in social media. This is especially dangerous because most phishing tips refer to email scams or phone scams. Therefore, people do not always notice the methods that scammers use on social networks.
5. Relatively inexpensive tools that you can get at your disposal
You don’t have to have special skills to pull off a phishing attack. Unfortunately, the availability of phishing kits and the proliferation of ransomware as a service (RaaS) allows amateur hackers to enter the market and compete with sophisticated criminal organizations quickly. The most disturbing part of this growing trend is that even people with little or no IT experience are reaping the benefits of these easy-to-use tools. With such earning potential, it’s easy to see why criminals are drawn into such a lucrative business.
6. Malware is getting more sophisticated
The old (though still effective) technique of luring users to click on malicious links will soon be eclipsed by much more cunning and hard-to-catch tactics. Of course, attackers are in no hurry to abandon existing malware techniques right now. However, there are enough new threats that make it possible to trick even the users who know enough about cybersecurity. Session hijacking, cross-site scripting, clickjacking – not all of them are actually new, but still may evolve to the point where you cannot foresee the trick.
How to avoid phishing?
A phishing email is only the starting point for a cyber attack. Once inside, attackers deploy the next stage of the attack – ransomware or data theft. According to a data breach cost report, phishing-related data breaches cost companies an average of $4.65 million. Unfortunately, no single tool or solution can completely prevent all phishing attacks. As mentioned above, phishing is an intersection of human and technical issues, which is why it is so difficult to defend against.
A layered approach is recommended to minimize the chances of being tricked by phishing attacks, beginning with security funds to filter out malicious messages. Zero-trust security solutions prevent attackers from penetrating deeper into the system by constantly verifying users’ identities, thereby minimizing the number of people who can access sensitive information. Techniques such as multi-factor authentication help with this verification. A zero-trust strategy can save much money in the event of a breach. According to a report on the cost of data breaches, organizations with this strategy spend $1.76 million less than those that don’t use zero-trust. However, attackers are getting sophisticated; they are learning to bypass filters, so you must test them to confirm they are set up correctly.
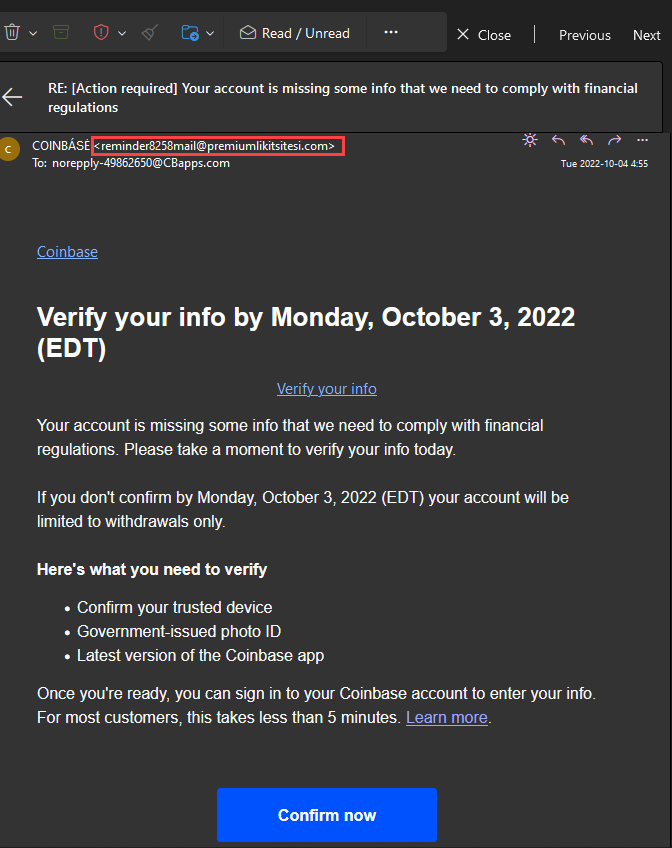
Finally, an employee training program with real-world examples is needed. The better employees understand how the attackers can act, the more likely they will identify threats and report them. For example, suppose an employee receives and identifies a phishing email. In that case, the company should take a screenshot and analyze any alerts employees should have noticed. Well-trained and vigilant employees can prevent many phishing schemes. It is also worth paying attention to links before clicking on them. Please hover your mouse pointer over the link and leave it unmoved for about a second so that the full link appears. If you’re expecting to go to facebook.com, make sure it looks like https://www.facebook.com and not something like http://faceb00k.com.
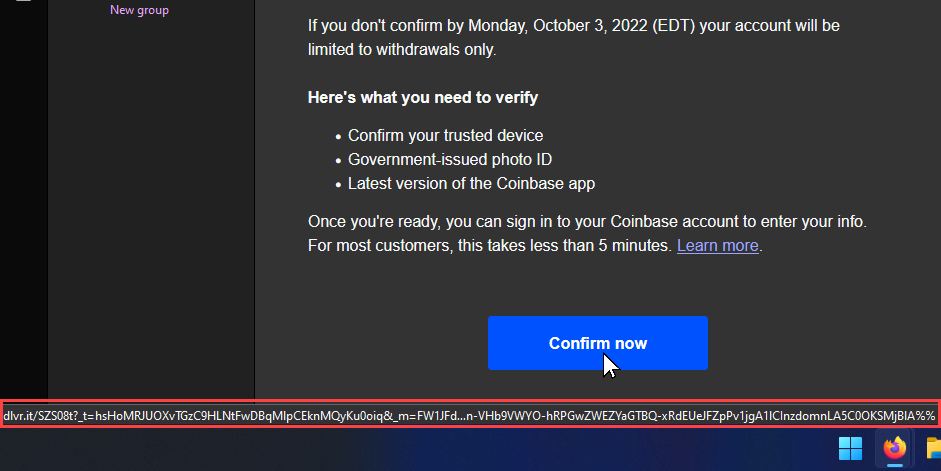
Another thing to watch out for are domains with minor errors, such as bankfoamerica.com. This can lead you to a site that seems completely real. Alternatively, you can open your browser and go directly to the site, log in, and then check your account or site for updates on the “problem”. So, the site would be easy to find if the original email or message was legitimate.
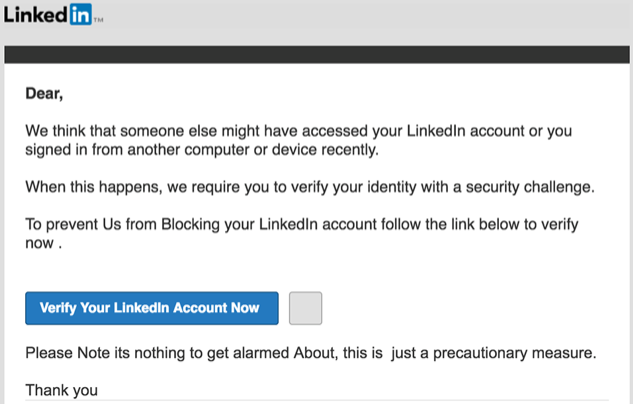
Don’t succumb to a sense of false urgency. Suppose an email or pop-up tries to scare you into logging in quickly. In that case, threatening consequences such as permanent lockout or disconnection, don’t be in a hurry. These tactics are designed to get you to bypass common sense and relay the information before you realize what’s wrong.




