Cybersecurity experts have uncovered a sophisticated cyberespionage campaign targeting a prominent U.S. aerospace organization. The threat actor, identified as AeroBlade, executed a spear phishing attack, raising serious questions about the overall cybersecurity preparedness within critical industries.
AeroBlade Attacks US Aerospace Company
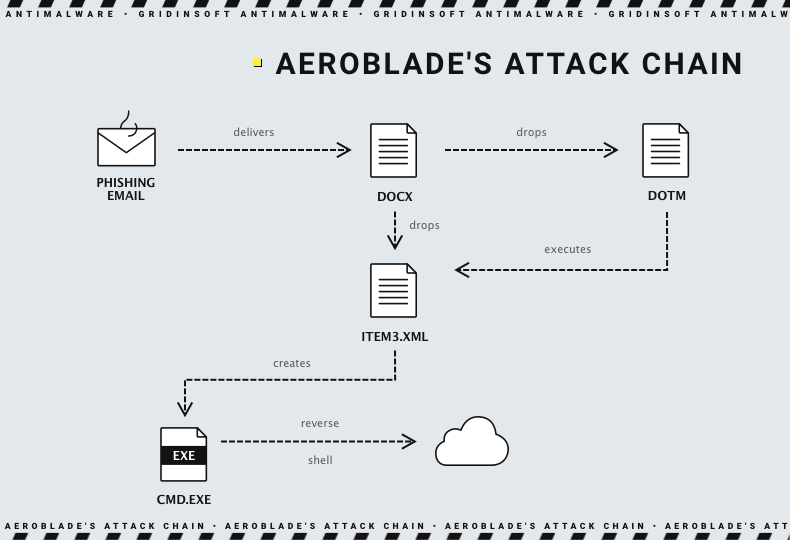
According to the cybersecurity experts, the spear phishing attack included sending the malicious file over email. The document, named [redacted].docx, employed a remote template injection technique and a malicious VBA macro code. The attacker’s network infrastructure became operational around September 2022, with the offensive phase occurring in July 2023, as assessed by BlackBerry with “medium to high confidence.”
The attack unfolded as follows:
- The malicious Word document is delivered through email spear phishing, enticing users to manually execute the file.
- The executed document employed a remote template injection to download a second-stage file, “
[redacted].dotm.” - The second-stage file executed “
item3.xml,” creating a reverse shell connecting to “redacted[.]redacted[.]com” over port 443.
The attack’s sophistication lies in the use of a remote template injection technique, a more advanced method than traditional phishing. By retrieving a payload from a remote server, attackers can circumvent some security measures that often catch more straightforward malicious attachments. The attack involved deploying a DLL as a reverse shell, granting control over the victim’s system.
AeroBlade Threat Actor – Is This Serious?
Callie Guenther, senior manager of cyber threat research at Critical Start, suggested the involvement of state-sponsored or highly organized criminal groups due to the level of commitment and resources demonstrated. As companies in the aerospace industry tend to be large in size and have well-built security systems, hacking them is never a trivial task. Such actions require commitment, professionalism and understanding the risks.
Analysts from BlackBerry suppose the commercial nature of AeroBlade group. In all detected episodes of its activity it aimed at the same company. The complexity of both attack approach and used tools grew significantly, especially in areas that aim at info exfiltration. Though, as other analysts suggest, nothing stops them from switching to more “classic” ransomware extortion in future.
Preventing phishing attacks
Phishing attacks prevention requires a multi-step approach that combines technological solutions, user education, and organizational policies. Here are essential steps:
- Regularly conduct phishing awareness training for employees to educate them about the various types of phishing attacks, warning signs, and safe online practices. Teach users how to recognize phishing emails, including checking sender email addresses. Also, scrutinizing email content for grammatical errors or suspicious links, and verifying unexpected attachments.
- Implement robust email filtering solutions to automatically detect and quarantine phishing emails before they reach users’ inboxes. Use email authentication protocols to verify the authenticity of incoming emails and reduce the likelihood of email spoofing. Also, consider implementing CDR systems – they will simply excise any content that is able to harm the system.
- Implement web filtering tools that block access to known malicious websites and URLs associated with phishing campaigns. Use URL scanning services to analyze and categorize website links, helping users avoid clicking on potentially harmful URLs.
- Keep all software, including operating systems, browsers, and security software, up to date with the latest patches. Cybercriminals often exploit vulnerabilities in outdated software to launch phishing attacks. Keep an eye on the latest cybersecurity news to be aware of new vulnerabilities.





