Back in mid-October 2023 Okta, one of the world’s largest identity providers, suffered a data breach. Security vulnerabilities in its support system allowed hackers to access one of the support accounts. Formerly, it was said about a miserable amount of customers suffering from the breach. But over a month later, the company discloses that hackers managed to leak the info about all the Okta Help Center clients.
Okta Hack Results Into a Massive Data Breach
As it was originally expected, the data breach within Okta Help Center touched only a miserable number of users. Due to the poor session token authentication, hackers managed to log in under the guise of a legit client and spawn several additional entities. This ended up with calling for a function designed to list all the Help Center accounts, which, as it was originally believed, had not been successful. As of October 20, Okta claimed about only 134 accounts having their data exposed in this incident.
As it turned out, this number was heavily underestimated. Further investigation showed that hackers successfully dumped info about all the accounts in the system. The co shares some specific details regarding the types of data exposed in that breach:
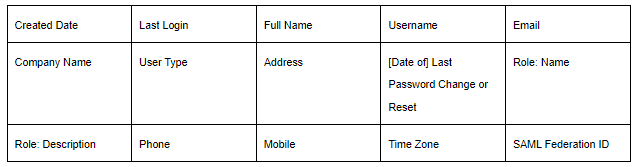
Therefore, it is possible that some of the users (0.4%, or 72 people) have more than just email and name exposed. Not a lot, but this already creates some critical contrast with the original claims from the company. And, what is more important, raises questions regarding the security architecture within the company.
More Details of Okta Hack Appeared
Aside from the data exposure disclosure, the company also shared some new details regarding the hack. As it turns out, crooks put their hands on a service account, designed to work with an automated algo running on a machine. This is often needed for automated backup creation and similar scheduled tasks. Credentials to this account were stored among other data on the employee’s Google account that hackers previously managed to access.
That explains the lack of the MFA protection on the compromised account (which is not an option for a machine) and its high privileges. Before, the story sounded rather ironic. The largest identity provider does not care about using identity protection mechanisms in their own networks. Now though it makes sense – as well as raises new questions about securing similar accounts. And it still does not justify the fact that compromising the account of a single employee in fact compromised the entire service.





