Eurecom has uncovered a series of exploits named “BLUFFS”, posing a significant threat to the security of Bluetooth sessions. These attacks exploit two previously unknown flaws in the Bluetooth standard, impacting versions 4.2 through 5.4 and potentially putting billions of devices, including smartphones and laptops, at risk.
BLUFFS Exploits – How Do They Work?
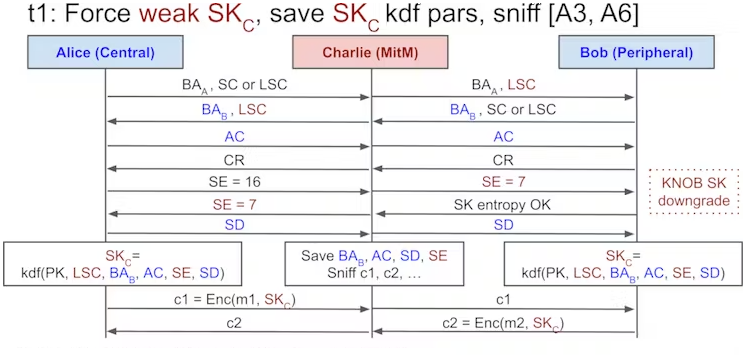
BLUFFS (Bluetooth Low User eavesdropping of Frequency-hopping Sessions) is a sophisticated series of attacks designed to compromise the forward and future secrecy of Bluetooth sessions, compromising the confidentiality of communications between devices. The methodology involves exploiting flaws in the session key derivation process, forcing the generation of a weak and predictable session key (SKC). The attacker then brute-forces the key, allowing them to decrypt past communications and manipulate future ones.
To execute BLUFFS, the attacker only needs to be within Bluetooth range of the targeted devices. Impersonating one device, the attacker negotiates a weak session key. Then, the other by proposing the lowest possible key entropy value and using a constant session key diversifier.
Impact on Bluetooth Devices
Given the architectural nature of the flaws, BLUFFS impacts all the devices running a whole lineup of Bluetooth protocol versions. The vulnerabilities affect Bluetooth Core Specification 4.2 through 5.4, potentially exposing a vast number of devices to the exploits. The impact has been confirmed through tests on smartphones, earphones, and laptops running Bluetooth versions 4.1 through 5.2.
Bluetooth SIG, the organization overseeing Bluetooth standard development, has received Eurecom’s report. They recommend implementations to reject connections with low key strengths, utilize “Security Mode 4 Level 4” for higher encryption strength, and operate in “Secure Connections Only” mode during pairing.
Mitigation Measures
Researchers propose backward-compatible modifications to enhance session key derivation and mitigate BLUFFS and similar threats. Recommendations, however, offer only the protocol fixes, i.e. they are not about to be done by users. Sadly, but at the moment, there is not much you can do to secure the BT connection.





