Aqua Security security researchers have warned that the TeamTNT group may be preparing a new large-scale anti-cloud campaign called “Silent Bob”.
Such suspicions arose after experts discovered hackers targeting misconfigured servers.
Aqua Security launched an investigation after discovering an attack on one of its lures. Subsequently, 4 images of malicious containers were discovered. However, given that some features of the code have remained unused, it appears that the campaign has not yet fully launched at this time.
TeamTNT is a cybercriminal group known for destructive attacks on cloud systems, especially Docker and Kubernetes environments. The group specializes in cryptomining.
We wrote that, for example, only within one month, two years ago, the group’s botnet infected more than 50,000 systems. However, in those good old days, mining botnets even attacked PostgreSQL databases. And also, if you remember, there was such a pretentious malware as KingMiner, which attacked MSSQL.
Although TeamTNT ceased operations at the end of 2021, Aqua Security linked the new campaign to TeamTNT based on the use of Tsunami malware, the dAPIpwn function, and a C2 server that responds in German.
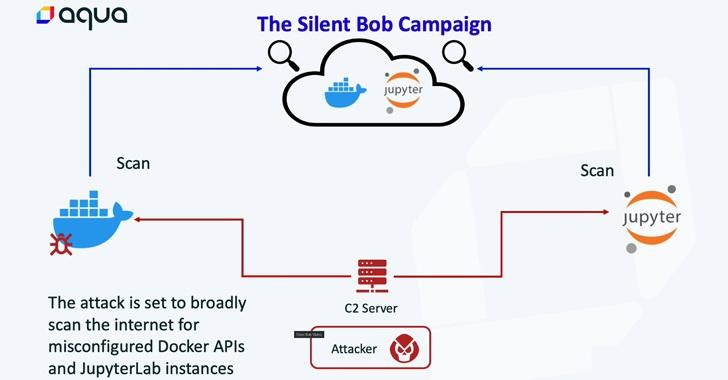
Detected group activity begins when an attacker identifies a misconfigured Docker API or JupyterLab server and deploys a container or interacts with the Command Line Interface (CLI) to scan for additional victims.
Such a process is designed to spread malware to more servers. The secondary payload includes a cryptominer and a backdoor, with the backdoor using the Tsunami malware as an attack tool.

Aqua Security also published a list of recommendations to help organizations mitigate the threat.




