TikTok Invisible Challenge became yet another host for threat actors. Crooks found a way to spread the WASP information stealer as a specific utility to revert the in-app filter. Users who ate the bait are risking their account credentials and banking information.
What is the TikTok Invisible Challenge?
Same as Instagram back in the previous decade, TikTok gives birth to numerous challenges. Invisible Challenge is just another example that touched tens of countries across the globe. It offers people to record a video using a new filter that removes the human body from the record, leaving only a transparent silhouette and clothes that were on the person. Such AI-based filters are not a new thing, but this challenge seemingly aims at propagating their usage. Not a bad practice on paper, but that created an unexpected problem.
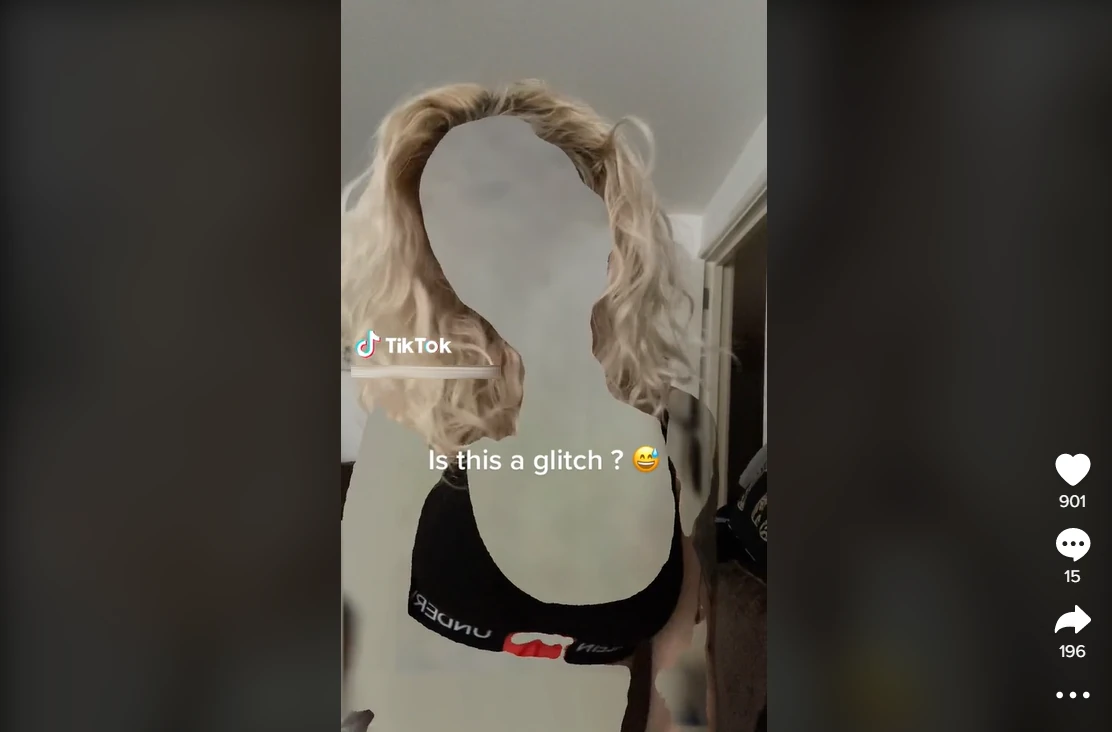
Some users, particularly females, decided to undress on camera having this filter enabled. As the filter remains active, that’s no risk of revealing your naked body. But a certain number of viewers started thinking of reverting the filter effect to see the original – with no clothes and no filter. Despite the fact that it is not real unless you have access to the device that recorded this video, some cunning fellas offered a way to “unfilter” the video. And here is where the problems have started.
TikTok Invisible Challenge spreads malware
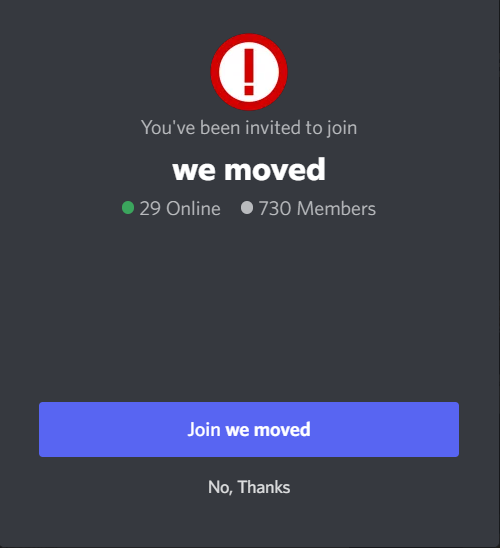
Most of the time, the handymen who offer to unfilter the video will share the link to a Discord server. This place is full of videos that look like the outcome of the filter removal utility. Hence, the unsuspecting user will likely believe that the ability to remove the filter is real. As I have mentioned before, it is possible only when you have access to the source video, which is present only on the author’s device. TikTok servers contain only the edited version of this video, where it is impossible to tear off the filter.
Therefore, we already figured out that the “Unfilter” utility is not real. If so, what goes under the guise of this tool? Numerous victims that followed the instructions from discord[.]gg/unfilter got WASP stealer on their device. This malware aims at credentials, cryptowallets information, banking data, and the like. The exact application was posted on GitHub, which for some reason is considered a reliable source with no chance to get malware. A bot in Discord additionally asked the channel participants to give a star (i.e. upvote) to the repository of a pseudo-utility. By the number of those stars – over 100 – we can estimate the number of victims. The exact Discord channel had over 700 followers and now is defunct.
Is WASP stealer dangerous?
Safe malware does not exist; it is an oxymoron. Stealers are not an exclusion, as they aim to steal a lot of users’ credentials, including financial ones. Most often, crooks pack the data they got into large databases and sell them on the Darknet. At that point, anyone can purchase it, and use it for their purposes. And as you can guess, Darknet is not a place that is famous for benevolent users. You can surely say goodbye to your savings in both crypto and bank accounts, as well as your accounts on social networks. That will not happen instantly, but this event is unavoidable if countermeasures are not taken.
If you suspect the infection with stealer malware, do the following steps:
- 1. Scan your computer with anti-malware software. It should be your first-and-foremost step since active malware can make all of the following actions useless. Stealers are not very easy to detect, hence you need an advanced solution that has both complex scanning systems and often updates. GridinSoft Anti-Malware fits both of these criteria.
- 2. Change all the passwords. Malware grabbed your current credentials, so it is quite obvious that changing your login information is vital to make its job useless. The sooner you do it, the fewer time hackers have to use your accounts and money.
- 3. Notify your friends and family about the threat. TikTok is a very popular social network, thus not only you but someone you know may also be at risk. The more people will be aware that Invisible Challenge filter reversion is not real – the fewer profit hackers will have.
However, stealers, as well as any other malware, is better to prevent before they will make their way to your device. Avoid any questionable things, especially when they contradict the very basis of how things work. Be also very skeptical about any software from unknown publishers you find online. Preventing the threat is always way easier, than dealing with its consequences.