The threat landscape meets a new player – Rugmi Loader. This threat specializes in spreading spyware, and is in fact capable of delivering any malware type. Rugmi boasts of its unusual structure, which makes it rather promising among other loaders.
What is Rugmi Loader?
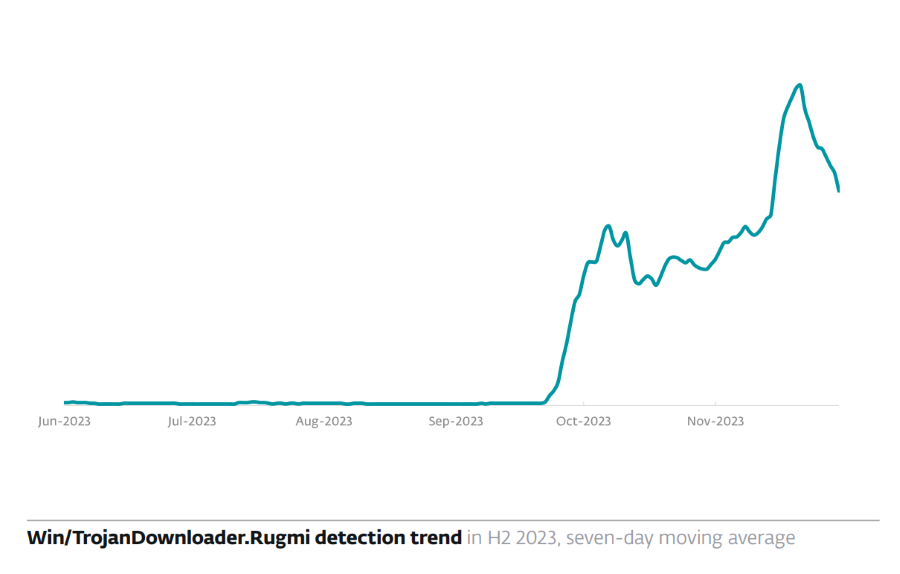
The Rugmi is a complex loader with multiple components that deliver information stealers. According to the report, in October and November 2023 alone, Rugmi detections have multiplied. Initially observed with only a few detections, Rugmi has experienced a dramatic increase in activity, with daily detections now numbering in the hundreds. This trend was particularly noticeable in the latter months of 2023.
The design of the Rugmi Loader features three components that allow it to unleash its malicious payload. The first component is a downloader tasked with retrieving an encrypted payload. It fetches the necessary malicious software while evading detection through encryption.
The second component is a loader ащк the payload from internal resources. It means that malware can arrive with an embedded payload and run it after all of the initial checks. This internal execution allows the malware to operate seamlessly, integrating into the system’s processes without raising immediate alarms.
Finally, the third component is a loader for external files. It activates the payload from an external file, the one downloaded through the command from the C2. Such a delivery method is more classic, and allows for more steady operations. At the same time, it may be unsuitable for attacks that require rapid action. Conjoining two methods in one is quite a new thing, which will certainly play its party in this malware’s performance.
The primary targets of these campaigns have been identified as the U.S. and Canada, indicating a strategic focus on regions with high-value targets. Such localization coincides with the activity of major spyware families, particularly Vidar, Raccoon and Lumma.
Loader Malware Explained
As the name suggests, loader (or dropper) malware is malicious software designed primarily to download and install other malware onto a compromised system. In short, it acts as a gateway for more malware. Loaders allow gaining access to a system and then fetching other harmful payloads from a remote server. This makes the overall deployment easier, allows weeding out honeypots, and makes the analysis of the entire attack chain more complicated.
The final payloads of loaders could be anything from ransomware and banking trojans to spyware. Its primary purpose is not to cause direct harm but to pave the way for “normal” malware. This road paving also includes changing system properties so there will be much less obstacles for further malware injection.
How dangerous is Rugmi Loader?
There are quite a few loaders in the modern threat landscape, but Rugmi has the merits that can make it competitive, if not prevalent. Currently, this market is dominated by Amadey, which is built around a more straightforward approach. Modularity of Rugmi makes it more potent in all the attack scenarios. At the same time, the rapid growth of a newcomer may motivate old players to evolve, which will spice up the malware world even more.
Nonetheless, all the benefits it brings are more about quantity rather than quality of malware that Rugmi can deploy. Ransomware, spyware, stealers – they develop in their own pace and path, and changes to the delivery methods barely change that. And since the new loader is not something groundbreaking, it is unnecessary to expect huge shifts in the paradigm.
Protect Yourself Against Malware
To safeguard against malware, including sophisticated threats like the Rugmi Loader, follow these essential practices:
- Be cautious with emails and downloads. We recommend avoiding clicking links or downloading attachments from unknown or suspicious sources. Doing so may put your device and personal information at risk. Phishing emails are a common way to spread malware.
- Use reputable antivirus software. The anti-malware solution is the first defense line against malware. Please ensure you have a reliable antivirus program installed and keep it updated. These programs can detect and remove many types of malware.
- Beware of social engineering. With the rise of services like ChatGPT, even the most obtuse scammer can write a convincing, well-crafted email. Be skeptical of unsolicited offers or alarming messages demanding immediate action.
- Educate yourself. Today, internet scams are progressing too fast. Keeping abreast of current events means knowing how to confront it all. Beware about the latest malware threats and learn to recognize potential risks to ensure your online safety. Forewarned is forearmed.





It’s great to have such high-quality analysis, information and documentation. We need it so much, and I really appreciate it. We’re also very much alone in considering these kinds of risks and threats when we work in cybersecurity, and very few people understand the background work, as well as the effort, time, training and energy needed to keep up to date. People don’t perceive the 100,000 threats we’re facing (and I’m being kind) and quickly categorize you as paranoid, whereas these are factual facts that require a great deal of analytical finesse, understanding, vigilance, and also experience, because many things are of a subtlety that’s hard to understand. It would be good to be able to forge partnerships or work seriously in this direction between professionals.