News, Tips, Security Lab
Shuckworm Gang Attacks Ukrainian Companies Using Pterodo Backdoor and USB Drives
Symantec experts report that the Shuckworm hack group (aka Armageddon, Gamaredon, Iron Tilden, Primitive Bear, Trident Ursa, UNC530, Winterflounder, and…
Cloud Mining Scams Spread Banking Trojans
It’s no secret that cybercriminals are increasingly using mobile platforms as an attack vector lately. One example is a new…
WannaCry 3.0 Ransomware Aims At Enlisted Russian-speaking Players
A previously unknown payload of ransomware, that call itself WannaCry 3.0, targets Russian-speaking players of the Enlisted game. Hackers reportedly…
Malware in GitHub Repositories Is Spread From Fake Security Company Name
Researchers detected fake company accounts on GitHub linked to a deceitful cybersecurity company. These accounts are promoting harmful repositories on…
BreachForums Is Back Online, Led by ShinyHunters
BreachForums, an infamous Darknet forum that was shut down in late March 2023, is back online since approx. June 13…
A WSO2 Vulnerability is Fraught with Remote Code Execution
The products by WSO2, an open-source API, applications, and web services provider, have been attacked in the wild through the CVE-2022-29464 vulnerability detected back in April 2022. This vulnerability allows…
Microsoft Experts Found Vulnerabilities in Pre-Installed Android Applications
Microsoft experts have found four serious vulnerabilities in pre-installed Android applications, namely in the framework used by Android applications of several major international mobile service providers. Vulnerabilities were discovered in…
DNS Spoofing: Key Facts, Meaning
What is DNS Spoofing? DNS (Domain name server) spoofing or DNS cache poisoning is a type of cyberattack used by an attacker to direct the victim’s traffic to a malicious…
Some Tips About Data Loss Prevention (DLP) For Users
Data Loss Prevention (DLP) is a method of detecting data loss and preventing a given case, including awareness of the protected content or context. It also includes using tools that…
Google Has Disabled Some of the Global Cache Servers in Russia
Media reports say that Google is notifying ISPs in Russia that it is shutting down its Google Global Cache (GGC) servers, which speed up the loading of its services, including…
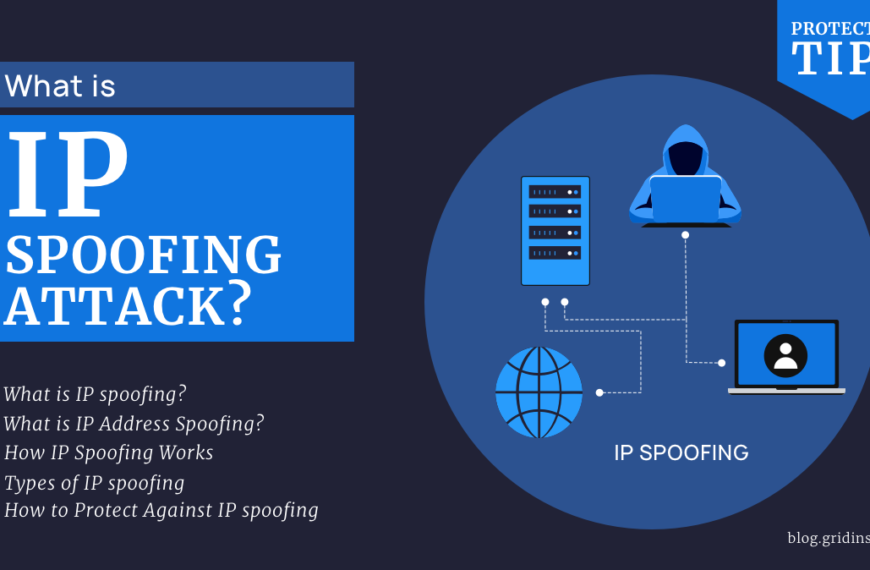
IP Spoofing Attack: Explanation & Protection
Among other types of attack, IP spoofing stands out for its simple yet graceful design. This is, exactly, what goes for its long life and widespread application throughout decades. Let’s…
10 Ways To Recognize and Avoid Phishing Scams
Phishing attacks are a scam that aims to steal confidential data through a set of methods. It has appeared since the time of the Internet. Fraudsters, in all forms, try…
15 Reasons to Choose GridinSoft Anti-Malware
Choosing the anti-malware solution these days is a tough decision. Over a dozen vendors offer a wide range of services, additional features, and promise extremely high efficiency of their tools.…
Fake Exploits Used to Deliver Cobalt Strike Beacons
Cyble experts have warned that cybercriminals are attacking IS researchers, distributing malware under the guise of exploits for Windows, which eventually installs Cobalt Strike beacons on the experts’ machines. Let…
Working Tips and Recommendation: How to Use OSINT
OSINT, or open-source intelligence, is a kind of reconnaissance operation that became extremely popular in the last few years. The known events in the Eastern Europe gave the other punch…
Benefits Of Using Malware Protection
It seems that people are not aware of the benefits of using malware protection. Many people have heard about computer threats but possess a rather vague understanding of what they…
Top Threats That Anti-Malware Catches
As technology advances, cyber-attacks become more prevalent, with attackers constantly developing new methods to exploit vulnerabilities in PCs and other devices. One of the most common reasons behind these attacks…