LockBit, an infamous ransomware gang that became a major threat actor over the last two years, released the variant of its ransomware for macOS. Previously, this system was considered safe from ransomware, as no known samples were targeting it specifically. Currently, LockBit’s product is considered the first ransomware that breaks that rule.
What is the LockBit gang?
LockBit group is a currently leading gang of threat actors that have spread eponymous ransomware since 2019. Through their entire lifetime, they are constantly updating their malware, making it more resistant to any countermeasures. The group is also significant for their media personality – they are never shy of giving interviews and discussing something on forums. After the Conti group dissolution in 2022, LockBit became a leader on the market, scoring a share of over 40% of all attacks at some point. This number fluctuates, but the nomination of the most successful cybercrime gang remains.
The key thing that gives LockBit its success is its ransomware and auxiliary software used in cyberattacks. In complex, these programs provide a safe, fast and reliable way to encrypt and exfiltrate the files. At the very beginning, their ransomware and data exfiltration software already were the fastest. But with time and updates, hackers made it even more rapid. In fact, no massively-used ransomware examples are even nearly compatible, and only one known sample – Rorschach ransomware – can boast of faster encryption. Updates bring not only faster encryption & exfiltration, but also updates to network infrastructure and bug bounty programs.
LockBit’s First-in-Kind macOS Ransomware
For a long time, macOS was considered a space safe from malware. Surely, there were minor things like adware or browser hijackers, that resided in browsers – but they do not rely on the operating system. “Serious” malware, like spyware, backdoors and ransomware were non-existent. Theoretically, some malware samples aimed at *NIX systems could run on macOS (as it is compatible), but they were not specifically designed to attack it. But on April 16, 2023, the news stating about macOS-targeted variant of LockBit appeared.
"locker_Apple_M1_64": 3e4bbd21756ae30c24ff7d6942656be024139f8180b7bddd4e5c62a9dfbd8c79
As much as I can tell, this is the first Apple's Mac devices targeting build of LockBit ransomware sample seen…
Also is this a first for the "big name" gangs?
🤔@patrickwardle
cc @cyb3rops pic.twitter.com/SMuN3Rmodl
— MalwareHunterTeam (@malwrhunterteam) April 15, 2023
The fact that the previously invincible system descended from the pantheon and is now along with the mortals initiated a hurricane of discussions. On weekends when it happened people went mad in their expectancies, creating more and more versions of what it is capable of and how that works. LockBit themselves, however, only confirmed having a newly developed macOS variant of their ransomware.
What actually happens?
Behind the huge media backlash, a lot of interesting details slipped away. They generally get available during the analysis of the sample. The latter appears to be completely undetected by vendors listed on VirusTotal, and aims at ARM systems. In just a day they’ve corrected this fault – at least some of them, though. However, further analysis of the sample shows that LockBit managed to compile it for multiple other platforms – like PowerPC, ARMv5/v6/v7, Linux, FreeBSD and even SPARC. Actually, the entire lineup of Apple products is at risk now – from computers to tablets and cell phones. Even the legacy, PowerPC-based systems, are not safe.
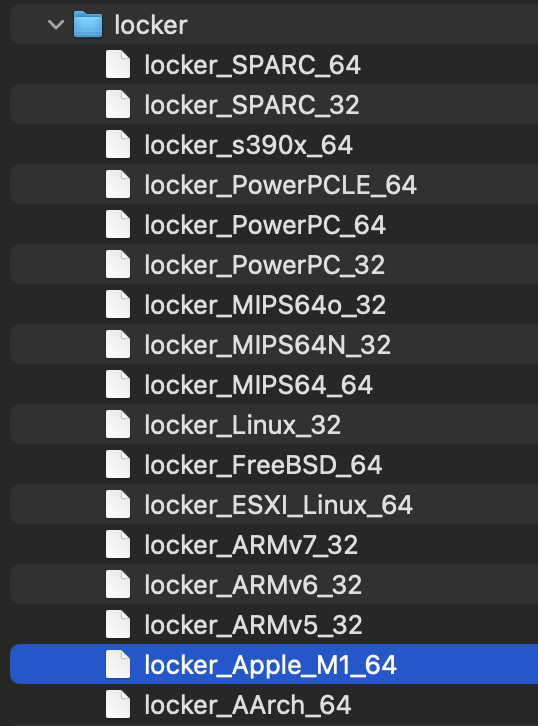
The exact sample refuses to be run in a normal way, as it lacks a valid signature of Apple Developer ID. To make it run, hackers most probably use a specific console command, that allows them to circumnavigate the restrictions. Sample is XOR-encrypted and features a couple of anti-analysis tricks. In particular, it forces the debug environment to stop if malware detects one. Still, after a deep analysis analysts noticed a lot of flaws present in this LockBit version. Malware is prone to buffer overflow errors, and most of its anti-analysis measures may easily be blocked.
Is LockBit ransomware for macOS dangerous?
For sure, it is. Despite being less than ideal at its current iteration, it will become so in future – I have no doubts about that. LockBit gang never overestimates their malware capabilities and will do their best to fix all the things analysts have found by now. Moreover, other gangs may have this case as an example and release their own ports. It is a pretty small threat for macOS at the moment, but may end up in a completely new paradigm.
Having macOS-based malware is threatening not only because of the novelty of such threats, but also because of absence of any countermeasures. Actually, they’re not totally absent – there are several anti-malware software solutions for macOS. Yet they have low coverage that makes no obstacle for malware. Additionally, these solutions have low capability against advanced threats, like LockBit ransomware, making protection even less effective. The only advice now is to implement proactive measures of counteraction – ones that will not allow malware to get to the system at all.
How to protect yourself?
Fortunately, counteractions against LockBit ransomware are cross-platform. LockBit hackers commonly utilise network vulnerabilities to make their way to the network and infect it. You can practise with firewalls or other restrictive measures, but crooks found the way to circumvent them. Advanced solutions, like Network Detection and Response, will fit best for that case. They do not always require having the client part installed on each system, bearing on overall network traffic monitoring. Detection systems and extensive logging make it much easier to stop the threat and prepare for possible intrusions in future.