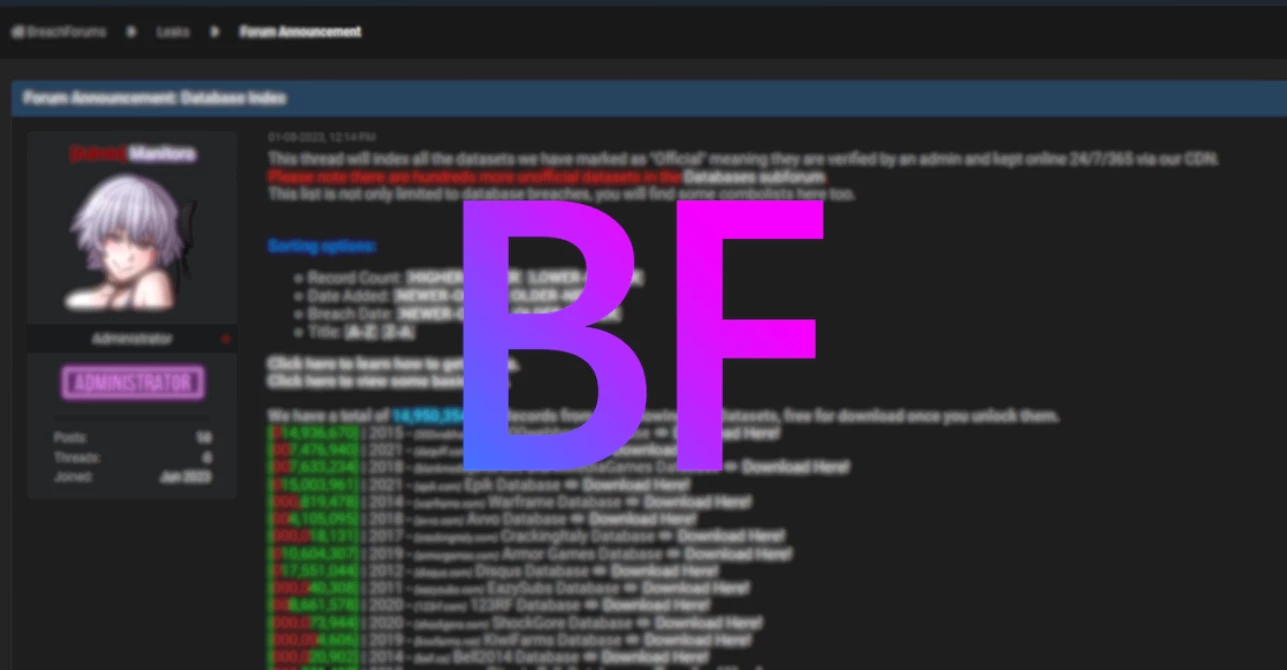
BreachForums Is Back Online, Led by ShinyHunters
BreachForums, an infamous Darknet forum that was shut down in late March…
RDP Honeypot Was Attacked 3.5 Million Times
With increased remote work, IT teams use remote access tools to manage…
Oneetx.exe
Oneetx.exe is a malicious process, related to Amadey dropper malware. It can…
Fortinet Fixes RCE Flaws in FortiOS and FortiProxy
Fortinet, a well-known vendor of corporate-grade security solutions, issued an urgent patch…
Third Party Data Breach: Definition and How to Prevent It
In today's digital landscape, data breaches have become an alarming reality for…
Android Malware Mimics VPN, Netflix and Over 60k of Other Apps
Android is an open operating system. This is an advantage and a…
Beware of Vacation-Related Scams: 4 Most Prevalent Types
Email scam actors constantly try to pick a better disguise for their…
BlackCat Ransomware New Update Boosts Exfiltration Speed
BlackCat ransomware continues to make a fuss globally for the second year…
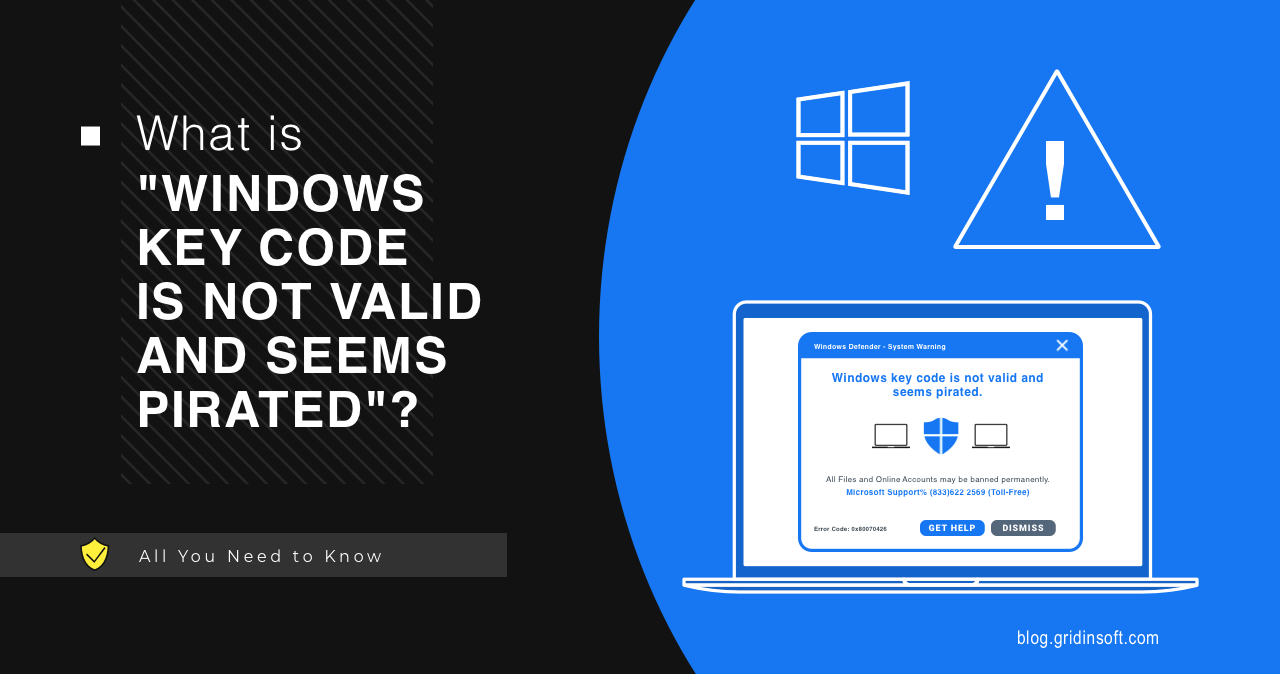
What is “Windows Key Code Is Not Valid And Seems Pirated”?
Windows Key Code Is Not Valid And Seems Pirated appears to be…
How to Defeat Insider Threat?
In the current digital world, organizations face more risks than ever due…
ChatGPT has become a New tool for Cybercriminals in Social Engineering
Artificial intelligence has become an advanced tool in today's digital world. It…
Conti Ransomware Heritage in 2023 – What is Left?
Ransomware groups come and go, but the people behind them continue to…