MOVEit MFT 0-day Vulnerability is Used to Steal Corporate Data
MOVEit managed file transfer (MFT) solution appears to contain a 0-day vulnerability,…
New iOS Vulnerability Allows “Triangulation” Attack
New iOS vulnerability allows executing a zero-click malware delivery through the built-in…
DDoS-for-Hire: Booter, Stresser and DDoSer
Most people think you must be a hacker to participate in cyberattacks.…
Android Malware With Almost 500M Downloads Resides in Google Play
Millions of Android users may be at risk of a cyberattack because…
RarBG Torrenting Site Is Shut Down, Admins Explain Why
RarBG, one of the most famous torrent tracker websites in the world,…
Ransomware Attacks in 2023: What to Expect?
Cybersecurity experts have published a report on worrying ransomware statistics. A survey…
RaidForums Leaked, Data of Almost 500,000 Users Published
RaidForums, the former leader among the underground forums, now suffers the user…
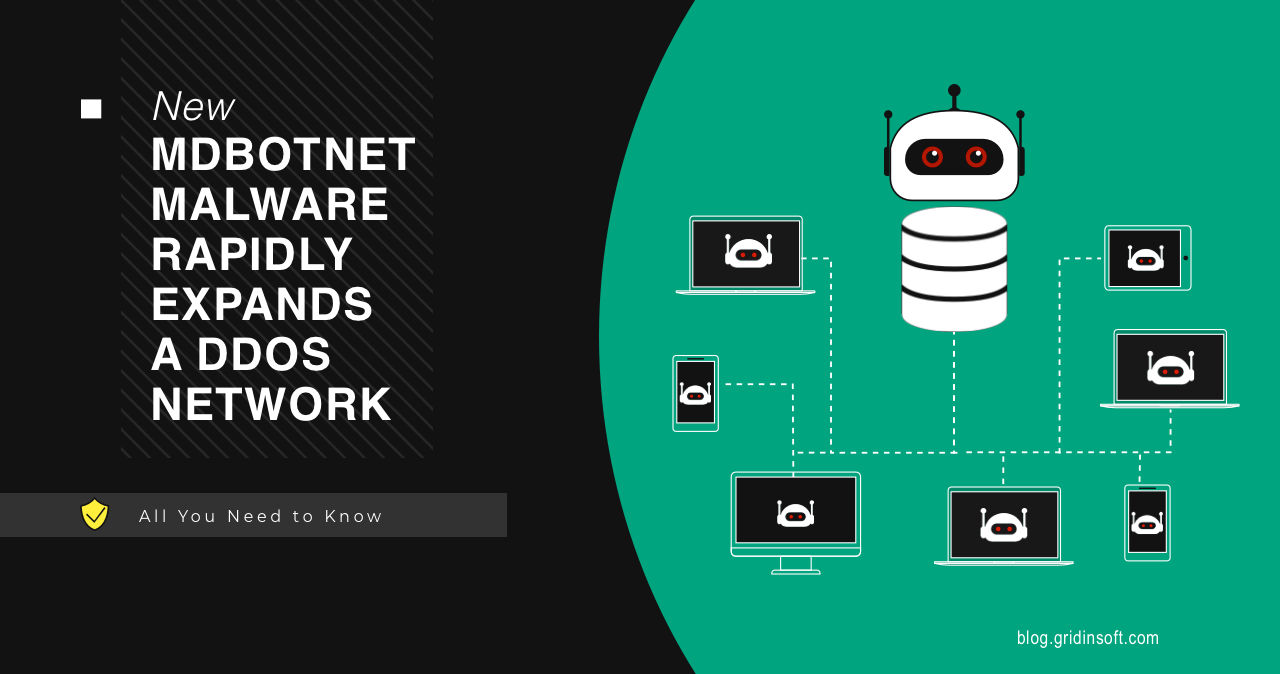
New MDBotnet Malware Rapidly Expands a DDoS Network
MDBotnet is a new malware strain that appears to be a backbone…
Ransomware Attacks Decline in 2023 – Is It True?
According to ransomware attacks status statistics, the trend of incidents related to…
US Authorities Warn of Disaster-Related Scams
Following natural disasters and severe weather, there is a higher chance of…
GitLab Releases Patch to Critical Vulnerability
GitLab, one of the most famous code repositories in the world, faces…
GoDaddy Refund Phishing Emails Spread Infostealer
Hackers started using GoDaddy Refund Emails as a disguise to trick the…