New iOS vulnerability allows executing a zero-click malware delivery through the built-in iMessage messenger. The breach was discovered by Kaspersky analytics team, and appears to touch almost every user of Apple smartphones. Experts dubbed the malware “Triangulation”.
iOS Exploit Allows Zero-Click Infection
Probably, the worst case scenario for any target of cyberattack is the infection performed without any action from the victim. And this is it – a crafted iMessage can trigger the malware injection to the device, leaving the user no chance to react. According to the report issued by Kaspersky, the breach is used to install a spyware dubbed Triangulation. Thing is, analysts discovered this trojan running in the iPhones of the company’s top executives.
Triangulation spyware is capable of things typical for malware of its class that aims at mobile devices. It allows for remote microphone enabling, gathering information about activity hours, geolocation, and grabbing photos and files from messengers. The worst thing here is that Triangulation is particularly hard to stop or remove – to some extent because of specific iOS characteristics.
Triangulation Trojan Is Very Tough to Find and Remove
As any other spyware, this one tries to stay as stealthy as possible. The only visible sign of its activity is disabled updates – at least this is what analysts discovered while examining the case. In iOS 14, Apple introduced a feature that displays when your mic or camera is in use, and also shows which app uses it. Though, it does not look like Triangulation triggers that mechanism, either because of a certain trick with OS settings or through enabling the mic during the use of other apps.
Since iOS keeps its files closed from external view, it is hard to use specialised software to uncover the malware running in the system. Moreover, this makes its removal even more difficult. The mentioned report says that the only probable way to remove Triangulation trojan from the device is to reset the phone to factory settings. And it is suboptimal – such a harsh operation wipes all user files as well. And each minute spent with an infected device can mean more and more personal data leaked to the unwanted party.
What can I do?
Frankly, it is quite unusual to give such advice to iOS users. For a long time, this operating system was considered one, if not the most secure OS. Zero-day vulnerabilities or clickless exploits were happening earlier, but Apple issued hotfixes pretty quickly. Though this time, neither the list of vulnerable iOS versions nor hotfixes are available. I hope to see a new-style Rapid Security Response patch Apple introduced in the past month. But now, here is what you can do to protect from Triangulation trojan attack.
Perform a periodic checkup of your device. Potentially, the victims in Kaspersky team were simply ignorant to the mic/camera usage notifications that were appearing on the screen. Either way, keeping eye on what your iPhone tries to tell you is important – sometimes simply to uncover a legit app that uses your mic excessively.
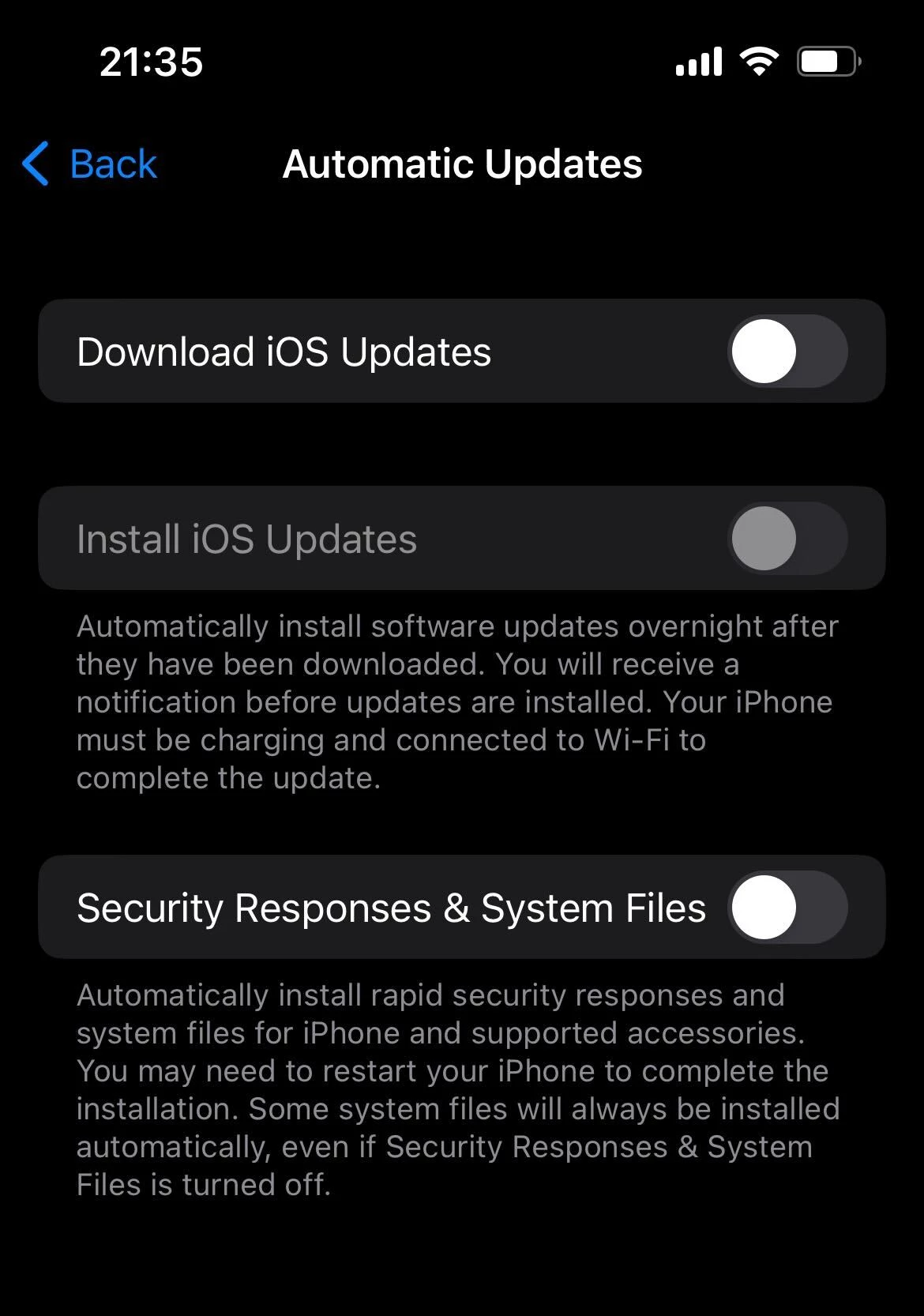
Another place you can peek into is the Updates section in Settings. Since the malware reportedly disables updating functions, it may be an obvious sign for the user. Even if you disabled it willingly, it is recommended to turn them back on. Apple is doing its best to keep their devices secure, and the new updates policy is a perfect confirmation to that.
To continue the previous paragraph – keep an eye on the most recent iOS updates and install all security patches available. Sometimes, the company releases fixes even for older OS versions, especially if the vulnerability is critical and exploited in the wild. As you can see, sometimes being careful and avoiding muddy waters may be not enough, because you simply cannot avoid a thing you cannot even see.

