MOVEit managed file transfer (MFT) solution appears to contain a 0-day vulnerability, already exploited by hackers. Progress, the developer of the software solution, already released a note and security advisory regarding the case.
What is MOVEit MFT?
MOVEit is a software solution that allows convenient and secure data transfer inside the organisation. The product under this brand name has a long story that begins in 2002, and on its path got the cloud storage feature and support of mobile platforms. Solutions of such kind gained significant popularity since the companies started bearing on electronic document management. Retaining diligent security level for that process is tremendously important, as such apps are used to transfer any kind of corporate documents.
MOVEit MFT 0-day Allows to Steal Data
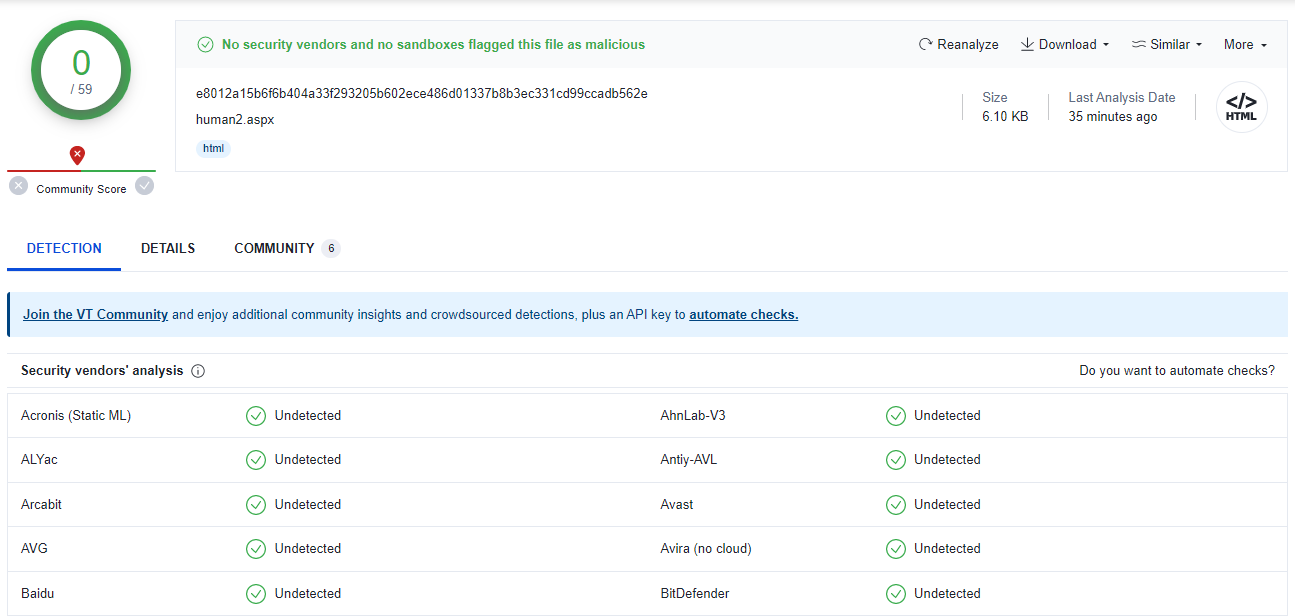
According to the advisory published by the Progress, the vulnerability in MOVEit MFT allows for unauthorised access that ends up with remote code execution. The vulnerability also relies on two HTTP ports – 80 and 443. Known cases of this vulnerability usage were bearing on an SQL injection that grants hackers access to the MOVEit MySQL server. Researchers detected a sample of the webshell code uploaded to VirusTotal – it is completely undetected. The consequent requests to the database tries to pick the password, and once the input is correct, the door is open. After the successful penetration, hackers get access to the list of the files, and possess the ability to add new and download what is already present.
The list of the vulnerable and secure MOVEit versions is as follows:
| Software name | Vulnerable versions | Fixed in |
|---|---|---|
| MOVEit Transfer | 2023.0.0 | 2023.0.1 |
| 2022.1.x | 2022.1.5 | |
| 2022.0.x | 2022.0.4 | |
| 2021.1.x | 2021.1.4 | |
| 2021.0.x | 2021.0.6 |
Security Advisory for Vulnerable Versions
Aside from the update request, developers released a list of recommended actions. The only solution is banning the connections via the aforementioned 80 and 443 ports in the firewall rules. Though, it is not lossless – without the access through these ports, users will not be able to log into the web interface; built-in automation tasks as well as some of the APIs and add-ons will not work either. After this manipulation, Progress still recommends checking the logs for potential attempts of malignant access and updating the software.





