Computer viruses really resemble real ones. They can infect thousands of computers in a matter of minutes, which is why we call their outbreak an epidemic. It’s hard to imagine how we could live without antivirus software now, but once it was a reality. But which virus was the most dangerous? I’ve compiled a list… Continue reading TOP 10 Most Dangerous Computer Viruses In History
Author: Stephanie Adlam
I write about how to make your Internet browsing comfortable and safe. The modern digital world is worth being a part of, and I want to show you how to do it properly.
Aluc Service: What Is Aluc App & How to Remove?
Aluc Service is a strange service you can spectate in the Task Manager. It is, in fact, a malware-related process that hides behind a legitimately-looking name. Most commonly, such a trick is done by coin miner malware and rootkits. What is Aluc Service? At a glance, Aluc Service may look like a legit service among… Continue reading Aluc Service: What Is Aluc App & How to Remove?
Exim Vulnerability Allows RCE, No Patches Available
Exim Internet Mailer, a program massively used as a basis for mailing servers, appears to have a remote code execution vulnerability. By overflowing the buffer, hackers can make the program execute whatever code they need. Despite several reports to the developer, the patch is still not available. What is Exim? Exim is a mail transfer… Continue reading Exim Vulnerability Allows RCE, No Patches Available
Redline and Vidar Stealers Switch to Ransomware Delivery
Cybercriminals who stand behind RedLine and Vidar stealers decided to diversify their activity. Now, crooks deploy ransomware, using the same spreading techniques as they used to deliver their spyware. Meanwhile, the process of ransomware enrollment is rather unusual and is full of advanced evasion techniques. What are Redline and Vidar Stealers? RedLine is an infostealer… Continue reading Redline and Vidar Stealers Switch to Ransomware Delivery
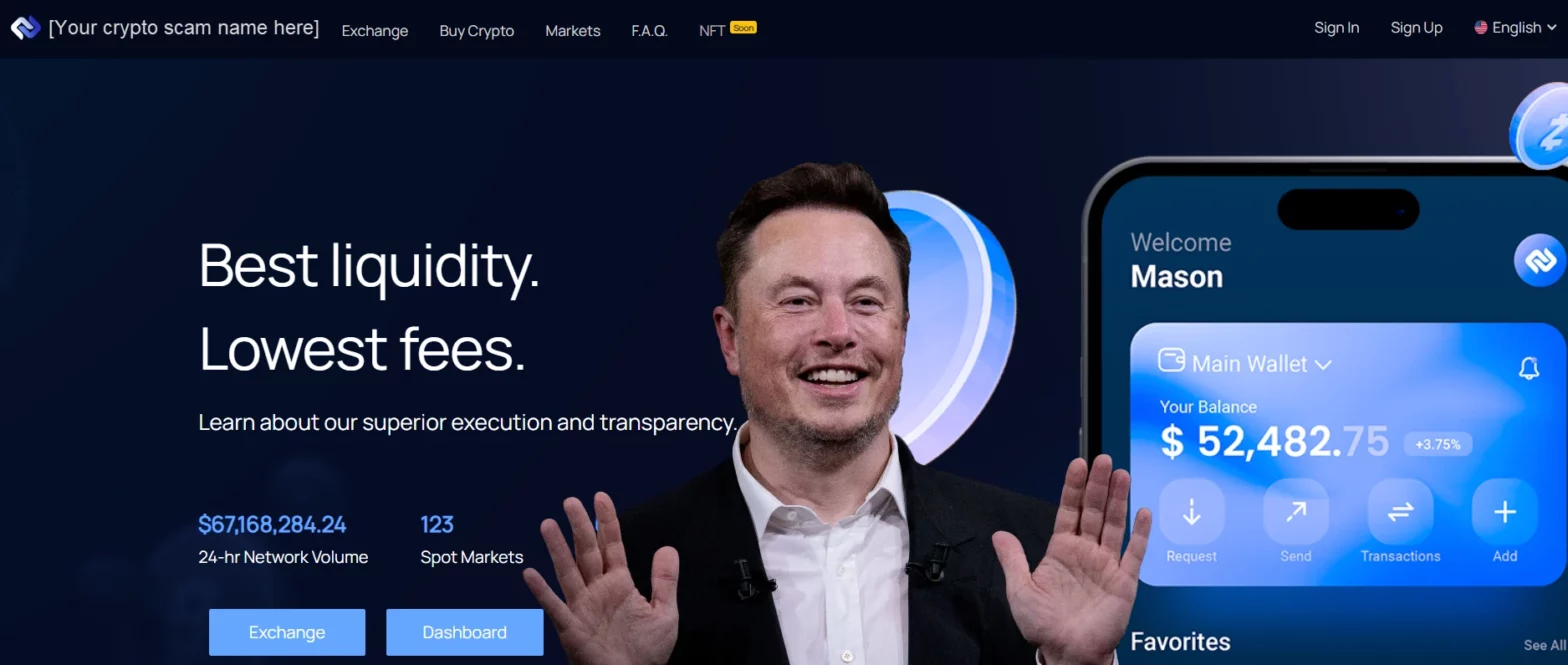
TikTok Flooded By Elon Musk Cryptocurrency Giveaway Scams
Recently, TikTok has been inundated with a flood of cryptocurrency giveaway scam videos spread across the platform. Mostly, these scams are masquerading as topics related to Elon Musk, Tesla, or SpaceX. The potential for quick and easy cryptocurrency makes these a constant and disturbing threat. TikTok flooded by “Elon Musk cryptocurrency giveaway” scams. Today, the… Continue reading TikTok Flooded By Elon Musk Cryptocurrency Giveaway Scams
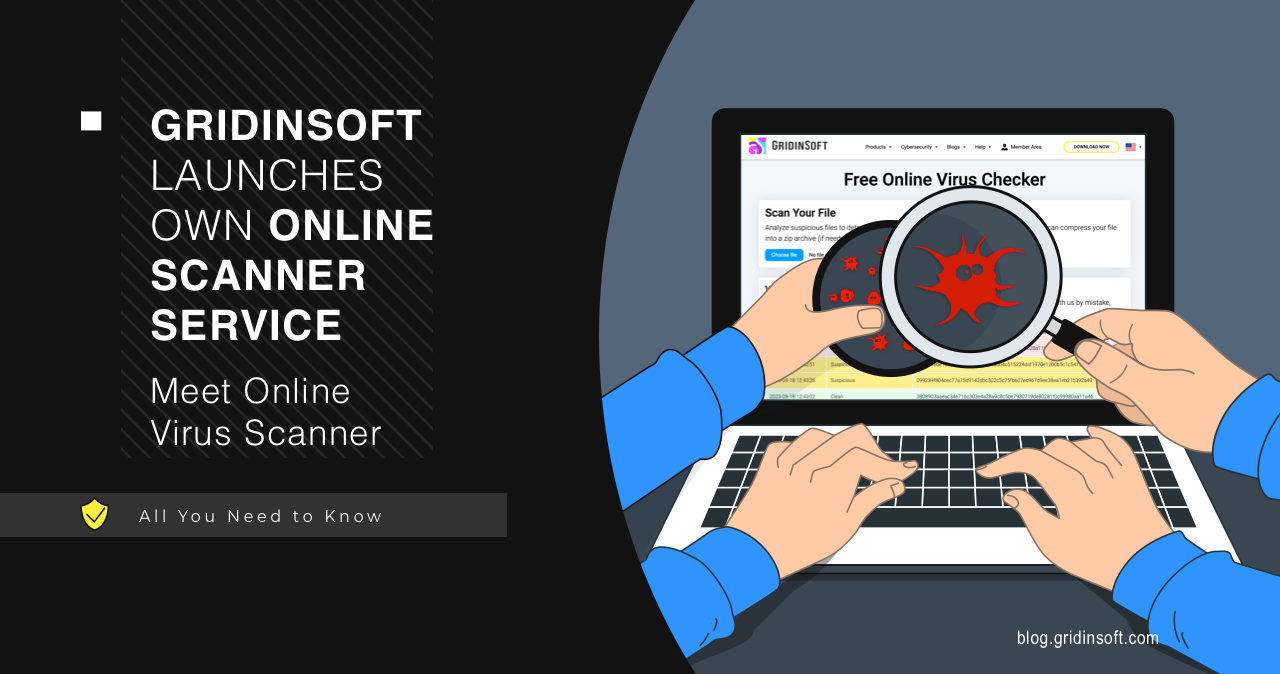
GridinSoft Launches Own Online Scanner Service – Meet Online Virus Scanner
As a part of the GridinSoft team, I am proud to announce the public release of our own online virus scanner service! Now, you can scan the file and see all the information about it for free, by using GridinSoft Online Virus Checker. Let’s check out its key features and find out why it is… Continue reading GridinSoft Launches Own Online Scanner Service – Meet Online Virus Scanner
What are Whaling Phishing Attacks?
Malicious actors know executives and high-level employees, such as public spokespersons, are familiar with common spam tactics. Due to their public profiles, they may have undergone extensive security awareness training, and the security team may have implemented stricter policies and more advanced tools to safeguard them. As a result, attackers targeting these individuals are forced… Continue reading What are Whaling Phishing Attacks?
3AM Ransomware Backs Up LockBit In Cyberattacks
Cybersecurity researchers have discovered a new family of ransomware called 3AM. Attackers attempted to use it as an alternative attack method during the failed LockBit deployment. 3AM Ransomware – The Fallback Variant of LockBit According to a recent report, cybersecurity experts have discovered a new type of ransomware known as 3AM. Since this ransomware has… Continue reading 3AM Ransomware Backs Up LockBit In Cyberattacks
What Is Identity Theft & How to Protect Against It
Identity theft is a significant issue affecting millions yearly, whether through stolen credit card information or fraudulent accounts. It’s a lucrative business for criminals, who can steal billions of dollars annually through these methods. Unfortunately, data breaches are a common occurrence, and they contribute to the problem. While it’s impossible to prevent data breaches, there… Continue reading What Is Identity Theft & How to Protect Against It
Google Fixes Critical Vulnerability in Chrome, Exploited in the Wild
Google released an urgent security update for its Chrome browser. The patch contains the fix for CVE-2023-4863, a heap buffer overflow vulnerability that can simply be exploited. Actually, Google states that this vulnerability has already been used in the wild. The breach affects browser builds for all supported OS – Mac, Linux and Windows. Google… Continue reading Google Fixes Critical Vulnerability in Chrome, Exploited in the Wild