Malicious actors know executives and high-level employees, such as public spokespersons, are familiar with common spam tactics. Due to their public profiles, they may have undergone extensive security awareness training, and the security team may have implemented stricter policies and more advanced tools to safeguard them. As a result, attackers targeting these individuals are forced to move beyond conventional phishing tactics such as Whaling Phishing and employ more sophisticated and targeted methods.
What is Whaling Phishing
Phishing is a malicious practice where attackers trick individuals into revealing sensitive information through fake emails that look legitimate. The victim willingly provides their credentials, which cannot be considered extortion or malware.
Phishing attacks, accounting for 39.6%, are the most common type of cyber attack and are frequently combined with other forms of malware such as HTML, URL, PDF, and executables.
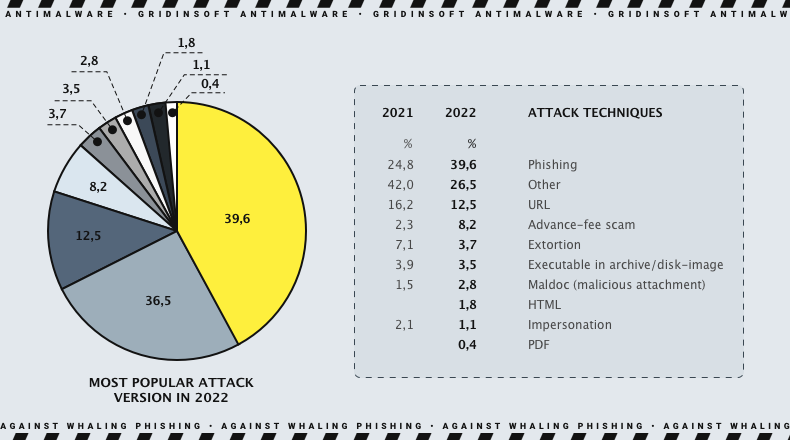
Phishing techniques are diverse, and it is nearly impossible to list them all without missing some. Nevertheless, several methods are currently the most prevalent. These methods have always been widely used due to their simplicity and the high likelihood of successfully trapping the victim.
Various types of phishing attacks include spear phishing, whaling phishing, angler phishing, pharming, pop-up phishing, and others. Spear phishing targets regular employees while whaling phishing targets high-profile employees, such as C-level executives.

Whaling Phishing Attacks
The whale is often considered the ruler of the ocean, symbolizing high authority. In the realm of phishing, ‘whale’ refers to C-level executives. These executives hold significant power within an organization, and the metaphor draws parallels between these influential individuals and the ocean’s king.
Due to their power and authority, C-level executives are targets for whaling attacks, which aim to deceive and exploit them, leveraging their access to sensitive information and decision-making abilities. When a CEO requests an urgent task from an employee, it is usually prioritized and completed quickly.
Whaling phishing is not characterized by special types of spreading. It is distributed via email, SMS, and voice like any other phishing attack. Let’s explore them through real-world examples.
Examples of Whaling Attacks
At their core, the common thread in examples of past successful whaling campaigns isn’t too dissimilar from successful phishing campaigns: The messages are seemingly so urgent, so potentially disastrous that the recipient feels compelled to act quickly, putting normal security hygiene practices by the wayside. Scammers writing successful whaling emails know their audience won’t be compelled by just a deadline reminder or a stern email from a superior. Instead, they’ll prey upon other fears, such as legal action or being the subject of reputational harm.
In one example of a whaling attempt, several executives across industries fell for an attack. They laced with accurate details about them and their businesses that purported to be from a United States District Court with a subpoena to appear before a grand jury in a civil case. The email included a link to the subpoena. When recipients clicked the link to view it, they were infected with malware instead.
Phases of Whaling Phishing Attacks
Here three phases in the phishing attack also apply to the whaling attack:
- When an attacker wants to access a system, the first step is to research the potential target. Learning about their position within the company and their relationship with other employees.
- Once the attacker has gathered enough information, they will create a customized phishing email that looks legitimate. (This is how the HR and Finance departments from Seagate and FACC Cyber Heist were deceived)
- The attacker will trick the target into clicking on a link or attachment. If the victim falls for the trick, the attacker must bypass security measures and inject a malicious payload. Then, they can steal data and sensitive information.
Defending Against Whaling Attacks
If you are an executive or someone who might be a target of whaling, you should remember the standard prevention advice for phishing attacks. It’s essential to be cautious of clicking on links or attachments in emails, as these attacks require the victim to take some action to be successful.
Implementing whaling-specific best practices can help organizations harden their defenses and educate potential targets.
It’s essential to be aware of the information public-facing employees share about executives. Whaling emails can seem more genuine if they include readily available online details. It can be birthdays, hometowns, favorite hobbies, or sports. Whaling emails can appear even more legitimate during major public events, like industry conferences or company events. Therefore, it’s essential to remind executives and spokespersons to exercise caution while checking their inboxes, particularly during high-publicity events when they are likely to be in the spotlight.





