Advanced Window Manager is potentially unwanted software that floods users’ systems with advertisements. It pretends to be a tool that adds new functionality to Windows, but in fact redirects search queries, tracks users’ internet activity, and displays advertisements. Typical distribution methods include software bundling and malvertising.
Advanced Window Manager Overview
Advanced Window Manager is an unwanted adware-like program. Despite positioning itself as a useful utility, its primary purpose is to bombard users with advertisements. The program frequently promotes fraudulent or malicious content, posing significant security risks. Clicking on any promotions displayed by Advanced Window Manager may redirect users to malicious websites that automatically download additional potentially unwanted software.

| Attribute | Details |
|---|---|
| Threat Type | Adware / PUP (Potentially Unwanted Program) |
| Detection Names | Win32/Adware.AdvancedWindowManager, PUP.Optional.WindowManager |
| Symptoms | Unwanted advertisements, browser redirects, slower system performance |
| Distribution Methods | Software bundling, malvertising, freeware downloads |
| Damage | Privacy issues, browser hijacking, exposure to malicious websites |
| Removal | Anti-malware software (recommended), manual removal possible |
Another undeclared feature is collecting information about users’ internet activity. This data includes search queries, visited URLs, geolocation data, and IP addresses, which are then sold to third parties. Advanced Window Manager is typically distributed as bundled software alongside other programs. Since this software is not particularly stealthy, users can identify its processes in Task Manager.
Detailed Analysis
Let’s analyze how Advanced Window Manager behaves in the system to understand its true nature. It arrives through an installer that precedes the original program and performs basic system checks. During installation, the unwanted software extracts the following files to a temporary folder on the system:
C:\Users\Admin\AppData\Local\Temp\7zS4E1438CD\setup_install.exe
C:\Users\Admin\AppData\Local\Temp\7zS4E1438CD\libcurlpp.dll
C:\Users\Admin\AppData\Local\Temp\7zS4E1438CD\libstdc++-6.dll
C:\Users\Admin\AppData\Local\Temp\7zS4E1438CD\libcurl.dllIt also resets some files, including:
%WINDIR%\Microsoft.NET\Framework\v4.0.30319\clr.dll
%WINDIR%\System32\rundll32.exe
C:\Users\<USER>\AppData\Local\Temp\7zSC8C4B203\metina_5.exe
C:\Users\<USER>\AppData\Local\Temp\7zSC8C4B203\metina_6.exeInstallation
Once installed, Advanced Window Manager (sample on VirusTotal) begins performing its main task – flooding the system with advertisements. It checks the following registry values, which are responsible for regionalizing the system to install more “relevant” programs:
\REGISTRY\USER\S-1-5-21-1346565761-3498240568-4147300184-1000\Control Panel\International\Geo\Nation
\REGISTRY\MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IMM\Ime File
\Registry\Machine\Software\Policies\Microsoft\System\DNSclientAfter completing this check, the malware connects to its command and control server. In our analysis, one of the requests following the initial connection installed an unwanted program called Ultra Media Burner. This behavior likely depends on the results of the aforementioned geolocation check.
GET http://limesfile.com
GET http://limesfile.com/Ea42LhC7KVL6GEpzgxwW/C_Net_8Rpjkd5GEqRYJq87/UltraMediaBurner.exe
GET http://estrix.xyz/addInstallImpression.php?key=125478824515ADNxu2ccbwe&ip=&oid=139Additional Checks & Persistence
As a typical adware specimen, Advanced Window Manager performs a series of system checks to determine the system’s location. By examining various registry keys, the malware obtains networking information. It is unlikely to implement any geofencing restrictions, as this data is primarily used to target advertisements more effectively.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Dnscache\InterfaceSpecificParameters\
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient\DnsPolicyConfigSubsequently, the malicious program modifies another set of registry keys related to Windows services and drivers. This is how it establishes persistence, adding values that associate its files with specific drivers and services in the system.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MpKsl9a97d018\Parameters
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MpKslcbc6775c\Parameters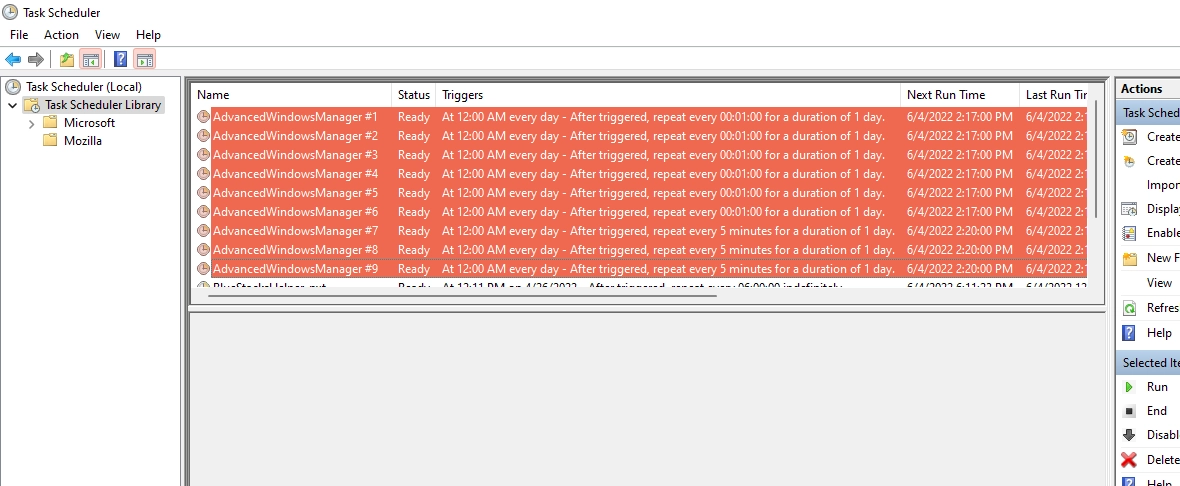
Advertising, Search Redirects and Browser Hijacking
After completing all preparations, Advanced Window Manager functions as adware or a browser hijacker. The most common scenario after installing this type of software is browser hijacking. The PUP changes the homepage and default search engine to ones it promotes (usually Bing or Yahoo). Users may also encounter lesser-known search engines like Chromstera set as the homepage or default search engine. In such cases, all queries are routed through these services, and the forced search engine change remains effective until the browser is restarted.
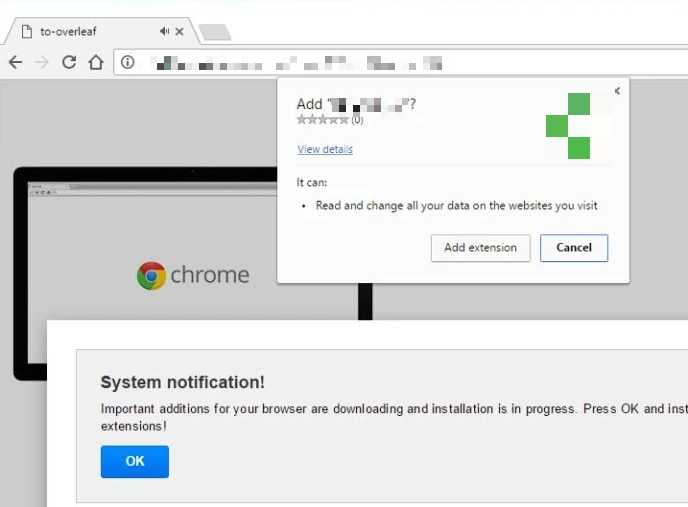
In addition to displaying irrelevant search results, the adware fills pages with advertisements and pop-ups, making web browsing extremely difficult. Another aspect of browser hijackers is collecting telemetry about users. Although such software typically does not steal passwords or other sensitive information, it redirects all search queries through its servers, thereby collecting general analytics about user behavior.
How To Remove Advanced Window Manager?
To remove Advanced Window Manager completely from your system, you’ll need to perform several steps. We recommend using specialized anti-malware software for the most thorough cleanup, but we’ve also included manual removal steps below.
Automated Removal with GridinSoft Anti-Malware
Using anti-malware software is the most reliable way to remove Advanced Window Manager and all its components. We recommend GridinSoft Anti-Malware for this task.
Step 1: Download and Install GridinSoft Anti-Malware
First, download GridinSoft Anti-Malware using the button below. Close all browsers before starting the installation process.
Step 2: Run a Full System Scan
Launch GridinSoft Anti-Malware and click on the “Scan” button to begin a comprehensive system scan. This will detect Advanced Window Manager and any other potentially unwanted applications on your system.

Step 3: Remove Detected Threats
After the scan completes, you’ll see a list of detected threats, including Advanced Window Manager components. Select all items and click the “Clean Now” button to remove them.

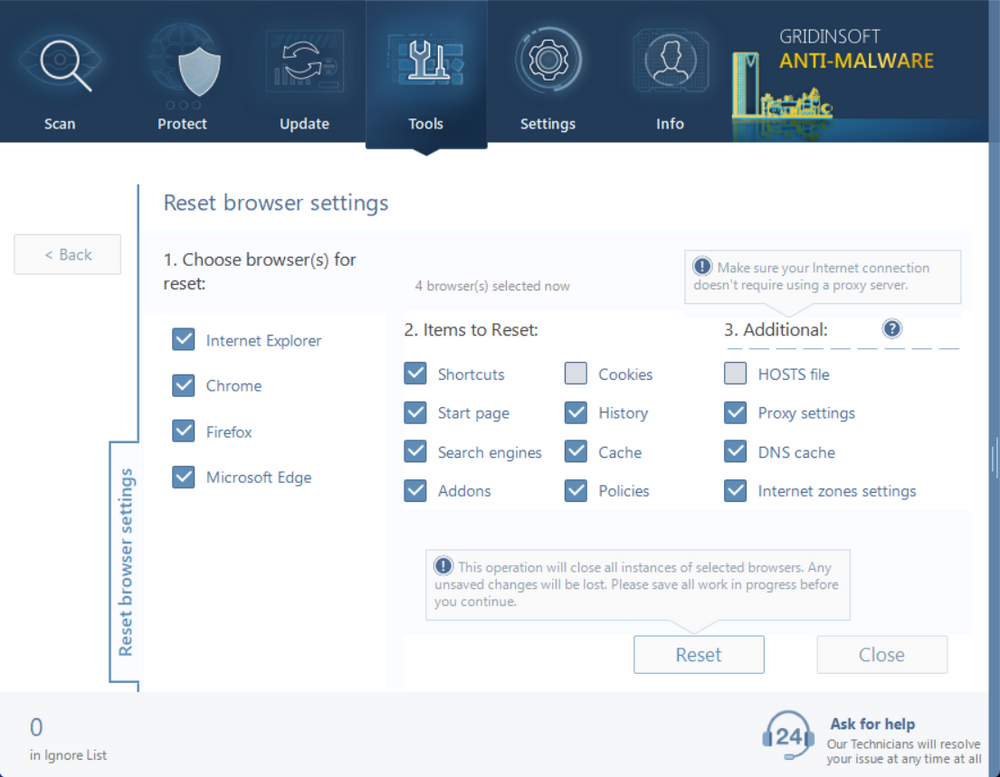
Step 4: Reset Your Browsers
To completely remove any browser modifications made by Advanced Window Manager, you should reset your browsers to their default settings. In GridinSoft Anti-Malware:
- Go to the “Tools” tab
- Select “Reset Browser Settings”
- Choose the browsers you want to reset
- Click “Reset” to restore default settings
Step 5: Enable Real-Time Protection
To prevent future infections, enable the Internet Security module in GridinSoft Anti-Malware:
- Go to the “Protect” tab
- Check the “Internet Security” option
- Click “Apply” to save changes

Manual Removal Instructions
If you prefer to remove Advanced Window Manager manually, follow these steps. However, note that manual removal is more complex and may not eliminate all components.
Step 1: Uninstall Advanced Window Manager from Control Panel
- Press Win + R, type “control panel” and press Enter
- Go to “Programs” > “Uninstall a program”
- Find “Advanced Window Manager” or any suspicious recently installed programs
- Right-click on them and select “Uninstall”
Step 2: Remove the Malicious Scheduled Tasks
- Press Win + R, type “taskschd.msc” and press Enter
- Look for tasks containing “Advanced Window Manager,” “AWM,” or suspicious random names
- Right-click on them and select “Delete”
Step 3: Reset Your Browsers
For Google Chrome:
- Open Chrome and click the three dots in the top-right corner
- Go to “Settings” > “Advanced” > “Reset and clean up”
- Click “Restore settings to their original defaults”
- Click “Reset settings” to confirm
For Mozilla Firefox:
- Open Firefox and click the three lines in the top-right corner
- Go to “Help” > “More troubleshooting information”
- Click “Refresh Firefox” in the top-right corner
- Click “Refresh Firefox” to confirm
For Microsoft Edge:
- Open Edge and click the three dots in the top-right corner
- Go to “Settings” > “Reset settings”
- Click “Restore settings to their default values”
- Click “Reset” to confirm
Frequently Asked Questions
Is Advanced Window Manager a virus?
Advanced Window Manager is not technically a virus but is classified as a potentially unwanted program (PUP) or adware. While it doesn’t typically damage your system directly like ransomware or trojans, it degrades your browsing experience, invades your privacy by tracking your online activities, and can expose you to malicious content through its advertisements. Many security products detect and flag it as a threat.
How did Advanced Window Manager get installed on my computer?
Advanced Window Manager typically enters systems through software bundling – it’s quietly included with free software downloads where users rush through installation steps without reading carefully. It may also be installed through malvertising (malicious advertisements) that trick users into clicking download buttons, or through deceptive pop-ups claiming your system needs an update or optimization. Always choose custom installation options and read each step when installing new software.
Can Advanced Window Manager steal my personal information?
While Advanced Window Manager doesn’t directly steal passwords or banking details, it does collect browsing data including search queries, websites visited, IP addresses, and geographic location. This information is typically sold to third parties for targeted advertising purposes. The program may also inject advertisements that lead to phishing sites designed to steal sensitive information. For these reasons, it’s important to remove it promptly.