PUADLManager:Win32/Sepdot is a potentially unwanted application that installs additional software. It specifically flags an application software that handles software bundling functionality. Sepdot is often packed into freeware applications or pirated software.
Potentially unwanted applications may look like less dangerous threats, but they can still create the problems. Intrusive advertisements, tracking users’ online activity, harvesting personal information – all this is among the most common symptoms. Sepdot should be removed as fast as any other thing detected by antivirus programs.
PUADLManager:Win32/Sepdot Overview
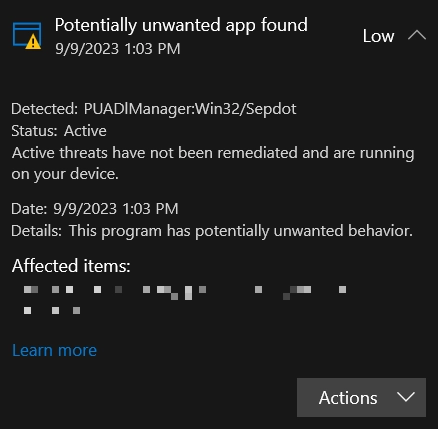
PUADLManager:Win32/Sepdot is a detection that Microsoft Defender uses to detect potentially unwanted software. As the name suggests, this unwanted application is a package installer. It is most often distributed in freeware applications or pirated software. The peculiarity of such installers is that all the processes of downloading additional software are performed in the background, without the user’s permission.
Unwanted apps that Sepdot installs can unleash a barrage of intrusive advertisements, track user’s online activity, and even harvest some personal information. Sometimes, it may offer seemingly helpful functionality, such as driver updating, system cleaning or tweaking Windows interface. However, these are mere facades with no real performance value. Having them running in the system exposes you to significant risk.
Technical Analysis
To understand how PUADLManager:Win32/Sepdot works, let’s test a sample of one on a virtual machine. This particular example is a program for downloading videos from popular online services. The functionality of Sepdot is pretty similar to other bundlers, though there are still some differences. The initial infection vector starts with the user running the infected file.
Persistence And Privilege Escalation
Sepdot creates processes and files in system directories to gain persistence and increase privileges. In particular, it drops the following files into temporary directories and directories of some programs:
%USERPROFILE%\AppData\Local\Temp\aTube_Catcher_files
%WINDIR%\Microsoft.NET\Framework\v4.0.30319\clr.dll
C:\Program Files (x86)\Google\GoogleUpdater\122.0.6234.0\updater.exe
C:\Program Files (x86)\Microsoft\Temp\EU4D43.tmp\MicrosoftEdgeUpdate.exe
In addition to these files, the malware drops many DLL files and changes certain specific registry values. Such actions allow PUADLManager:Win32/Sepdot to legitimize its presence in the system.
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\APPID\MicrosoftEdgeUpdate.exe\AppID
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\APPID\{A6B716CB-028B-404D-B72C-50E153DD68DA}\ServiceParameters
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{D1E8B1A6-32CE-443C-8E2E-EBA90C481353}\LocalizedString
Data Collection
Sepdot collects quite a lot of information about the system, particularly about the user profile, hardware configuration and Windows version. I would suppose that this is purely for fingerprinting the system.
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Display
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Lsa\FipsAlgorithmPolicy\Enabled
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SystemInformation
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\ComputerName\ActiveComputerName
The sample does not check values such as BIOS version or other low-level values, but the above registry keys provide comprehensive information about the device it is running. It does not look like VM/debugger evasion either, as the thing does not check any related registry values.
Impact
The effect on the target system is similar to other bundlers. PUADLManager:Win32/Sepdot downloads and installs various potentially unwanted programs along with the main program. Moreover, based on the collected data, this thing downloads and installs “relevant” unwanted software for the user.
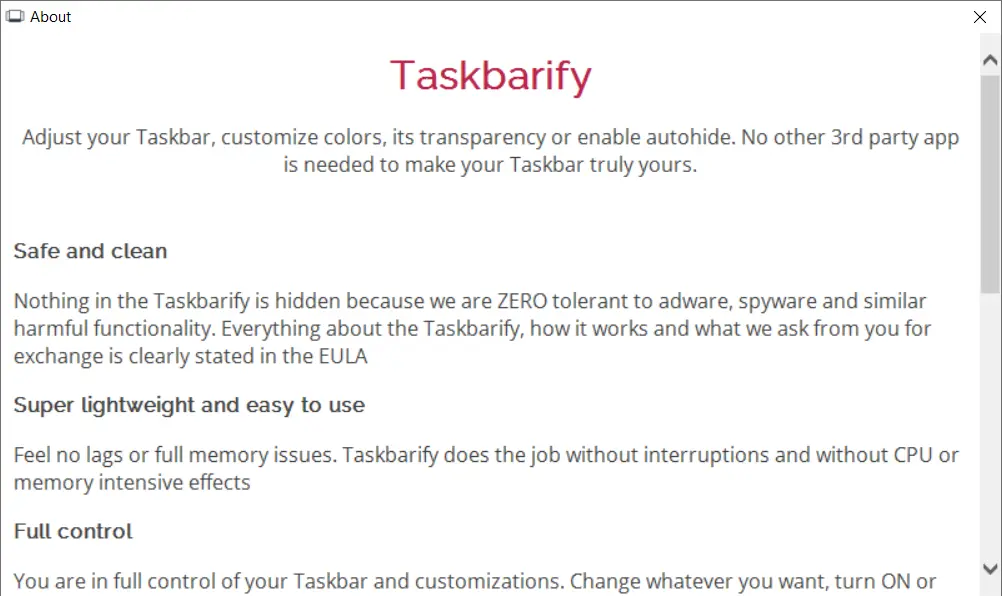
Since some services depend on geographical location, this approach allows the most favorable use of the additional software installer’s capabilities. For example, proxies allow the bypassing of regional restrictions. In suitable cases, Sepdot will install proxyware like Stopabit or Taskbarify on such a system.
In other cases, the bundler may introduce adware-like apps or rogue software (fake browsers, system cleaners, etc). Their name explain themselves pretty well, though almost all such apps will collect excessive telemetrics from the user machine.
How To Remove PUADLManager:Win32/Sepdot?
To remove PUADLManager:Win32/Sepdot, you will need an advanced anti-malware tool. GridinSoft Anti-Malware will be the best option, as it can repel with ease even those unwanted apps that other antiviruses ignore. Download Gridinsoft Anti-Malware and run a Full scan. Besides scanning, you can reset your browsers and HOSTS file in the program, which will help eliminate traces of malicious activity in a few clicks.