Smurfing, or smurf attack, is a kind of DDoS attack. It has a pretty easy mechanism, but counteracting it may be as hard as it could be with the most sophisticated types of denial attacks. Let’s check how that works, and figure out how to mirror that attack as well as decrease the chances to successfully conduct that attack.
What is a Smurf Attack?
A smurf attack is a pretty interesting type of DDoS attack. When we say “DDoS”, we usually imagine the request flooding attack. That type of threat is based on creating an enormous flow of requests, that just overloads the server. While being very easy to create, it is pretty easy to counteract. Smurf is similar to the mentioned attack type, but the channel flooding is done in a different way. The exact naming of this type of attack – smurfing – stands for the name of the malware that was first used to commit such an attack – Win32/DDoS.Smurf.
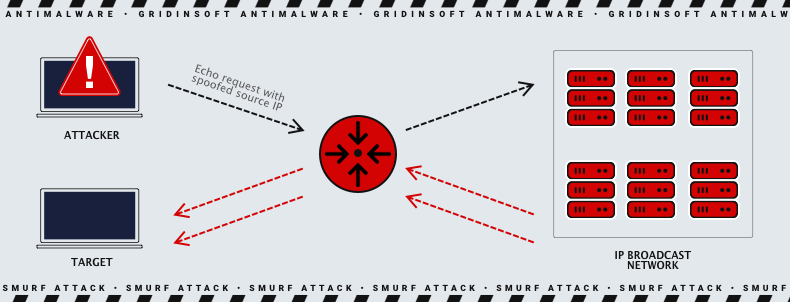
Smurf DDoS attack supposes the sending of ICMP packages to the broadband network, and rerouting the responses from all possible hosts to the target1. One computer sends a package to the network, without choosing the final host, and all present hosts start responding. The traffic created by the responses is the main danger: the network may consist of hundreds of computers. To compare with real life, it is like posting a very attractive car selling offer on dozens of websites, and specifying the phone number of a person you want to piss off. If these sites are not moderated, the victim may receive calls regarding this offer for months, until it changes the phone number. Impressive effects, isn’t it? Smurf attacks on the Internet will not lead to changing the number, but you will surely see how the network is melting under the load.
How Was the Smurf DDoS Attack Conducted?
Just as in the case of any denial attack, smurf requires a chain of computers that will conduct your requests. However, the number of computers under the attacker’s control is not the only (and the main) variable parameter. Since crooks use the broadband network as an intermediary in this attack, the efficiency of the latter depends on how big is the network where the ICMP is sent. To prevent traffic filtering by the hosts in the network, it is better to send the pings to different ones. Such a step will also make the counteraction and attack tracing much harder.
Sure, the quantitative and qualitative characteristics of the botnet play a role as well. Because the smurf attack generally aims at stand-alone servers (for example, ones that belong to small companies) rather than big online resources, there is no need to spam the requests. It is possible to do everything with a minimal amount of resources, when you know the correct settings. For example, sending bigger packages multiplied on a large network you apply as an intermediary, will quickly create a bottleneck effect and make the target server inoperable. However, it is not so easy to find such a network, so crooks usually have to be content with larger botnets and smaller package sizes.
How Dangerous is the Smurf Attack?
Just as any DDoS attack, it has a main unpleasant effect – the targeted server becomes inoperable. Since this type of cyber security attack is usually aimed against smaller but more sensible targets, such as operational servers of software vendors. Having a server knocked for these companies means the disrupted, or even paralysed workflow. Exactly, that is one of the targets of such attacks – to cause disruptions to the rivals’ infrastructure. However, that is not a single purpose.

DDoS-attack, contrary to phishing or malware spreading, is pretty easy to track. Smurfing, on the other hand, allows the crooks to use a minimal amount of things they may be traced for. With proper settings and circumstances, it may be successful even with a dozen computers involved into the attack. That may be extremely profitable for cybercriminals who use DDoS attacks as a distraction for the other action – malware injection, for example, or data exfiltration.
To perform a smurf DDoS attack, cybercriminals who manage an advanced persistent threat can use a corporate network they have already infected. Again, it is not so easy to reach the ideal environment for such an attack, but using “spare” machines crooks may cut the costs for botnet renting or establishment. While the more classic DDoS attacks from the inside may be tracked and blocked pretty easily, smurf attacks are not that easy to mirror.
How to Protect from Smurf DDoS Attacks?
Fortunately for the server maintainers and everyone involved in it, the protection from smurf attacks is not too hard to establish. The functions crooks call for are known, and they may easily be counteracted with low-to-no functionality losses. Sure, you will not shut down the DDoS attack completely, but its efficiency by best expectations will fall to 1 request per 1 attacking computer, regardless of the number of computers in the arbitrary network.
- Disable the IP-directed broadcast. The inability to route the responses to your network makes it impossible to perform such an attack. However, it may be a problem for some functionality, for example, for FTP/SFTP connections. This setup is about to be done on the router.
- Forbid the ICMP responses received. That function will filter the ICMP response packages, which are generally used in smurf attacks. Meanwhile, hackers are not obliged to use this package type, therefore this is not an ideal solution.
- Configure the firewall to filter the pings from the outside. That is the most flexible solution that can provide minimal problems in the workflow. Inability to ping your server from the outside stops the packages routing (they just arrive nowhere) and will likely stop the cybercriminals who may try to brute force your domain controller.
- More information about the smurf attacks.




