How often do we connect to free Wi-Fi networks in public places? Whether to post Instagram stories with a cup of coffee we just bought or to make edits to a project while you’re waiting for your flight. In such cases, the widespread availability of public Wi-Fi is a boon. But this general use of public Wi-Fi is also the perfect place to do hackers’ nefarious deeds. Evil Twin attack is right about that case. Read on and we’ll cover everything you need to know about evil twin attack meaning, how it works, and how to prevent it.
What is an evil twin attack? Main facts about evil twin attack definition
So, what is the best description of an evil twin? An evil twin cyber attack is a hacker attack that creates a fake Wi-Fi network that looks legitimate. However, its purpose is to steal the victims’ sensitive data. Typically, the victims of these attacks are ordinary people who connect to a free hotspot in a coffee shop or elsewhere. Evil twin attacks get their name because of their ability to mimic legitimate Wi-Fi networks to the point where they are indistinguishable from one another. Such networks share the same Service Set Identifier Name (SSID) and, quite possibly, the same Media Access Control Address (MAC).
How does an evil twin attack work?
First, the attackers position themselves near the legitimate Wi-Fi network and use their device to find out what service set ID and radio frequency the legitimate AP is using. They then send their own more powerful radio source using the same name as the legitimate AP. To the end user, the twin access point will appear legitimate. Since the attackers have the same network name and parameters as the legitimate AP, they were copied and physically positioned near the end user. Therefore, the signal is likely to be the strongest within reach.
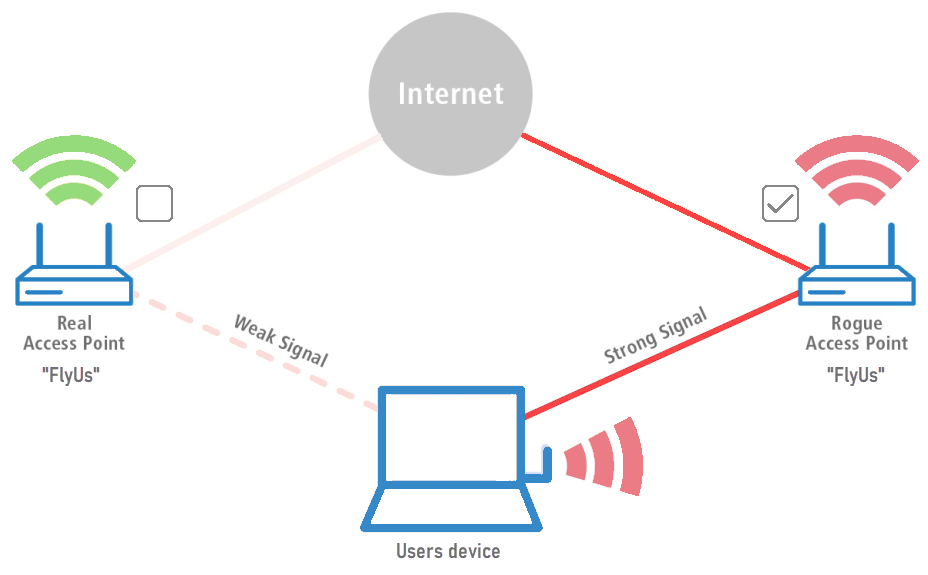
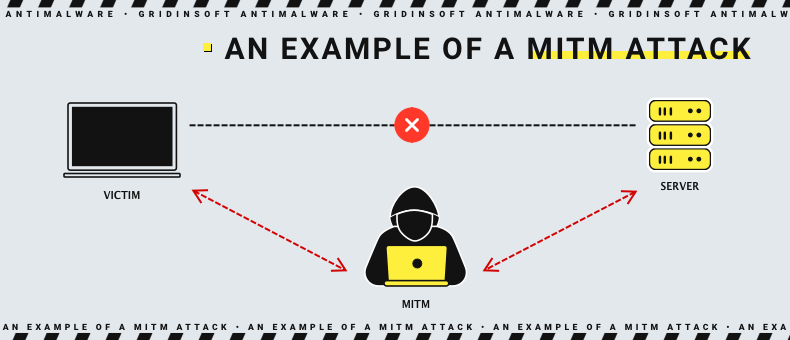
Suppose the end user manually connects to the evil twin or his computer automatically selects the fake AP. In that case, the evil twin becomes the default wireless point for his device. The attack can include a man-in-the-middle (MITM) attack. That attack allows the person who controls the access point to eavesdrop on users and steal their credentials or other sensitive information.
Finally, a fake AP can be used in a phishing scam. In this case, victims will connect to the evil twin and be redirected to the phishing site. It will then prompt them to enter their sensitive data, such as their username and password, and of course, they will be sent directly to the hacker.
What is an example of an evil twin attack?
Let’s take a look at the classic airport scheme. You can’t wait to get back online after the flight and post fresh pics of a cup of coffee in front of an airplane window. On many screens around the terminal, you see the name and password of the airport Wi-Fi SSID. Opening the Wi-Fi section on your phone, you see several Wi-Fi networks with the same name. Of course, you choose to connect to the one with the strongest signal, despite the “Unsecure” label. It is worth noting that some devices display only one access point in the list if several access points contain identical SSIDs. Everything seems okay. The network is legitimate because the password works without any problems.
However, you have just connected to an evil twin network. Using the available Wi-Fi information displayed at the airport, the hackers deployed an entire network, creating an access point with an identical SSID name and password. To achieve a strong signal and more excellent range, hackers can use Wi-Fi Pineapple, deliberately set up closer to the arrival halls. Wi-Fi Pineapple is a product of some enterprising guys who ordered a Chinese Wi-Fi router with two wireless interfaces and one wired one, wrote OpenWRT-based firmware for it and stuffed it with hacking and traffic analysis utilities. However, scammers can use almost any device, including phones, laptops, portable routers, and tablets. Through such a Wi-Fi network, an attacker can see everything you do and enter online, including information such as your bank account number and passwords.
How to protect the device from Evil Twin attacks
Evil twin attacks can be challenging to identify. However, there are a few steps you can take to keep yourself safe when connecting to public Wi-Fi networks:
Use your own access point.
The easiest way to protect yourself from this attack is to use your hotspot instead of public Wi-Fi. This ensures you’re always connected to a secure network and prevents hackers from accessing your data. Set a password to keep your hotspot private.
Don’t use unsecured Wi-Fi hotspots.
When connecting to a public network, avoid open access points marked “Unsecured.” Unprotected networks lack security features, such as traffic encryption, so evil twin networks almost always carry this designation. In addition, hackers often rely on people not paying attention and connecting to their networks, ignoring the risks.
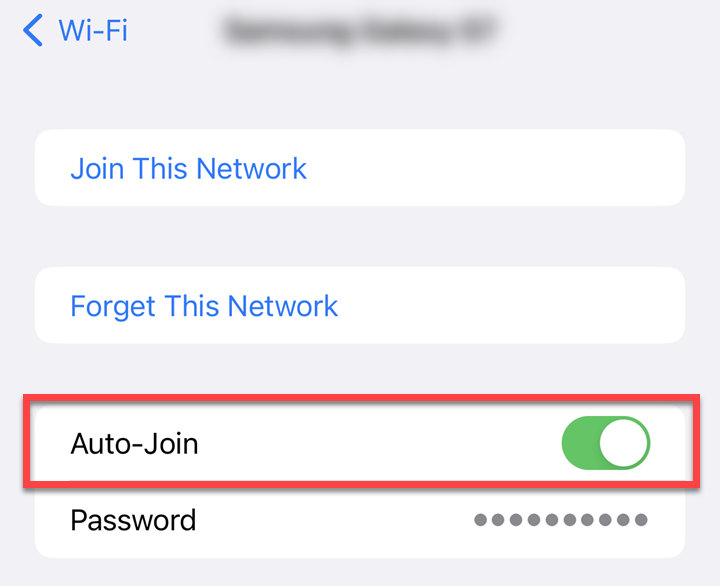
Turn off automatic connectivity.
By default, your device has auto-connect enabled. It will automatically connect to any networks you’ve used before as soon as they’re within reach. This can be dangerous, especially if you’ve unknowingly connected to a fake network in the past. Pay attention to which networks you are connecting to, and turn off the automatic connection to public networks or those you would not want to connect to automatically.
Never log in to personal accounts on a public Wi-Fi network.
You should avoid logging into personal accounts or transmitting sensitive information when using public Wi-Fi. Hackers can intercept it if you transfer it while connecting to their evil twin network. Therefore, refrain from logging into any accounts to protect your personal information. Moreover, the security settings of public networks are often subpar, as a person who does the setup may just ignore the dangers. That can lead to more sophisticated cracks, which require a different tactic to counter.
Use a VPN.
A VPN can help protect you from many attacks, including an evil twin attack, by encrypting your data before it leaves your device. When you run a VPN app, it encrypts your online activity before it’s sent to the network, preventing a hacker from reading it.
Avoid non-HTTPS websites
When using the public network and beyond, visit HTTPS websites. These sites offer end-to-end encryption that prevents hackers from tracking your activities while using them. HTTPS is a very advanced and secure version of HTTP that allows you to create many secure transactions by encrypting all communication using TLS. This helps you protect potentially sensitive information from theft.
Use two-factor authentication
Using two-factor authentication for your accounts is probably the best way to prevent hackers from accessing them. For example, suppose a hacker gained access to your account. But then, thanks to two-factor authentication, they won’t be able to log into your account because they can’t access the confirmation code.





